Get the free Chronology of Data Breaches Custom Sort - Retired Public Safety.com
Show details
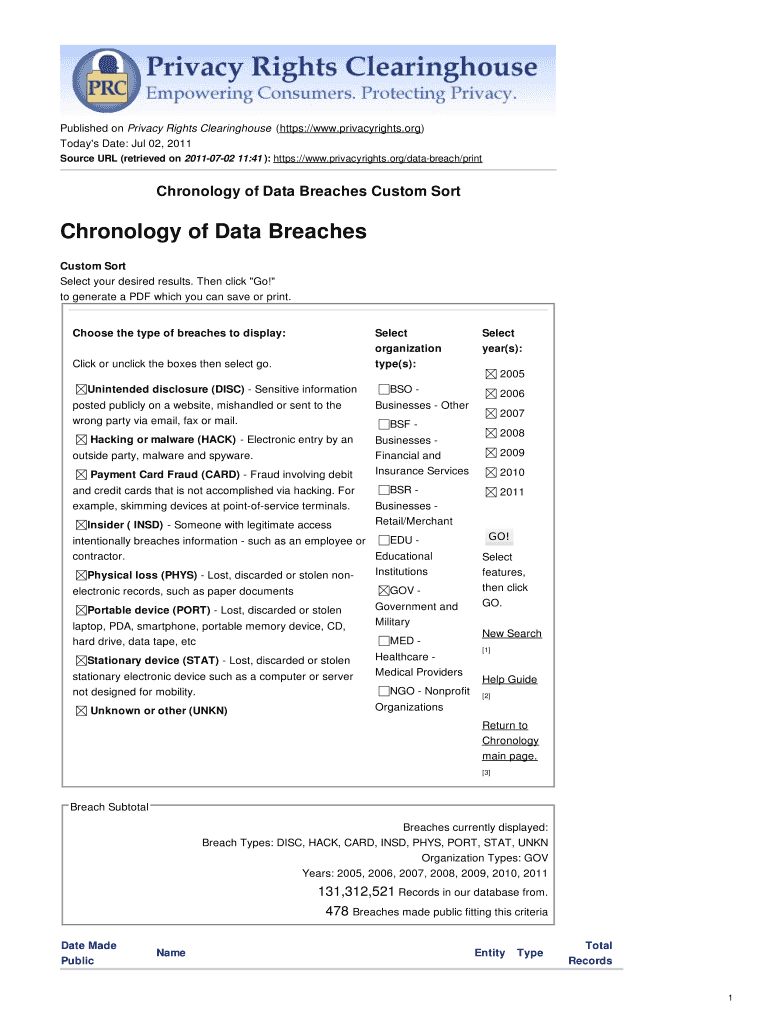
Published on Privacy Rights Clearinghouse (https://www.privacyrights.org) Today's Date: Jul 02, 2011 Source URL (retrieved on 2011-07-02 11:41): https://www.privacyrights.org/data-breach/print Chronology
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign chronology of data breaches

Edit your chronology of data breaches form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your chronology of data breaches form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing chronology of data breaches online
Follow the steps below to benefit from a competent PDF editor:
1
Check your account. If you don't have a profile yet, click Start Free Trial and sign up for one.
2
Upload a file. Select Add New on your Dashboard and upload a file from your device or import it from the cloud, online, or internal mail. Then click Edit.
3
Edit chronology of data breaches. Replace text, adding objects, rearranging pages, and more. Then select the Documents tab to combine, divide, lock or unlock the file.
4
Save your file. Select it from your list of records. Then, move your cursor to the right toolbar and choose one of the exporting options. You can save it in multiple formats, download it as a PDF, send it by email, or store it in the cloud, among other things.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out chronology of data breaches

How to Fill Out Chronology of Data Breaches:
01
Gather Information: Start by collecting all relevant information about each data breach, including the date, type of breach, affected parties, and any actions taken in response. This could include reviewing incident reports, conducting interviews, and consulting with IT and security teams.
02
Organize by Date: Arrange the data breaches in chronological order, starting from the earliest incident to the most recent. This allows for a clear timeline visualization of the breaches, which can be helpful for analysis and identification of patterns or trends.
03
Include Key Details: For each data breach, ensure that you include essential details such as the name of the breached organization, the nature of the breach (e.g., malware attack, unauthorized access), the potential impact (e.g., stolen personal data, financial loss), and any notable actions or investigations that followed.
04
Document Remediation Efforts: It is important to document any steps taken by the organization to mitigate the impact of each data breach. This can include activities such as conducting forensic analysis, notifying affected individuals, implementing additional security measures, or cooperating with law enforcement agencies.
05
Include Lessons Learned: As you fill out the chronology, it is valuable to note any lessons learned from each data breach. This could involve identifying vulnerabilities in security systems, improving incident response protocols, or implementing preventive measures to avoid similar breaches in the future.
Who Needs Chronology of Data Breaches?
01
Organizations: Companies and institutions can benefit from maintaining a chronology of data breaches to understand their own security history, identify weaknesses, and ensure that appropriate measures are in place to prevent similar incidents.
02
Regulatory Bodies: Government agencies and industry regulators may require access to an organization's chronology of data breaches to assess compliance with relevant laws and regulations. This information helps them evaluate an organization's security practices and enforce necessary actions if needed.
03
Security Professionals: Cybersecurity experts and IT teams use data breach chronologies to analyze past incidents, identify trends, and develop more effective strategies and countermeasures to secure sensitive data and prevent future breaches.
04
Legal Entities: In case of legal actions or disputes, a chronology of data breaches can be a crucial document for demonstrating a pattern of negligence, breach of contract, or violations of privacy laws. It provides evidence that can support legal claims or defenses.
05
Public Awareness: Transparency is important to build trust with stakeholders and the public. Organizations that share their data breach chronology with the public demonstrate accountability, enabling affected individuals or customers to take necessary precautions and make informed decisions regarding their personal information.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I send chronology of data breaches to be eSigned by others?
Once you are ready to share your chronology of data breaches, you can easily send it to others and get the eSigned document back just as quickly. Share your PDF by email, fax, text message, or USPS mail, or notarize it online. You can do all of this without ever leaving your account.
How can I get chronology of data breaches?
It's simple with pdfFiller, a full online document management tool. Access our huge online form collection (over 25M fillable forms are accessible) and find the chronology of data breaches in seconds. Open it immediately and begin modifying it with powerful editing options.
How do I edit chronology of data breaches online?
The editing procedure is simple with pdfFiller. Open your chronology of data breaches in the editor, which is quite user-friendly. You may use it to blackout, redact, write, and erase text, add photos, draw arrows and lines, set sticky notes and text boxes, and much more.
What is chronology of data breaches?
The chronology of data breaches is a timeline documenting the dates and details of data breaches that have occurred.
Who is required to file chronology of data breaches?
Entities or organizations that have experienced a data breach are required to file a chronology of data breaches.
How to fill out chronology of data breaches?
The chronology of data breaches can be filled out by providing information such as the date of the breach, how it occurred, what data was affected, and the steps taken to address the breach.
What is the purpose of chronology of data breaches?
The purpose of the chronology of data breaches is to provide a detailed record of data breaches for regulatory compliance and transparency.
What information must be reported on chronology of data breaches?
The information that must be reported on the chronology of data breaches includes the date of the breach, how it occurred, what data was affected, and the steps taken to address the breach.
Fill out your chronology of data breaches online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Chronology Of Data Breaches is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.



















