Get the free ACA System Security Plan Procedures, v 1.0, 08012012 - cms
Show details
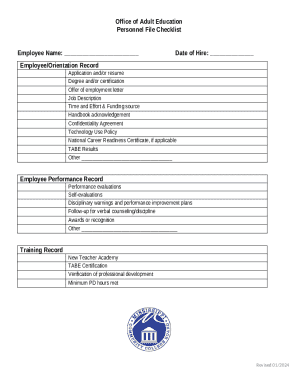
Restricted Distribution Sensitive Information For Official Use Only Centers for Medicare & Medicaid Services ACA System Security Plan Procedures Version 1.0 August 1, 2012, Restricted Distribution
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign aca system security plan

Edit your aca system security plan form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your aca system security plan form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit aca system security plan online
Use the instructions below to start using our professional PDF editor:
1
Log in to account. Click on Start Free Trial and sign up a profile if you don't have one yet.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit aca system security plan. Rearrange and rotate pages, add and edit text, and use additional tools. To save changes and return to your Dashboard, click Done. The Documents tab allows you to merge, divide, lock, or unlock files.
4
Save your file. Select it from your records list. Then, click the right toolbar and select one of the various exporting options: save in numerous formats, download as PDF, email, or cloud.
With pdfFiller, it's always easy to work with documents. Try it out!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out aca system security plan

How to fill out ACA System Security Plan:
01
Start by gathering all necessary information: Before filling out the ACA system security plan, you will need to gather information about your organization's infrastructure, systems, and processes. This may include details about your IT infrastructure, network topology, software applications, data storage practices, as well as any relevant policies and procedures.
02
Understand the applicable security requirements: Familiarize yourself with the security requirements outlined by the Affordable Care Act (ACA) and any other relevant regulatory frameworks. These requirements may cover areas such as access control, risk assessment, incident response, data protection, and security awareness training. It is important to have a clear understanding of these requirements before proceeding with the plan.
03
Identify potential security vulnerabilities: Assess your organization's systems and identify any potential security vulnerabilities that could put your sensitive data at risk. This may involve conducting risk assessments, vulnerability scans, and penetration testing. By identifying vulnerabilities, you can develop strategies to mitigate them and enhance your overall security posture.
04
Develop security controls and measures: Based on the identified vulnerabilities and the applicable security requirements, develop a set of security controls and measures that will help protect your organization's sensitive information. These controls may include implementing strong access controls, encryption of sensitive data, regular software updates and patches, network segmentation, and training employees on security best practices.
05
Document your security plan: Begin documenting your ACA system security plan, ensuring that it is comprehensive, clear, and well-organized. Include details about each security control, the rationale behind it, and any procedures or protocols that need to be followed. This documentation will serve as a guide for implementing and maintaining the security measures outlined in the plan.
06
Review and revise the plan regularly: Security threats and technologies are constantly evolving, so it is important to review and revise your ACA system security plan on a regular basis. This will help ensure that your organization remains up-to-date with the latest security best practices and can effectively address emerging threats.
Who needs an ACA System Security Plan:
01
Healthcare organizations: Healthcare organizations, including hospitals, clinics, insurance providers, and healthcare clearinghouses, are required to have an ACA system security plan. This is to safeguard the privacy and security of patient information and comply with the requirements outlined by the ACA.
02
Business associates: Business associates that work with healthcare organizations and have access to patient information are also required to have an ACA system security plan. These may include companies that provide IT services, billing and coding services, claims processing, and other healthcare-related services.
03
Government agencies: Government agencies involved in healthcare, such as state health departments and Medicare/Medicaid programs, may also need to have an ACA system security plan. This ensures that government-held healthcare data is adequately protected from unauthorized access, disclosure, and manipulation.
In summary, it is important to carefully follow the necessary steps while filling out an ACA system security plan. Gathering information, understanding security requirements, identifying vulnerabilities, developing security controls, documenting the plan, and regularly reviewing and revising it are all crucial aspects. Various stakeholders, including healthcare organizations, business associates, and government agencies, need an ACA system security plan to protect sensitive data and comply with regulatory requirements.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How do I edit aca system security plan online?
The editing procedure is simple with pdfFiller. Open your aca system security plan in the editor. You may also add photos, draw arrows and lines, insert sticky notes and text boxes, and more.
Can I sign the aca system security plan electronically in Chrome?
You certainly can. You get not just a feature-rich PDF editor and fillable form builder with pdfFiller, but also a robust e-signature solution that you can add right to your Chrome browser. You may use our addon to produce a legally enforceable eSignature by typing, sketching, or photographing your signature with your webcam. Choose your preferred method and eSign your aca system security plan in minutes.
How do I fill out aca system security plan using my mobile device?
On your mobile device, use the pdfFiller mobile app to complete and sign aca system security plan. Visit our website (https://edit-pdf-ios-android.pdffiller.com/) to discover more about our mobile applications, the features you'll have access to, and how to get started.
What is aca system security plan?
An ACA System Security Plan is a document that outlines the security measures and protocols in place to protect the Affordable Care Act (ACA) systems and data.
Who is required to file aca system security plan?
Entities and organizations that have access to ACA systems or handle ACA data are required to file an ACA System Security Plan.
How to fill out aca system security plan?
To fill out an ACA System Security Plan, entities must provide detailed information about their security measures, policies, and procedures for protecting ACA systems and data.
What is the purpose of aca system security plan?
The purpose of an ACA System Security Plan is to ensure that entities handling ACA data have adequate security measures in place to protect the confidentiality, integrity, and availability of the data.
What information must be reported on aca system security plan?
Information that must be reported on an ACA System Security Plan includes security controls, risk assessments, incident response procedures, and system monitoring practices.
Fill out your aca system security plan online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Aca System Security Plan is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.