Get the free Slide 1. Information Security Training - ohiowater
Show details
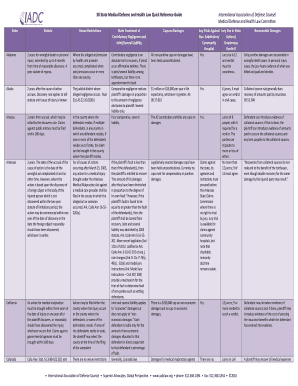
Lynn Marshall Bio: Activated Sludge Short School One Day Wastewater Training Event (24.0 Total Contact Hours) Friday, May 24, 2013, Held At: Rocky Fork State Park OPERATOR TRAINING COMMITTEE OF OHIO,
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign slide 1 information security

Edit your slide 1 information security form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your slide 1 information security form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing slide 1 information security online
Here are the steps you need to follow to get started with our professional PDF editor:
1
Log in to your account. Start Free Trial and register a profile if you don't have one.
2
Upload a file. Select Add New on your Dashboard and upload a file from your device or import it from the cloud, online, or internal mail. Then click Edit.
3
Edit slide 1 information security. Add and change text, add new objects, move pages, add watermarks and page numbers, and more. Then click Done when you're done editing and go to the Documents tab to merge or split the file. If you want to lock or unlock the file, click the lock or unlock button.
4
Save your file. Choose it from the list of records. Then, shift the pointer to the right toolbar and select one of the several exporting methods: save it in multiple formats, download it as a PDF, email it, or save it to the cloud.
pdfFiller makes dealing with documents a breeze. Create an account to find out!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out slide 1 information security

How to fill out slide 1 information security?
01
Identify the purpose of slide 1: Before filling out slide 1 on information security, it is important to clearly understand its purpose. Determine what specific information or key points you want to convey to your audience regarding information security.
02
Provide an introduction: Start by introducing the topic of information security and its importance. Include a brief overview of what information security entails and why it is crucial for individuals and organizations to pay attention to it.
03
Define information security: Clearly define what information security means and explain its main objectives. Emphasize the importance of protecting sensitive information, maintaining data confidentiality, and preventing unauthorized access or breaches.
04
Discuss common threats and risks: Highlight some of the most common information security threats and risks that individuals and organizations face. Talk about various types of cyber attacks, such as phishing, malware, and social engineering, and explain how they can compromise information security.
05
Explain best practices: Provide practical tips and best practices for ensuring information security. Discuss the importance of strong passwords, regular software updates, data backup, and encryption. Emphasize the need for employee training and awareness to prevent security incidents.
06
Include visual aids: Use relevant visuals, such as charts, graphs, or diagrams, to enhance the understanding of information security concepts. Visual aids can help in simplifying complex information and making it more engaging for the audience.
07
Add relevant examples or case studies: Incorporate real-life examples or case studies that illustrate the consequences of poor information security practices. This can help the audience better comprehend the potential risks and motivate them to take appropriate measures.
Who needs slide 1 information security?
01
Organizations: Any organization, regardless of its size or industry, needs to prioritize information security. Protecting sensitive company data, customer information, financial records, and intellectual property is crucial for maintaining trust, reputation, and complying with legal regulations.
02
Individuals: Individual users, including employees, students, or any person handling electronic devices or accessing the internet, need to understand the importance of information security. Individuals can become targets of cyber attacks and may unknowingly expose sensitive information if they are not equipped with the necessary knowledge.
03
IT Professionals: IT professionals play a vital role in implementing and maintaining information security measures within organizations. They need to have a thorough understanding of information security principles, best practices, and the latest technologies to secure networks, systems, and data.
04
Decision-makers: Executives and decision-makers within organizations need to be aware of information security risks and considerations. They should understand the potential consequences of inadequate security measures and make informed decisions regarding budget allocation, resource allocation, and policy implementation.
Overall, anyone who interacts with or handles sensitive information, whether in a personal or professional capacity, can benefit from understanding and implementing information security measures.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
Can I sign the slide 1 information security electronically in Chrome?
Yes. With pdfFiller for Chrome, you can eSign documents and utilize the PDF editor all in one spot. Create a legally enforceable eSignature by sketching, typing, or uploading a handwritten signature image. You may eSign your slide 1 information security in seconds.
Can I create an electronic signature for signing my slide 1 information security in Gmail?
It's easy to make your eSignature with pdfFiller, and then you can sign your slide 1 information security right from your Gmail inbox with the help of pdfFiller's add-on for Gmail. This is a very important point: You must sign up for an account so that you can save your signatures and signed documents.
How do I edit slide 1 information security on an iOS device?
Create, modify, and share slide 1 information security using the pdfFiller iOS app. Easy to install from the Apple Store. You may sign up for a free trial and then purchase a membership.
What is slide 1 information security?
Slide 1 information security refers to the initial reporting document required by certain regulatory bodies.
Who is required to file slide 1 information security?
Certain organizations or companies may be required to file slide 1 information security based on regulations set forth by relevant authorities.
How to fill out slide 1 information security?
Slide 1 information security is typically filled out by providing detailed information about the organization's security measures, protocols, and any incidents that have occurred.
What is the purpose of slide 1 information security?
The purpose of slide 1 information security is to provide transparency and accountability regarding an organization's security practices.
What information must be reported on slide 1 information security?
Information such as security protocols, incident response plans, and any security breaches must be reported on slide 1 information security.
Fill out your slide 1 information security online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Slide 1 Information Security is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.