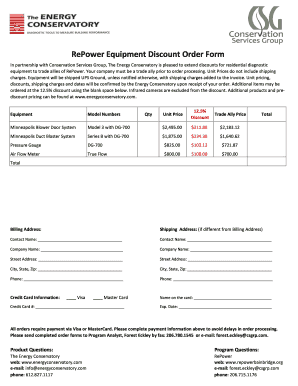
Get the free Security Consulting and Analysis - Sept06 - suffolk va
Show details
August 22, 2006, REQUEST FOR PROPOSAL Security Consulting and Analysis Services The City of Suffolk will accept sealed proposals from qualified persons/ firms until 2:00 p.m., local time, Wednesday,
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign security consulting and analysis

Edit your security consulting and analysis form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your security consulting and analysis form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit security consulting and analysis online
To use our professional PDF editor, follow these steps:
1
Register the account. Begin by clicking Start Free Trial and create a profile if you are a new user.
2
Prepare a file. Use the Add New button. Then upload your file to the system from your device, importing it from internal mail, the cloud, or by adding its URL.
3
Edit security consulting and analysis. Rearrange and rotate pages, add and edit text, and use additional tools. To save changes and return to your Dashboard, click Done. The Documents tab allows you to merge, divide, lock, or unlock files.
4
Get your file. When you find your file in the docs list, click on its name and choose how you want to save it. To get the PDF, you can save it, send an email with it, or move it to the cloud.
pdfFiller makes dealing with documents a breeze. Create an account to find out!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out security consulting and analysis

How to fill out security consulting and analysis:
01
Identify your organization's security goals and objectives. Determine what areas of your company's security infrastructure require evaluation and improvement.
02
Assess the current security measures in place. Conduct a comprehensive review of your organization's security protocols, systems, and policies to identify any vulnerabilities or gaps that may exist.
03
Conduct a risk assessment. Identify potential risks and threats to your organization's security, both internal and external. This step involves evaluating the potential impact and likelihood of each risk.
04
Develop a security plan. Based on the findings from the risk assessment, formulate a strategic plan to mitigate identified risks and enhance overall security. This plan should include specific action steps, timelines, and responsible parties.
05
Implement the security plan. Take necessary steps to put the security plan into action, including implementing security controls and measures, updating policies and procedures, and training employees on security best practices.
06
Regularly monitor and evaluate security measures. Continuously monitor the effectiveness of implemented security measures. Regularly review and update security policies and protocols to adapt to changing threats and vulnerabilities.
07
Seek professional assistance if needed. Consider engaging the services of a security consulting firm or expert to aid in the analysis and development of your security plan. Their expertise and experience can provide valuable insights and guidance.
08
Conduct regular audits and assessments. Perform periodic audits and assessments to ensure ongoing compliance with security standards and regulatory requirements.
09
Continuously educate and train employees. Security is a shared responsibility. Provide ongoing training and education to employees to raise awareness about security risks, promote best practices, and ensure their active participation in maintaining a secure environment.
10
Stay up-to-date with industry trends and advancements. Keep abreast of emerging threats, new technologies, and industry best practices to continuously enhance your security consulting and analysis efforts.
Who needs security consulting and analysis:
01
Businesses of all sizes and industries can benefit from security consulting and analysis. From small startups to large corporations, every organization faces various security risks that need to be addressed.
02
Government agencies and institutions often deal with sensitive information and assets, making security consulting and analysis essential to protect against cyber threats and unauthorized access.
03
Non-profit organizations and charitable institutions can also benefit from security consulting and analysis to safeguard donors' personal information and maintain the trust of their supporters.
04
Healthcare organizations, including hospitals, clinics, and private practices, store vast amounts of sensitive patient data that requires robust security measures and regular analysis to ensure compliance with privacy regulations.
05
Financial institutions, such as banks, credit unions, and investment firms, handle highly sensitive customer financial data, making security consulting and analysis crucial to protect against fraud and cyber attacks.
06
Educational institutions, including schools, colleges, and universities, hold confidential student records and research data that need to be safeguarded from unauthorized access or data breaches.
07
Retailers and e-commerce businesses face the risk of payment fraud, data breaches, and theft of customer information, highlighting the need for security consulting and analysis to protect customer data and maintain business continuity.
08
Critical infrastructure facilities, including power plants, water treatment facilities, and transportation networks, require security consulting and analysis to protect against physical and cyber threats that could have far-reaching consequences.
09
Legal firms and professional services companies often handle sensitive client information and intellectual property, necessitating security consulting and analysis to protect client confidentiality and prevent data breaches.
10
Individuals and households can also benefit from security consulting and analysis to protect personal information, secure home networks, and ensure overall safety and privacy.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is security consulting and analysis?
Security consulting and analysis involves assessing security risks, identifying vulnerabilities, and recommending strategies to improve security measures.
Who is required to file security consulting and analysis?
Businesses and organizations in certain industries, especially those dealing with sensitive information or assets, are usually required to conduct security consulting and analysis.
How to fill out security consulting and analysis?
Security consulting and analysis reports are typically filled out by trained professionals who specialize in security assessments. The reports should include a detailed analysis of security vulnerabilities and recommended solutions.
What is the purpose of security consulting and analysis?
The purpose of security consulting and analysis is to help organizations identify and mitigate security risks, protect their assets and information, and improve overall security posture.
What information must be reported on security consulting and analysis?
The report should include an assessment of current security measures, identified vulnerabilities, recommended security improvements, and a plan for implementation.
Can I sign the security consulting and analysis electronically in Chrome?
Yes. You can use pdfFiller to sign documents and use all of the features of the PDF editor in one place if you add this solution to Chrome. In order to use the extension, you can draw or write an electronic signature. You can also upload a picture of your handwritten signature. There is no need to worry about how long it takes to sign your security consulting and analysis.
How do I edit security consulting and analysis on an Android device?
Yes, you can. With the pdfFiller mobile app for Android, you can edit, sign, and share security consulting and analysis on your mobile device from any location; only an internet connection is needed. Get the app and start to streamline your document workflow from anywhere.
How do I complete security consulting and analysis on an Android device?
On an Android device, use the pdfFiller mobile app to finish your security consulting and analysis. The program allows you to execute all necessary document management operations, such as adding, editing, and removing text, signing, annotating, and more. You only need a smartphone and an internet connection.
Fill out your security consulting and analysis online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Security Consulting And Analysis is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.