Get the free Bulletin d'exploitation - itu.int
Show details
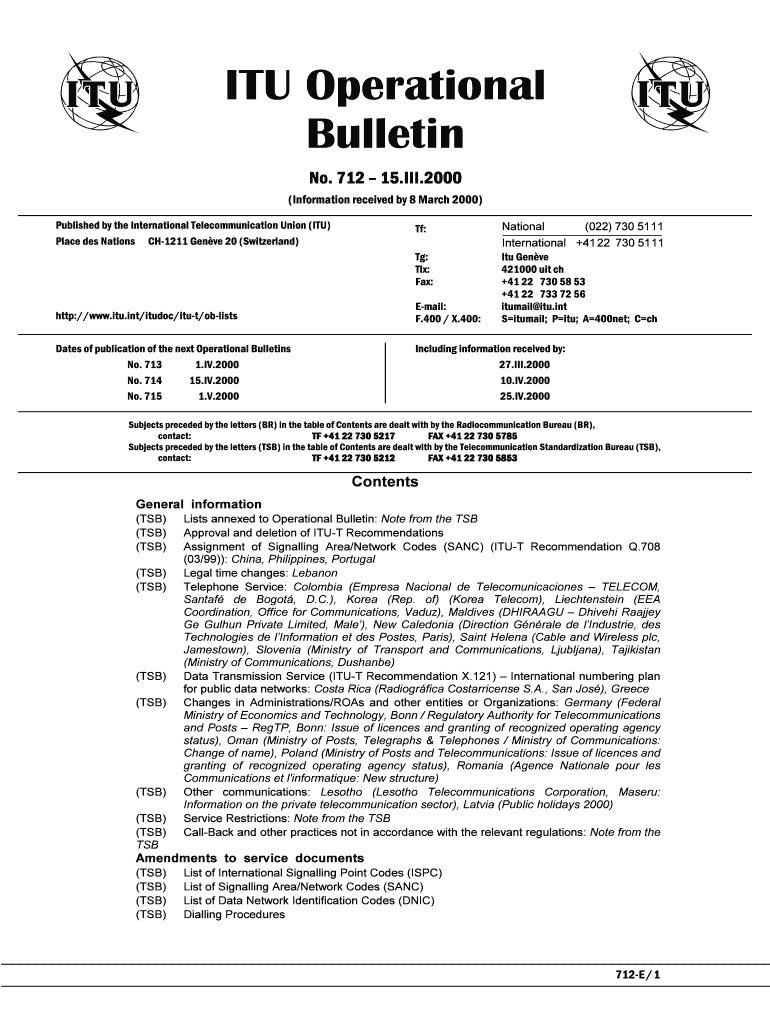
ITU Operational Bulletin No. 712 15.III.2000 (Information received by 8 March 2000) Published by the International Telecommunication Union (ITU) Place DES Nations CH1211 Genre 20 (Switzerland)TF:
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign bulletin dexploitation - ituint
Edit your bulletin dexploitation - ituint form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.
Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your bulletin dexploitation - ituint form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit bulletin dexploitation - ituint online
Use the instructions below to start using our professional PDF editor:
1
Create an account. Begin by choosing Start Free Trial and, if you are a new user, establish a profile.
2
Prepare a file. Use the Add New button. Then upload your file to the system from your device, importing it from internal mail, the cloud, or by adding its URL.
3
Edit bulletin dexploitation - ituint. Rearrange and rotate pages, add new and changed texts, add new objects, and use other useful tools. When you're done, click Done. You can use the Documents tab to merge, split, lock, or unlock your files.
4
Get your file. Select your file from the documents list and pick your export method. You may save it as a PDF, email it, or upload it to the cloud.
Dealing with documents is always simple with pdfFiller.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out bulletin dexploitation - ituint
How to fill out bulletin dexploitation - ituint
01
To fill out bulletin d'exploitation - ituint, follow these steps:
02
Start by entering the date at the top of the bulletin.
03
Provide the name and contact details of the person responsible for the exploitation.
04
Specify the software or system that is being exploited.
05
Describe the purpose and objective of the exploitation.
06
List the steps or tasks involved in the exploitation process.
07
Include any relevant codes, scripts, or files that are used in the exploitation.
08
Provide a detailed description of the expected outcomes or results.
09
Include any necessary documentation or references related to the exploitation.
10
Finally, review and double-check all the information provided before submitting the bulletin.
11
Note: The specific format or requirements of the bulletin may vary depending on the organization or context. Make sure to adhere to any guidelines or instructions provided by your organization.
Who needs bulletin dexploitation - ituint?
01
Bulletin d'exploitation - ituint is needed by individuals or organizations involved in technology or cybersecurity. This includes software developers, system administrators, IT professionals, ethical hackers, and cybersecurity consultants. The bulletin helps them document and communicate the process of exploiting software or systems, identifying vulnerabilities, and proposing recommendations for improvements. It is an essential tool for ensuring the security and stability of technology infrastructure.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I manage my bulletin dexploitation - ituint directly from Gmail?
You can use pdfFiller’s add-on for Gmail in order to modify, fill out, and eSign your bulletin dexploitation - ituint along with other documents right in your inbox. Find pdfFiller for Gmail in Google Workspace Marketplace. Use time you spend on handling your documents and eSignatures for more important things.
How do I complete bulletin dexploitation - ituint online?
Filling out and eSigning bulletin dexploitation - ituint is now simple. The solution allows you to change and reorganize PDF text, add fillable fields, and eSign the document. Start a free trial of pdfFiller, the best document editing solution.
Can I create an eSignature for the bulletin dexploitation - ituint in Gmail?
It's easy to make your eSignature with pdfFiller, and then you can sign your bulletin dexploitation - ituint right from your Gmail inbox with the help of pdfFiller's add-on for Gmail. This is a very important point: You must sign up for an account so that you can save your signatures and signed documents.
What is bulletin dexploitation - ituint?
Bulletin d'exploitation - ituint is a document used to report operational activities and performance in IT sector.
Who is required to file bulletin dexploitation - ituint?
IT companies and service providers are required to file bulletin d'exploitation - ituint.
How to fill out bulletin dexploitation - ituint?
Bulletin d'exploitation - ituint can be filled out online through a designated platform provided by the regulatory authorities.
What is the purpose of bulletin dexploitation - ituint?
The purpose of bulletin d'exploitation - ituint is to monitor and regulate IT activities, ensure compliance with regulations, and assess the performance of IT companies.
What information must be reported on bulletin dexploitation - ituint?
Information such as financial data, operational statistics, security measures, and compliance status must be reported on bulletin d'exploitation - ituint.
Fill out your bulletin dexploitation - ituint online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Bulletin Dexploitation - Ituint is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.