Get the free Policy/Procedure: Access to Protected Health Information - ...
Show details
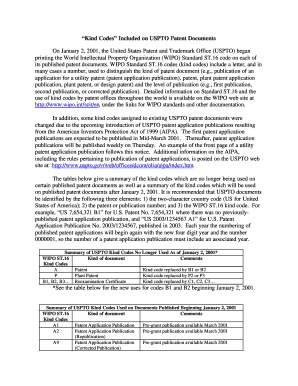
Policy/Procedure:Access to Protected Health InformationReviewed and Accepted by: Approved by: Date of Issue: Date Revised/Reviewed:John A Million III & Justin Honiara John A Million III 3/1/17 10/1/17Policy:
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign policyprocedure access to protected

Edit your policyprocedure access to protected form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your policyprocedure access to protected form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing policyprocedure access to protected online
To use the professional PDF editor, follow these steps below:
1
Set up an account. If you are a new user, click Start Free Trial and establish a profile.
2
Prepare a file. Use the Add New button. Then upload your file to the system from your device, importing it from internal mail, the cloud, or by adding its URL.
3
Edit policyprocedure access to protected. Replace text, adding objects, rearranging pages, and more. Then select the Documents tab to combine, divide, lock or unlock the file.
4
Save your file. Choose it from the list of records. Then, shift the pointer to the right toolbar and select one of the several exporting methods: save it in multiple formats, download it as a PDF, email it, or save it to the cloud.
pdfFiller makes dealing with documents a breeze. Create an account to find out!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out policyprocedure access to protected

How to fill out policyprocedure access to protected
01
To fill out a policy procedure access to protected, follow these steps:
02
Determine the specific policies and procedures that require access to be protected.
03
Identify the key stakeholders who need to be involved in the policy procedure access to protected.
04
Create a comprehensive list of the protected information and resources that need to be included in the policy procedure access.
05
Develop a clear and concise set of guidelines and protocols for accessing the protected information and resources.
06
Implement appropriate security measures, such as authentication, encryption, and regular monitoring, to ensure the integrity and confidentiality of the protected access.
07
Train and educate employees and other authorized personnel on the proper use and adherence to the policy procedure access.
08
Regularly review and update the policy procedure access to reflect changing technologies, best practices, and regulatory requirements.
09
Conduct periodic audits and assessments to ensure compliance with the policy procedure access.
10
Continuously monitor and evaluate the effectiveness of the policy procedure access and make necessary improvements.
Who needs policyprocedure access to protected?
01
Anyone who requires access to protected information and resources should follow the policy procedure access. This includes:
02
- Employees who handle sensitive data or have administrative privileges.
03
- Contractors or third-party vendors who have access to confidential information.
04
- Managers and supervisors who oversee the implementation and enforcement of access policies.
05
- IT personnel responsible for managing and securing systems and networks.
06
- Auditors and compliance officers who ensure adherence to privacy and security regulations.
07
- Executives and decision-makers who need access to protected information to make informed choices.
08
- Legal and HR departments who handle sensitive employee data.
09
- Any other individuals or departments with a legitimate need to access and protect confidential information.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I modify policyprocedure access to protected without leaving Google Drive?
You can quickly improve your document management and form preparation by integrating pdfFiller with Google Docs so that you can create, edit and sign documents directly from your Google Drive. The add-on enables you to transform your policyprocedure access to protected into a dynamic fillable form that you can manage and eSign from any internet-connected device.
Can I create an eSignature for the policyprocedure access to protected in Gmail?
You can easily create your eSignature with pdfFiller and then eSign your policyprocedure access to protected directly from your inbox with the help of pdfFiller’s add-on for Gmail. Please note that you must register for an account in order to save your signatures and signed documents.
Can I edit policyprocedure access to protected on an iOS device?
Create, modify, and share policyprocedure access to protected using the pdfFiller iOS app. Easy to install from the Apple Store. You may sign up for a free trial and then purchase a membership.
What is policyprocedure access to protected?
Policy procedure access to protected is a set of guidelines and regulations that outline the rules and procedures for accessing protected information or resources.
Who is required to file policyprocedure access to protected?
All employees and individuals who need to access protected information are required to file policy procedure access to protected.
How to fill out policyprocedure access to protected?
Policy procedure access to protected can be filled out by completing the required forms and submitting them to the designated department for review and approval.
What is the purpose of policyprocedure access to protected?
The purpose of policy procedure access to protected is to ensure that only authorized individuals have access to sensitive and protected information, thereby safeguarding confidentiality and security.
What information must be reported on policyprocedure access to protected?
Policy procedure access to protected typically requires individuals to report their personal information, reason for access, and any necessary approvals or authorizations.
Fill out your policyprocedure access to protected online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Policyprocedure Access To Protected is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.