Get the free SECURITY PENETRATION TESTING - doit maryland
Show details
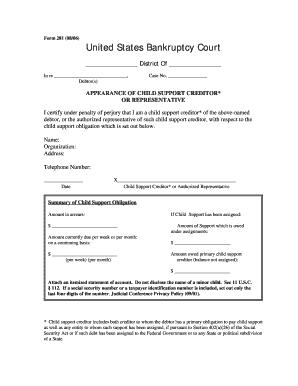
CERTIFICATION REGARDING INVESTMENTS IN IRAN i it is not identified on the list created by the Board of Public Works as a person engaging in investment activities in Iran as described in 17-702 of State Finance Procurement and ii it is not engaging in investment activities in Iran as described in State Finance Procurement Article 17-702. Personally Identifiable Information PII Any information about an individual maintained by the State including 1 any information that can be used to...
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign security penetration testing

Edit your security penetration testing form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your security penetration testing form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit security penetration testing online
Follow the guidelines below to use a professional PDF editor:
1
Register the account. Begin by clicking Start Free Trial and create a profile if you are a new user.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit security penetration testing. Rearrange and rotate pages, add and edit text, and use additional tools. To save changes and return to your Dashboard, click Done. The Documents tab allows you to merge, divide, lock, or unlock files.
4
Save your file. Select it in the list of your records. Then, move the cursor to the right toolbar and choose one of the available exporting methods: save it in multiple formats, download it as a PDF, send it by email, or store it in the cloud.
Dealing with documents is simple using pdfFiller. Now is the time to try it!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out security penetration testing

How to fill out security penetration testing
01
Start by understanding the purpose of security penetration testing. It is essential to identify potential vulnerabilities and weaknesses in a system.
02
Define the scope of the security penetration testing. Determine which aspects of the system will be tested and establish clear goals.
03
Conduct thorough research on the system to be tested. Gather all available information on the architecture, technologies, and potential vulnerabilities.
04
Identify the appropriate tools and methodologies to use during the penetration testing process. Choose tools that align with the system's technologies and potential vulnerabilities.
05
Create a detailed plan for security penetration testing. Include step-by-step instructions on how to perform the testing, the expected timeline, and any specific objectives.
06
Obtain authorization and permissions from relevant stakeholders before conducting security penetration testing. Ensure that all legal and ethical guidelines are followed.
07
Perform the security penetration testing according to the plan. Use the selected tools and methodologies to identify vulnerabilities and exploit them if necessary.
08
Document all findings and vulnerabilities discovered during the testing process. Include clear descriptions, severity levels, and recommendations for mitigation.
09
Prepare a comprehensive report that summarizes the security penetration testing process, findings, and recommendations. Make sure the report is accessible and understandable to both technical and non-technical stakeholders.
10
Implement the recommended solutions and fixes to address the identified vulnerabilities. Follow best practices and security guidelines to strengthen the system's overall security posture.
11
Regularly repeat security penetration testing to ensure that new vulnerabilities are not introduced and to validate the effectiveness of implemented security measures.
Who needs security penetration testing?
01
Organizations that handle sensitive customer data, such as financial institutions, healthcare providers, and e-commerce platforms, need security penetration testing to safeguard confidential information.
02
Companies that develop software, applications, or websites need security penetration testing to identify and eliminate potential vulnerabilities that could be exploited by hackers.
03
Government agencies and organizations dealing with national security or critical infrastructure must conduct security penetration testing to protect against cyber threats and attacks.
04
Any organization that wants to ensure the security of its network, systems, and applications can benefit from security penetration testing.
05
Startups and small businesses can also benefit from security penetration testing, as it helps identify vulnerabilities before they are exploited by cybercriminals.
06
Companies that have experienced previous security breaches or incidents may require security penetration testing to assess their systems' current vulnerabilities and prevent future compromises.
07
Companies that need to comply with industry standards and regulations, such as PCI DSS or HIPAA, often require security penetration testing to meet the necessary criteria.
08
Organizations that value their reputation and customer trust understand the importance of security penetration testing as a proactive measure to prevent potential data breaches.
09
Software developers who want to improve the security of their code and ensure that their applications are resilient against attacks can benefit from security penetration testing.
10
Organizations that want to stay ahead of emerging security threats and trends can use security penetration testing to validate their security measures and identify any gaps.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I manage my security penetration testing directly from Gmail?
The pdfFiller Gmail add-on lets you create, modify, fill out, and sign security penetration testing and other documents directly in your email. Click here to get pdfFiller for Gmail. Eliminate tedious procedures and handle papers and eSignatures easily.
How can I get security penetration testing?
It's simple using pdfFiller, an online document management tool. Use our huge online form collection (over 25M fillable forms) to quickly discover the security penetration testing. Open it immediately and start altering it with sophisticated capabilities.
Can I edit security penetration testing on an iOS device?
Yes, you can. With the pdfFiller mobile app, you can instantly edit, share, and sign security penetration testing on your iOS device. Get it at the Apple Store and install it in seconds. The application is free, but you will have to create an account to purchase a subscription or activate a free trial.
What is security penetration testing?
Security penetration testing is a method used to evaluate the security of a system by simulating an attack from a malicious hacker.
Who is required to file security penetration testing?
Organizations that handle sensitive information or have critical infrastructure are typically required to conduct and file security penetration testing.
How to fill out security penetration testing?
Security penetration testing can be filled out by hiring a third-party cybersecurity firm to conduct the tests and provide a report.
What is the purpose of security penetration testing?
The purpose of security penetration testing is to identify vulnerabilities in a system before they can be exploited by malicious actors.
What information must be reported on security penetration testing?
The report should include details of the vulnerabilities found, the methodology used, and recommendations for remediation.
Fill out your security penetration testing online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Security Penetration Testing is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.