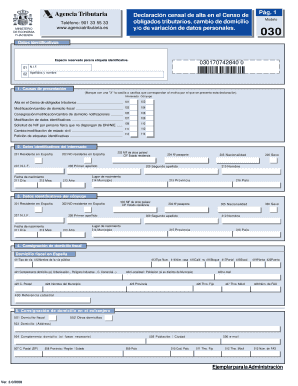
Get the free Web Attacker - cseweb ucsd
Show details
Web Security CSE 127Web Attacker Owns attacker.com Can get an SSL Certificate for attacker.com Can entice the user to visit attacker.com typo squatting e.g. gogle.com social media link phishing email
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign web attacker - cseweb
Edit your web attacker - cseweb form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.
Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your web attacker - cseweb form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit web attacker - cseweb online
Here are the steps you need to follow to get started with our professional PDF editor:
1
Log into your account. If you don't have a profile yet, click Start Free Trial and sign up for one.
2
Simply add a document. Select Add New from your Dashboard and import a file into the system by uploading it from your device or importing it via the cloud, online, or internal mail. Then click Begin editing.
3
Edit web attacker - cseweb. Rearrange and rotate pages, insert new and alter existing texts, add new objects, and take advantage of other helpful tools. Click Done to apply changes and return to your Dashboard. Go to the Documents tab to access merging, splitting, locking, or unlocking functions.
4
Save your file. Select it in the list of your records. Then, move the cursor to the right toolbar and choose one of the available exporting methods: save it in multiple formats, download it as a PDF, send it by email, or store it in the cloud.
pdfFiller makes working with documents easier than you could ever imagine. Create an account to find out for yourself how it works!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out web attacker - cseweb
How to fill out web attacker
01
To fill out a web attacker, follow these steps:
02
Identify the target website or application you want to attack.
03
Gather information about the target, such as its architecture, vulnerabilities, and potential entry points.
04
Research and understand various web attack techniques, such as SQL injection, cross-site scripting (XSS), or cross-site request forgery (CSRF).
05
Determine the most suitable attack vector based on the identified vulnerabilities and their potential impact.
06
Prepare the necessary tools and scripts required for the chosen attack technique.
07
Test the attack in a controlled environment, such as a local or sandboxed setup, to ensure its effectiveness.
08
Modify and optimize the attack approach, if needed, based on initial results.
09
Execute the attack on the target website or application using the chosen attack vector.
10
Monitor and analyze the attack's progress and success rate.
11
Maintain proper documentation of the attack methodology and techniques used for future reference.
12
Always practice ethical hacking and obtain proper authorization before performing any web attack.
Who needs web attacker?
01
Web attackers are individuals or organizations primarily involved in cybersecurity and ethical hacking domains.
02
The following groups of people may require a web attacker:
03
- Cybersecurity professionals performing penetration testing to discover and mitigate vulnerabilities within web applications.
04
- Ethical hackers running security assessments for businesses to identify potential weaknesses that could be exploited by malicious attackers.
05
- Researchers studying web vulnerabilities to improve security measures and develop effective countermeasures.
06
- Law enforcement agencies investigating cybercrimes and perpetrators involved in web attacks.
07
- System administrators and IT teams responsible for securing web-based infrastructures and preventing unauthorized access.
08
- Software developers and QA engineers testing the security of their web applications during the development lifecycle.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I edit web attacker - cseweb on a smartphone?
You can easily do so with pdfFiller's apps for iOS and Android devices, which can be found at the Apple Store and the Google Play Store, respectively. You can use them to fill out PDFs. We have a website where you can get the app, but you can also get it there. When you install the app, log in, and start editing web attacker - cseweb, you can start right away.
Can I edit web attacker - cseweb on an iOS device?
Create, modify, and share web attacker - cseweb using the pdfFiller iOS app. Easy to install from the Apple Store. You may sign up for a free trial and then purchase a membership.
How can I fill out web attacker - cseweb on an iOS device?
Install the pdfFiller app on your iOS device to fill out papers. If you have a subscription to the service, create an account or log in to an existing one. After completing the registration process, upload your web attacker - cseweb. You may now use pdfFiller's advanced features, such as adding fillable fields and eSigning documents, and accessing them from any device, wherever you are.
What is web attacker?
Web attacker refers to an individual or group of individuals who carry out malicious activities on a website or online platform.
Who is required to file web attacker?
Any individual or organization that has been a victim of a web attacker is required to file a report.
How to fill out web attacker?
To fill out a web attacker report, the victim must provide details of the attack, including the date, time, and nature of the incident.
What is the purpose of web attacker?
The purpose of filing a web attacker report is to document the attack and provide information for further investigation and prevention.
What information must be reported on web attacker?
The victim must report details of the attack such as the methods used, the impact on the website, and any potential vulnerabilities that were exploited.
Fill out your web attacker - cseweb online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Web Attacker - Cseweb is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.