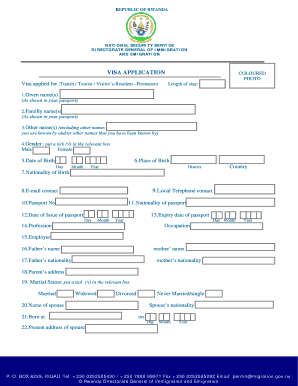
Get the free Protocol to Identify and Address Licensed Child Day Cares On ...
Show details
Protocol to Identify and Address
Licensed Child Day Cares
On or Near Locations with Chemical ContaminationFINALJune 2010Protocol to Identify and Address Licensed Child Day Cares On or Near Locations
With
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign protocol to identify and

Edit your protocol to identify and form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your protocol to identify and form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing protocol to identify and online
Follow the steps below to benefit from a competent PDF editor:
1
Create an account. Begin by choosing Start Free Trial and, if you are a new user, establish a profile.
2
Prepare a file. Use the Add New button. Then upload your file to the system from your device, importing it from internal mail, the cloud, or by adding its URL.
3
Edit protocol to identify and. Text may be added and replaced, new objects can be included, pages can be rearranged, watermarks and page numbers can be added, and so on. When you're done editing, click Done and then go to the Documents tab to combine, divide, lock, or unlock the file.
4
Save your file. Select it from your records list. Then, click the right toolbar and select one of the various exporting options: save in numerous formats, download as PDF, email, or cloud.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out protocol to identify and

How to fill out protocol to identify and
01
To fill out a protocol to identify, follow these steps:
02
Start by writing the title of the protocol, indicating that it is for identification purposes.
03
Include the date and time of the identification process.
04
List all the individuals or objects that need to be identified.
05
Indicate the method or procedure that will be used for identification.
06
Provide any necessary instructions or guidelines for the identification process.
07
Leave space for signatures of the individuals involved in the identification.
08
Finally, review and double-check the protocol for accuracy and completeness before using it for identification purposes.
Who needs protocol to identify and?
01
A protocol to identify and may be needed by:
02
- Law enforcement agencies during criminal investigations to establish the identity of suspects or victims.
03
- Security personnel at airports, borders, or other high-security areas to verify the identities of individuals.
04
- Organizations conducting background checks or identity verification for employment or access control purposes.
05
- Medical professionals performing patient identification to ensure accurate medical records and treatment.
06
- Research institutions or laboratories conducting experiments or studies that require identification of specimens or subjects.
07
- Any individual or organization that needs a documented and standardized process for identification purposes.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I manage my protocol to identify and directly from Gmail?
pdfFiller’s add-on for Gmail enables you to create, edit, fill out and eSign your protocol to identify and and any other documents you receive right in your inbox. Visit Google Workspace Marketplace and install pdfFiller for Gmail. Get rid of time-consuming steps and manage your documents and eSignatures effortlessly.
Can I edit protocol to identify and on an iOS device?
Use the pdfFiller mobile app to create, edit, and share protocol to identify and from your iOS device. Install it from the Apple Store in seconds. You can benefit from a free trial and choose a subscription that suits your needs.
How can I fill out protocol to identify and on an iOS device?
pdfFiller has an iOS app that lets you fill out documents on your phone. A subscription to the service means you can make an account or log in to one you already have. As soon as the registration process is done, upload your protocol to identify and. You can now use pdfFiller's more advanced features, like adding fillable fields and eSigning documents, as well as accessing them from any device, no matter where you are in the world.
What is protocol to identify and?
Protocol to identify and is a set of guidelines and procedures used to accurately identify a person or entity.
Who is required to file protocol to identify and?
Any individual or organization that needs to verify the identity of another person or entity is required to file a protocol to identify and.
How to fill out protocol to identify and?
Protocol to identify and can be filled out by providing relevant information such as name, address, date of birth, and any other identifying details.
What is the purpose of protocol to identify and?
The purpose of protocol to identify and is to ensure that individuals or entities are accurately identified and verified for various purposes such as security, compliance, or legal reasons.
What information must be reported on protocol to identify and?
The information reported on protocol to identify and typically includes personal details, identification documents, and any other relevant information required for verification.
Fill out your protocol to identify and online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Protocol To Identify And is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.