Get the free Endpoint Security and Security Awareness Training - ibat
Show details
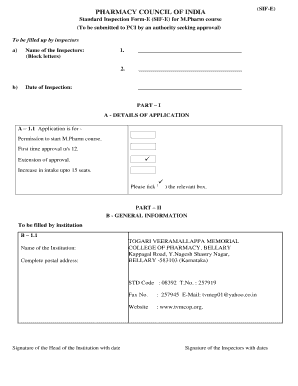
Who Should Attend Endpoint Security and Security Awareness Training This summit will benefit CEOs, COOs, Security Officers and anyone responsible for risk management of community financial institutions'
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign endpoint security and security

Edit your endpoint security and security form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your endpoint security and security form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit endpoint security and security online
Here are the steps you need to follow to get started with our professional PDF editor:
1
Register the account. Begin by clicking Start Free Trial and create a profile if you are a new user.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit endpoint security and security. Rearrange and rotate pages, insert new and alter existing texts, add new objects, and take advantage of other helpful tools. Click Done to apply changes and return to your Dashboard. Go to the Documents tab to access merging, splitting, locking, or unlocking functions.
4
Save your file. Select it from your list of records. Then, move your cursor to the right toolbar and choose one of the exporting options. You can save it in multiple formats, download it as a PDF, send it by email, or store it in the cloud, among other things.
With pdfFiller, it's always easy to work with documents.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out endpoint security and security

01
Identify the purpose and objectives of endpoint security and security. Understand the importance of protecting endpoints (computers, servers, mobile devices) from threats and securing the overall network.
02
Assess your organization's current security infrastructure and identify any gaps or vulnerabilities. This includes evaluating existing security measures, such as firewalls, antivirus software, and data encryption.
03
Determine the scope of endpoint security and security needed. Consider the number of endpoints, the types of devices being used, and the level of sensitive data being handled.
04
Research and select appropriate endpoint security solutions. Look for solutions that offer features such as real-time threat detection, malware protection, data loss prevention, and device monitoring.
05
Implement the chosen endpoint security solution across all endpoints in your organization. This may involve installing software agents or deploying hardware devices. Ensure that all endpoints are properly configured and updated with the latest security patches.
06
Establish security policies and procedures. Define guidelines for using and accessing endpoints, including strong password requirements, remote access protocols, and data backup procedures. Educate employees about these policies and enforce them consistently.
07
Regularly monitor and update endpoint security measures. This includes performing security audits, conducting vulnerability assessments, and applying patches and updates to software and hardware.
08
Train employees on endpoint security best practices. Teach them how to identify and report suspicious activities, avoid phishing scams, and protect sensitive data. Encourage a culture of security awareness and responsibility.
09
Continuously evaluate and improve endpoint security measures. Stay up-to-date with the latest security threats and industry best practices. Conduct regular risk assessments and adapt your security strategy accordingly.
Who needs endpoint security and security?
01
Organizations of all sizes: Whether you're a small business or a large enterprise, endpoint security and security are essential for protecting against cyber threats that can compromise your data and network.
02
Remote workers and mobile devices: With the rise of remote work and the increasing use of mobile devices, endpoint security becomes even more critical. Remote workers accessing company resources from their personal laptops or mobile phones need to be protected.
03
Industries handling sensitive data: Industries that deal with sensitive information, such as healthcare, finance, and legal sectors, have strict regulatory requirements. Endpoint security helps these organizations comply with data protection laws and safeguard sensitive data.
04
Any organization connected to the internet: In today's interconnected world, virtually every organization is connected to the internet in some way. This makes them vulnerable to cyber attacks, highlighting the need for endpoint security measures.
05
Individuals concerned about personal security: Individuals who value their privacy and want to secure their personal devices, such as computers and smartphones, can also benefit from implementing endpoint security measures.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is endpoint security and security?
Endpoint security is the practice of securing endpoints or entry points on a network, such as desktops, laptops, and mobile devices. This is done to protect against cybersecurity threats and ensure data security.
Who is required to file endpoint security and security?
Organizations and businesses that have endpoints connected to their network are required to implement and file endpoint security measures.
How to fill out endpoint security and security?
Endpoint security measures can be filled out by implementing antivirus software, firewalls, encryption, and regular security updates.
What is the purpose of endpoint security and security?
The purpose of endpoint security is to protect endpoints from cybersecurity threats such as malware, phishing attacks, and unauthorized access.
What information must be reported on endpoint security and security?
Information such as the types of security measures implemented, any incidents or breaches, and any changes to security policies must be reported on endpoint security.
Where do I find endpoint security and security?
The pdfFiller premium subscription gives you access to a large library of fillable forms (over 25 million fillable templates) that you can download, fill out, print, and sign. In the library, you'll have no problem discovering state-specific endpoint security and security and other forms. Find the template you want and tweak it with powerful editing tools.
Can I create an eSignature for the endpoint security and security in Gmail?
With pdfFiller's add-on, you may upload, type, or draw a signature in Gmail. You can eSign your endpoint security and security and other papers directly in your mailbox with pdfFiller. To preserve signed papers and your personal signatures, create an account.
How do I complete endpoint security and security on an iOS device?
Install the pdfFiller app on your iOS device to fill out papers. If you have a subscription to the service, create an account or log in to an existing one. After completing the registration process, upload your endpoint security and security. You may now use pdfFiller's advanced features, such as adding fillable fields and eSigning documents, and accessing them from any device, wherever you are.
Fill out your endpoint security and security online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Endpoint Security And Security is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.