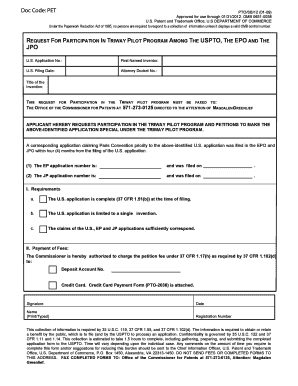
Get the free Chronology of Data Breaches Custom Sort - education new york bb
Show details
Published on Privacy Rights Clearinghouse (ht t p://www.privacyright s.org) Today's Date: Dec 06, 2013Chronology of Data Breaches Custom SortChronology of Data Breaches Custom So rt Select your desired
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign chronology of data breaches

Edit your chronology of data breaches form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your chronology of data breaches form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing chronology of data breaches online
Follow the steps down below to benefit from a competent PDF editor:
1
Log in. Click Start Free Trial and create a profile if necessary.
2
Upload a file. Select Add New on your Dashboard and upload a file from your device or import it from the cloud, online, or internal mail. Then click Edit.
3
Edit chronology of data breaches. Rearrange and rotate pages, insert new and alter existing texts, add new objects, and take advantage of other helpful tools. Click Done to apply changes and return to your Dashboard. Go to the Documents tab to access merging, splitting, locking, or unlocking functions.
4
Get your file. Select the name of your file in the docs list and choose your preferred exporting method. You can download it as a PDF, save it in another format, send it by email, or transfer it to the cloud.
It's easier to work with documents with pdfFiller than you could have believed. You can sign up for an account to see for yourself.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out chronology of data breaches

How to fill out chronology of data breaches:
01
Start by gathering all available information regarding the data breaches. This includes the date of the breach, the affected organization, the type of data compromised, and any other relevant details.
02
Organize the information in a systematic manner. You can choose to use a spreadsheet or a chronological list format, whichever suits your preferences. Include columns or sections for each piece of information to ensure clarity.
03
Begin with the earliest known data breach and then proceed chronologically, adding each subsequent breach to the list. Make sure to include any updates or additional information as it becomes available.
04
Be thorough and accurate when recording the details of each breach. Include any known impacts or consequences, the actions taken by the affected organization in response, and any relevant legal or regulatory implications.
05
Regularly update the chronology as new breaches occur or as more information about existing breaches is discovered. It is crucial to keep the chronology up-to-date to ensure its usefulness as a reference tool.
Who needs chronology of data breaches:
01
Organizations and businesses: They can benefit from maintaining a chronology of data breaches to track the changing patterns and trends in cybersecurity threats. It helps them understand the risks and take proactive measures to strengthen their defenses.
02
Regulatory bodies and policymakers: By having access to a comprehensive chronology of data breaches, regulatory bodies and policymakers can identify recurring vulnerabilities or systemic weaknesses in cybersecurity practices. This information can then be used to shape regulations and policies that better protect individuals and organizations.
03
Researchers and analysts: Studying the chronology of data breaches can provide valuable insights into the evolving nature of cyber threats. Researchers can analyze patterns, identify common vulnerabilities, and propose countermeasures to mitigate future breaches.
04
Individuals: Being aware of the chronology of data breaches can help individuals assess the potential risks associated with sharing personal information and taking necessary precautions to protect themselves. It allows them to make informed decisions regarding their online activities and privacy.
In summary, filling out a chronology of data breaches requires gathering and organizing the relevant information in a systematic manner. This tool is beneficial for organizations, regulatory bodies, researchers, analysts, and individuals alike, having various purposes like monitoring trends, shaping policies, conducting research, and enhancing personal cybersecurity.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I send chronology of data breaches for eSignature?
Once you are ready to share your chronology of data breaches, you can easily send it to others and get the eSigned document back just as quickly. Share your PDF by email, fax, text message, or USPS mail, or notarize it online. You can do all of this without ever leaving your account.
How do I edit chronology of data breaches online?
With pdfFiller, you may not only alter the content but also rearrange the pages. Upload your chronology of data breaches and modify it with a few clicks. The editor lets you add photos, sticky notes, text boxes, and more to PDFs.
How do I edit chronology of data breaches on an iOS device?
You certainly can. You can quickly edit, distribute, and sign chronology of data breaches on your iOS device with the pdfFiller mobile app. Purchase it from the Apple Store and install it in seconds. The program is free, but in order to purchase a subscription or activate a free trial, you must first establish an account.
Fill out your chronology of data breaches online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Chronology Of Data Breaches is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.