Get the free Cyber Crime Fundamentals - e-vision anglia ac
Show details
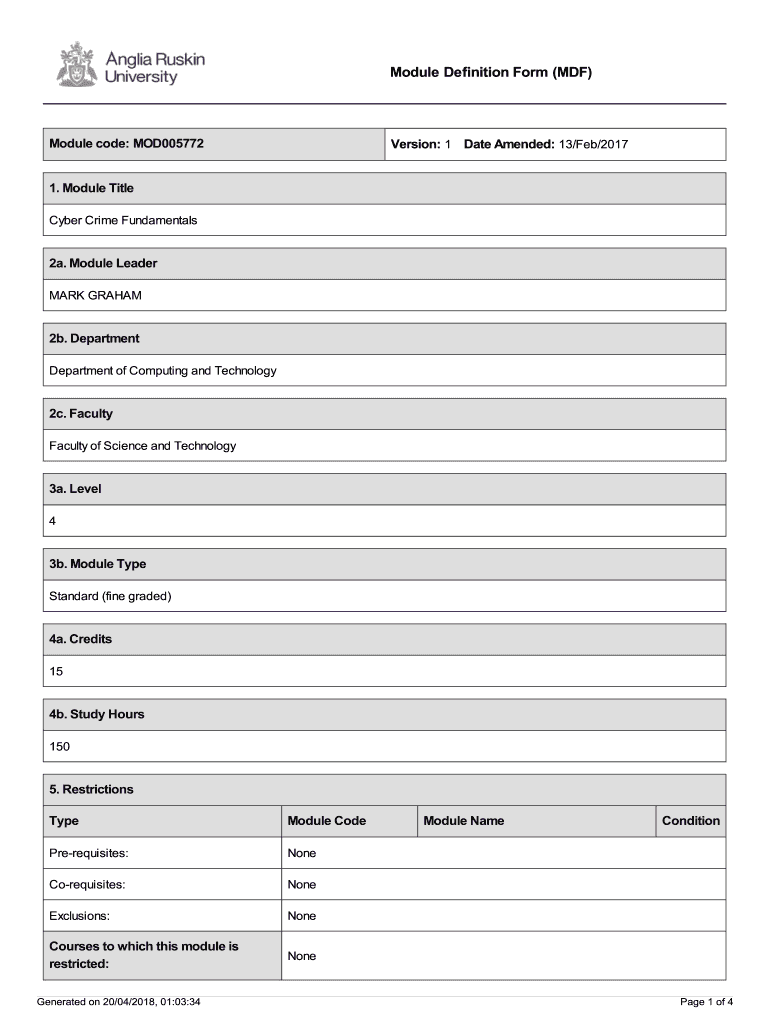
Module Definition Form (MDF)Module code: MOD005772Version: 1 Date Amended: 13/Feb/20171. Module Title
Cyber Crime Fundamentals2a. Module Leader
MARK GRAHAM2b. Department of Computing and Technology2c.
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign cyber crime fundamentals

Edit your cyber crime fundamentals form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your cyber crime fundamentals form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing cyber crime fundamentals online
Here are the steps you need to follow to get started with our professional PDF editor:
1
Check your account. If you don't have a profile yet, click Start Free Trial and sign up for one.
2
Upload a file. Select Add New on your Dashboard and upload a file from your device or import it from the cloud, online, or internal mail. Then click Edit.
3
Edit cyber crime fundamentals. Add and change text, add new objects, move pages, add watermarks and page numbers, and more. Then click Done when you're done editing and go to the Documents tab to merge or split the file. If you want to lock or unlock the file, click the lock or unlock button.
4
Get your file. When you find your file in the docs list, click on its name and choose how you want to save it. To get the PDF, you can save it, send an email with it, or move it to the cloud.
pdfFiller makes working with documents easier than you could ever imagine. Create an account to find out for yourself how it works!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out cyber crime fundamentals

How to fill out cyber crime fundamentals
01
To fill out cyber crime fundamentals, follow these steps:
02
Start by familiarizing yourself with the basics of cyber crime, including its definition, types of cyber crime, and common cyber crime techniques.
03
Gather necessary information and evidence related to the specific cyber crime case you are investigating or analyzing.
04
Analyze the information and evidence to identify the motives, methods, and potential perpetrators of the cyber crime.
05
Document your findings in a clear and organized manner, ensuring that all relevant details are included.
06
Prepare a comprehensive report summarizing the cyber crime, its impact, and any recommendations for prevention or further action.
07
Continuously update your knowledge and skills in the field of cyber crime by staying informed about the latest trends, technologies, and legal developments.
08
Practice ethical conduct and adhere to legal and professional standards while conducting cyber crime investigations or analyses.
Who needs cyber crime fundamentals?
01
Cyber crime fundamentals are essential for anyone involved in or interested in the field of cyber security and online investigations. Specifically, the following individuals or groups can benefit from cyber crime fundamentals:
02
- Law enforcement agencies and officers responsible for combating cyber crime.
03
- Cyber security professionals and experts tasked with protecting networks, systems, and data from cyber threats.
04
- Digital forensics investigators involved in analyzing and recovering evidence from cyber crime incidents.
05
- Government authorities and policymakers responsible for creating and implementing cyber crime laws and regulations.
06
- Legal professionals involved in prosecuting cyber criminals or handling cyber crime-related cases.
07
- IT professionals and system administrators responsible for maintaining the security of computer networks and infrastructure.
08
- Businesses and organizations concerned about cyber threats and seeking to develop effective preventive measures.
09
- Individuals who want to enhance their knowledge and awareness of cyber crime for personal or professional reasons.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I edit cyber crime fundamentals on a smartphone?
The pdfFiller mobile applications for iOS and Android are the easiest way to edit documents on the go. You may get them from the Apple Store and Google Play. More info about the applications here. Install and log in to edit cyber crime fundamentals.
How do I complete cyber crime fundamentals on an iOS device?
Install the pdfFiller iOS app. Log in or create an account to access the solution's editing features. Open your cyber crime fundamentals by uploading it from your device or online storage. After filling in all relevant fields and eSigning if required, you may save or distribute the document.
How do I complete cyber crime fundamentals on an Android device?
Use the pdfFiller mobile app and complete your cyber crime fundamentals and other documents on your Android device. The app provides you with all essential document management features, such as editing content, eSigning, annotating, sharing files, etc. You will have access to your documents at any time, as long as there is an internet connection.
Fill out your cyber crime fundamentals online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Cyber Crime Fundamentals is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.





















