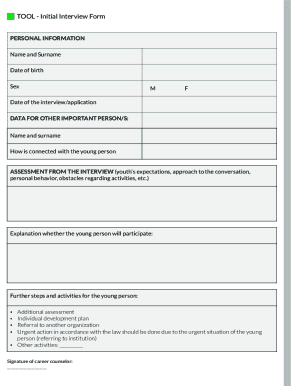
Get the free CYBER ATTACKS WHAT TO KNOW AND WHAT TO DO SOME
Show details
Cyberattacks WHAT TO KNOW AND WHAT TO DO SOME BASICS Davina PruittMentle, PhD ET PRO 2014 ASB Conference, Ocean City, MD 2014 ET PRO. This work may be reproduced and redistributed, in whole or in
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign cyber attacks what to

Edit your cyber attacks what to form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your cyber attacks what to form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit cyber attacks what to online
Use the instructions below to start using our professional PDF editor:
1
Create an account. Begin by choosing Start Free Trial and, if you are a new user, establish a profile.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit cyber attacks what to. Rearrange and rotate pages, add and edit text, and use additional tools. To save changes and return to your Dashboard, click Done. The Documents tab allows you to merge, divide, lock, or unlock files.
4
Get your file. When you find your file in the docs list, click on its name and choose how you want to save it. To get the PDF, you can save it, send an email with it, or move it to the cloud.
pdfFiller makes working with documents easier than you could ever imagine. Register for an account and see for yourself!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out cyber attacks what to

How to fill out cyber attacks what to
01
Start by understanding the types of cyber attacks that exist, such as phishing, malware, and denial of service attacks.
02
Educate yourself and your team about common vulnerabilities and how to recognize and prevent them.
03
Implement strong password policies and multi-factor authentication to protect against unauthorized access.
04
Keep all software and systems up to date with the latest security patches.
05
Regularly backup important data and files to ensure they can be recovered in case of a cyber attack.
06
Use a reliable antivirus software and firewall to detect and block malicious activities.
07
Train employees on safe internet usage, including how to identify suspicious emails and avoid clicking on malicious links.
08
Monitor and analyze network traffic for any signs of unusual or suspicious activity.
09
Develop an incident response plan to effectively handle a cyber attack if it occurs.
10
Stay informed about emerging threats and cybersecurity best practices to continuously improve your defenses.
Who needs cyber attacks what to?
01
Anyone who uses computers or digital devices for personal or professional purposes needs to be aware of cyber attacks and how to protect against them.
02
Businesses, especially those that handle sensitive customer data or intellectual property, have a high need for cybersecurity measures.
03
Government organizations and agencies need to protect classified information and critical infrastructure from cyber attacks.
04
Educational institutions should prioritize cybersecurity to safeguard student and staff data.
05
Individuals who store personal information, make online transactions, or use social media should also be vigilant against cyber attacks.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
Can I create an electronic signature for signing my cyber attacks what to in Gmail?
You can easily create your eSignature with pdfFiller and then eSign your cyber attacks what to directly from your inbox with the help of pdfFiller’s add-on for Gmail. Please note that you must register for an account in order to save your signatures and signed documents.
How do I edit cyber attacks what to on an iOS device?
Use the pdfFiller mobile app to create, edit, and share cyber attacks what to from your iOS device. Install it from the Apple Store in seconds. You can benefit from a free trial and choose a subscription that suits your needs.
How can I fill out cyber attacks what to on an iOS device?
Make sure you get and install the pdfFiller iOS app. Next, open the app and log in or set up an account to use all of the solution's editing tools. If you want to open your cyber attacks what to, you can upload it from your device or cloud storage, or you can type the document's URL into the box on the right. After you fill in all of the required fields in the document and eSign it, if that is required, you can save or share it with other people.
What is cyber attacks what to?
Cyber attacks refers to the unauthorized access or disruption of computer systems or networks.
Who is required to file cyber attacks what to?
Organizations that experience a cyber attack are required to file a report.
How to fill out cyber attacks what to?
The report must be filled out by providing detailed information about the cyber attack incident.
What is the purpose of cyber attacks what to?
The purpose of filing cyber attacks report is to inform authorities about the incident and take necessary actions to prevent future attacks.
What information must be reported on cyber attacks what to?
The report must include details about the attack, impact on systems, data compromised, and mitigation steps taken.
Fill out your cyber attacks what to online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Cyber Attacks What To is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.