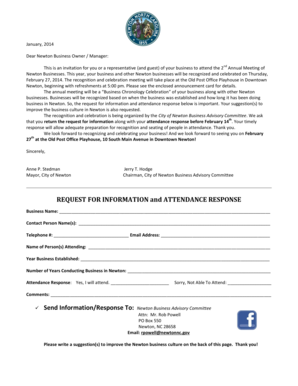
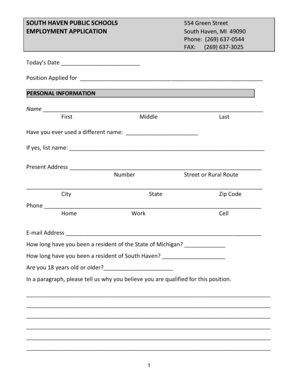
Get the free COMPUTER FORENSIC INTAKE RECEIPT AND AGREEMENT
Show details
This document is an agreement between the User and KBSolutions Inc. for forensic computer intake services. It outlines the services provided, the User's rights and responsibilities, and terms regarding
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign computer forensic intake receipt

Edit your computer forensic intake receipt form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your computer forensic intake receipt form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit computer forensic intake receipt online
Here are the steps you need to follow to get started with our professional PDF editor:
1
Log in to your account. Start Free Trial and register a profile if you don't have one yet.
2
Simply add a document. Select Add New from your Dashboard and import a file into the system by uploading it from your device or importing it via the cloud, online, or internal mail. Then click Begin editing.
3
Edit computer forensic intake receipt. Rearrange and rotate pages, insert new and alter existing texts, add new objects, and take advantage of other helpful tools. Click Done to apply changes and return to your Dashboard. Go to the Documents tab to access merging, splitting, locking, or unlocking functions.
4
Get your file. Select your file from the documents list and pick your export method. You may save it as a PDF, email it, or upload it to the cloud.
pdfFiller makes dealing with documents a breeze. Create an account to find out!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out computer forensic intake receipt

How to fill out COMPUTER FORENSIC INTAKE RECEIPT AND AGREEMENT
01
Begin by filling out the date at the top of the form.
02
Provide the name and contact information of the client on the designated lines.
03
Describe the nature of the forensic examination and the specific services requested.
04
Outline the terms and conditions, ensuring to highlight the confidentiality of the investigation.
05
Specify any associated fees, payment methods, and billing procedures.
06
Review and explain the consent section, ensuring the client understands their rights.
07
Obtain the client's signature, confirming their agreement to the terms and services outlined.
08
Keep a copy for your records and provide a copy to the client.
Who needs COMPUTER FORENSIC INTAKE RECEIPT AND AGREEMENT?
01
Individuals or businesses seeking forensic analysis of electronic devices.
02
Lawyers requiring documentation for legal cases involving digital evidence.
03
Organizations needing to ensure compliance with data protection regulations.
04
Law enforcement agencies conducting investigations that involve digital crimes.
Fill
form
: Try Risk Free






People Also Ask about
What are the five steps in the methodology for a forensic scientist to follow in investigating a case?
There are five main steps involved in the scientific method: stating the problem, forming the hypothesis, collecting the data by observing and experimenting, interpreting these data, and drawing conclusions.
What are the 5 steps in digital forensics?
In conclusion, the digital forensics investigation process involves several stages, including identification, collection, analysis, reporting, and presentation. By following a structured and methodical approach, cyber forensic companies can gather, analyze, and preserve digital evidence in a legal and ethical manner.
What are the five steps in the computer forensics process?
The core stages of a digital forensics investigation include: Identification of resources and devices involved in the investigation. Preservation of the necessary data. Analysis. Documentation. Presentation.
What are the four-four-step processes of computer forensics?
There are four main steps to computer forensics. Device identification. The first step is identifying the devices or storage media that might contain data, metadata or other digital artifacts relevant to the investigation. Data preservation. Forensic analysis. Reporting.
How long does a computer forensic investigation take?
A complete examination of a 100 GB of data on a hard drive can have over 10,000,000 pages of electronic information and may take between 15 to 35 hours or more to examine, depending on the size and types of media. A reasonable quote can be obtained prior to the investigation's start.
What are the five components of the computer forensic methodology?
5 Steps for Conducting Computer Forensics Investigations Policy and Procedure Development. Evidence Assessment. Evidence Acquisition. Evidence Examination. Documenting and Reporting.
What are the 5 key elements of digital forensics?
The core stages of a digital forensics investigation include: Identification of resources and devices involved in the investigation. Preservation of the necessary data. Analysis. Documentation. Presentation.
What is the methodology of computer forensics?
Computer forensic science (computer forensics) investigates computers and digital storage evidence. It involves examining digital data to identify, preserve, recover, analyze and present facts and opinions on inspected information.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is COMPUTER FORENSIC INTAKE RECEIPT AND AGREEMENT?
The Computer Forensic Intake Receipt and Agreement is a formal document that outlines the terms and conditions under which digital evidence is collected, analyzed, and stored during a forensic investigation.
Who is required to file COMPUTER FORENSIC INTAKE RECEIPT AND AGREEMENT?
Typically, the parties involved in the forensic investigation, such as law enforcement agencies, legal firms, or organizations conducting internal investigations, are required to file the Computer Forensic Intake Receipt and Agreement.
How to fill out COMPUTER FORENSIC INTAKE RECEIPT AND AGREEMENT?
To fill out the Computer Forensic Intake Receipt and Agreement, individuals must provide details such as the case number, the parties involved, the description of the assets being examined, and signatures from all relevant stakeholders indicating their consent and understanding of the terms.
What is the purpose of COMPUTER FORENSIC INTAKE RECEIPT AND AGREEMENT?
The purpose of the Computer Forensic Intake Receipt and Agreement is to establish a clear understanding between all parties regarding the scope of the forensic investigation, the handling of evidence, and the obligations of each party concerning confidentiality and data protection.
What information must be reported on COMPUTER FORENSIC INTAKE RECEIPT AND AGREEMENT?
The Computer Forensic Intake Receipt and Agreement must report information such as the case number, names of the involved parties, a detailed description of the digital evidence, acknowledgment of the terms and conditions by all parties, and signatures confirming agreement.
Fill out your computer forensic intake receipt online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Computer Forensic Intake Receipt is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.