Get the free Cybercriminals Exploit New Weaknesses in Retailers ... - FireEye
Show details
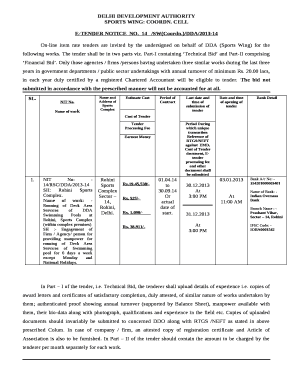
CASE STUDY Cybercriminals Exploit New Weaknesses in Retailers Networks* Turning Credit into Cash In 2013, intrusions in the retail industry utilized a new initial compromise vector and criminals used
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign cybercriminals exploit new weaknesses

Edit your cybercriminals exploit new weaknesses form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your cybercriminals exploit new weaknesses form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit cybercriminals exploit new weaknesses online
Follow the guidelines below to take advantage of the professional PDF editor:
1
Sign into your account. If you don't have a profile yet, click Start Free Trial and sign up for one.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit cybercriminals exploit new weaknesses. Text may be added and replaced, new objects can be included, pages can be rearranged, watermarks and page numbers can be added, and so on. When you're done editing, click Done and then go to the Documents tab to combine, divide, lock, or unlock the file.
4
Get your file. When you find your file in the docs list, click on its name and choose how you want to save it. To get the PDF, you can save it, send an email with it, or move it to the cloud.
With pdfFiller, dealing with documents is always straightforward.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out cybercriminals exploit new weaknesses

How to fill out cybercriminals exploit new weaknesses:
01
Stay updated with the latest technologies and vulnerabilities: Cybercriminals should constantly be aware of the new weaknesses and vulnerabilities that emerge in various technologies. They need to keep up with the latest news and research in the field to identify potential new avenues for exploitation.
02
Conduct thorough research and reconnaissance: Cybercriminals must conduct extensive research and reconnaissance to identify potential targets and vulnerabilities. This involves studying the target's systems, networks, and infrastructure to identify potential weaknesses that can be exploited.
03
Exploit known vulnerabilities: Once cybercriminals have identified a weakness, they use their technical skills to exploit it. This can involve various techniques such as exploiting software vulnerabilities, using social engineering tactics, or leveraging weak passwords.
04
Implement sophisticated attack techniques: Cybercriminals are constantly developing and refining their attack techniques. They may use advanced hacking tools or develop custom malware to exploit new weaknesses. They often employ techniques such as phishing, ransomware, or distributed denial-of-service (DDoS) attacks to compromise systems and steal valuable data.
05
Stay one step ahead of cybersecurity defenses: Cybercriminals constantly adapt and evolve their strategies to bypass the latest cybersecurity defenses. They continually analyze and study the security measures implemented by organizations to anticipate and exploit any weaknesses or gaps in their defense systems.
Who needs cybercriminals exploit new weaknesses:
01
State-sponsored hackers: Governments or nation-states may employ cybercriminals to exploit new weaknesses for political or strategic purposes. These hackers may target other countries, critical infrastructure, or high-value individuals to gain access to sensitive information or disrupt operations.
02
Criminal organizations: Organized criminal groups often hire cybercriminals to exploit weaknesses in order to conduct various illegal activities. This can include financial fraud, identity theft, or unauthorized access to sensitive information for monetary gain.
03
Hacktivists: Hacktivist groups with political or ideological motivations may use cybercriminals to exploit new weaknesses in order to advance their cause, disrupt operations, or spread their message. They may target government agencies, corporations, or individuals that they perceive as threats or opponents.
04
Competitor companies: In some cases, businesses may employ cybercriminals to exploit weaknesses in their competitors' systems to gain a competitive edge. This can involve stealing proprietary information, sabotaging operations, or damaging reputations.
05
Private individuals: Some individuals may hire cybercriminals to exploit weaknesses in personal devices, networks, or online accounts. This can be for various reasons such as revenge, blackmail, or personal gain.
Overall, cybercriminals exploit new weaknesses to accomplish their specific goals, which can range from financial gain to political or ideological motives. The frequency and impact of their actions highlight the importance of robust cybersecurity measures to protect individuals, organizations, and society as a whole.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is cybercriminals exploit new weaknesses?
Cybercriminals exploit new weaknesses by identifying vulnerabilities in systems or software and using them to gain unauthorized access or steal sensitive information.
Who is required to file cybercriminals exploit new weaknesses?
Anyone who has knowledge of cybercriminals exploiting new weaknesses should report it to the appropriate authorities or cybersecurity teams.
How to fill out cybercriminals exploit new weaknesses?
To fill out a report on cybercriminals exploiting new weaknesses, provide detailed information about the vulnerability or attack, including any evidence or logs that may help in investigation.
What is the purpose of cybercriminals exploit new weaknesses?
The purpose of cybercriminals exploiting new weaknesses is to gain unauthorized access to systems, steal sensitive information, disrupt operations, or extort money from individuals or organizations.
What information must be reported on cybercriminals exploit new weaknesses?
Any information related to the vulnerability, attack method, impact on systems or data, and any actions taken to mitigate the threat should be reported on cybercriminals exploiting new weaknesses.
Can I create an electronic signature for signing my cybercriminals exploit new weaknesses in Gmail?
Create your eSignature using pdfFiller and then eSign your cybercriminals exploit new weaknesses immediately from your email with pdfFiller's Gmail add-on. To keep your signatures and signed papers, you must create an account.
How can I edit cybercriminals exploit new weaknesses on a smartphone?
You can do so easily with pdfFiller’s applications for iOS and Android devices, which can be found at the Apple Store and Google Play Store, respectively. Alternatively, you can get the app on our web page: https://edit-pdf-ios-android.pdffiller.com/. Install the application, log in, and start editing cybercriminals exploit new weaknesses right away.
How do I edit cybercriminals exploit new weaknesses on an iOS device?
Create, modify, and share cybercriminals exploit new weaknesses using the pdfFiller iOS app. Easy to install from the Apple Store. You may sign up for a free trial and then purchase a membership.
Fill out your cybercriminals exploit new weaknesses online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Cybercriminals Exploit New Weaknesses is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.