Get the free Private Security Compliance Monitoring - Texas Department of ... - dps texas
Show details
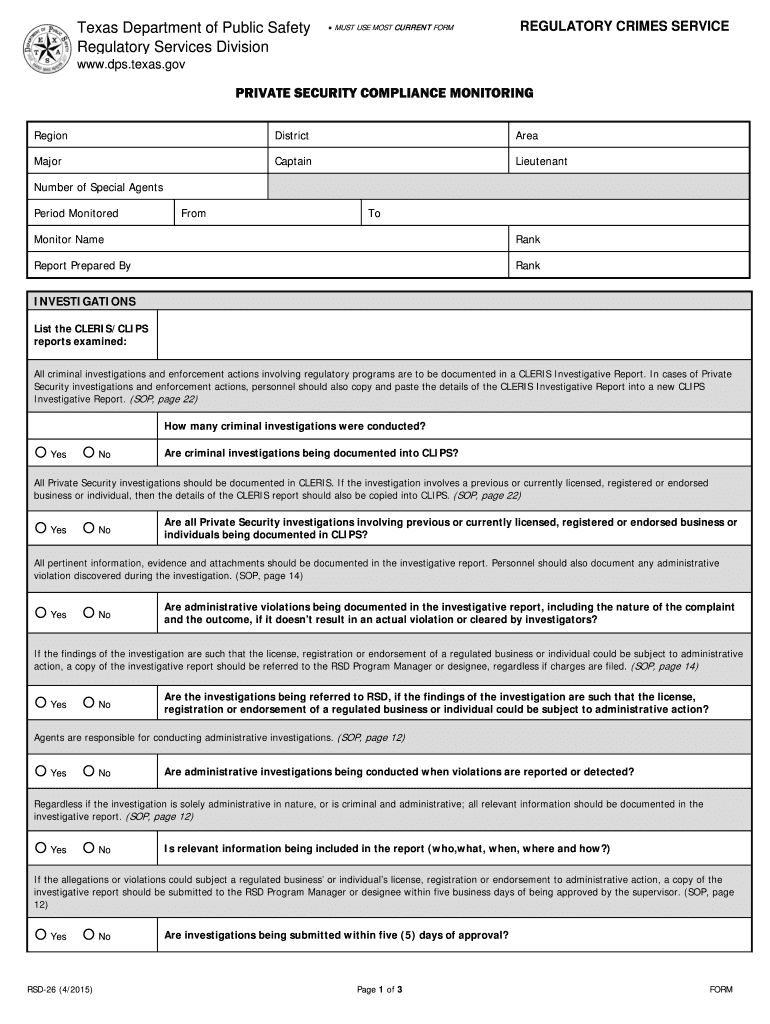
Texas Department of Public Safety MUST USE MOST CURRENT FORM ... submitted within five (5) days of approval? RSD-26 (4/2015). Page 1 of 3. FORM ...
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign private security compliance monitoring

Edit your private security compliance monitoring form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your private security compliance monitoring form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing private security compliance monitoring online
In order to make advantage of the professional PDF editor, follow these steps:
1
Log in to your account. Start Free Trial and sign up a profile if you don't have one.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit private security compliance monitoring. Add and replace text, insert new objects, rearrange pages, add watermarks and page numbers, and more. Click Done when you are finished editing and go to the Documents tab to merge, split, lock or unlock the file.
4
Get your file. Select your file from the documents list and pick your export method. You may save it as a PDF, email it, or upload it to the cloud.
Dealing with documents is simple using pdfFiller. Try it now!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out private security compliance monitoring

How to fill out private security compliance monitoring:
01
Gather all relevant information: Start by gathering all the necessary information related to private security compliance. This may include regulations, policies, procedures, and any other documentation that needs to be followed.
02
Identify the scope: Determine the scope of your private security compliance monitoring. Define the areas or aspects that you need to focus on and ensure that they align with the regulations and requirements.
03
Assign responsibilities: Clearly define and assign the responsibilities for monitoring and ensuring compliance. Identify the individuals or teams responsible for specific tasks, such as conducting inspections, reviewing documentation, and reporting any non-compliance issues.
04
Create a monitoring plan: Develop a comprehensive plan for monitoring private security compliance. This plan should outline the methods, frequency, and procedures for conducting compliance checks, audits, and inspections. Consider utilizing automated tools or software to streamline the process.
05
Conduct regular inspections: Regularly inspect the security measures in place to ensure they meet compliance standards. This may include physical inspections of security systems, access controls, surveillance equipment, and other relevant aspects.
06
Review documentation: Review and update all relevant documentation regularly. This may include policies, procedures, incident reports, training records, and security logs. Make sure that any changes or updates in regulations are reflected in your documentation.
07
Identify and report non-compliance: If any non-compliance issues are identified during the monitoring process, they should be promptly addressed and reported. Establish a clear reporting system for identifying, documenting, and resolving non-compliance issues.
Who needs private security compliance monitoring?
01
Organizations: Private sector organizations across various industries that deal with sensitive information, valuable assets, or have security responsibilities require private security compliance monitoring. This may include financial institutions, healthcare facilities, transportation companies, data centers, and more.
02
Government Agencies: Government agencies responsible for national security, critical infrastructure protection, defense, or law enforcement also require private security compliance monitoring. These agencies often have regulations in place that organizations must comply with to ensure the security and protection of sensitive information or critical assets.
03
Service Providers: Private security compliance monitoring is necessary for security service providers who offer services such as security guard services, alarm system monitoring, surveillance system installation, or cybersecurity services. These providers need to adhere to industry and regulatory standards to ensure the safety and security of their clients.
In conclusion, filling out private security compliance monitoring involves gathering relevant information, identifying the scope, assigning responsibilities, creating a monitoring plan, conducting inspections, reviewing documentation, and reporting non-compliance issues. Private security compliance monitoring is needed by organizations, government agencies, and service providers to ensure compliance with security regulations and standards.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I get private security compliance monitoring?
With pdfFiller, an all-in-one online tool for professional document management, it's easy to fill out documents. Over 25 million fillable forms are available on our website, and you can find the private security compliance monitoring in a matter of seconds. Open it right away and start making it your own with help from advanced editing tools.
How do I complete private security compliance monitoring online?
Filling out and eSigning private security compliance monitoring is now simple. The solution allows you to change and reorganize PDF text, add fillable fields, and eSign the document. Start a free trial of pdfFiller, the best document editing solution.
Can I edit private security compliance monitoring on an iOS device?
Create, modify, and share private security compliance monitoring using the pdfFiller iOS app. Easy to install from the Apple Store. You may sign up for a free trial and then purchase a membership.
What is private security compliance monitoring?
Private security compliance monitoring involves monitoring and ensuring that private security companies are in compliance with relevant laws, regulations, and industry standards.
Who is required to file private security compliance monitoring?
Private security companies are required to file private security compliance monitoring to demonstrate that they are meeting all necessary requirements.
How to fill out private security compliance monitoring?
Private security compliance monitoring can be filled out by providing detailed information about the company's security practices, training programs, employee background checks, and other relevant details.
What is the purpose of private security compliance monitoring?
The purpose of private security compliance monitoring is to ensure that private security companies are operating in a legal and ethical manner, providing a safe environment for their clients and employees.
What information must be reported on private security compliance monitoring?
Information that must be reported on private security compliance monitoring includes security policies, procedures, incident reports, training records, and employee certifications.
Fill out your private security compliance monitoring online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Private Security Compliance Monitoring is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.


















