Get the free Operating Systems Security - cse wustl
Show details
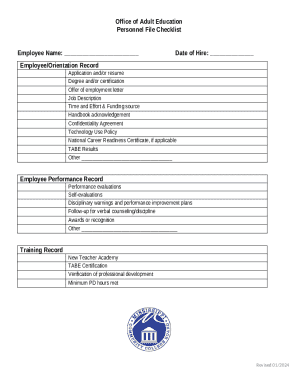
Operating Systems Security Raj Jain Washington University in Saint Louis, MO 63130 Jain CSE.USTL.edu Audio/video recordings of this lecture are available at: http://www.cse.wustl.edu/ Jain/cse571-09/
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign operating systems security

Edit your operating systems security form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your operating systems security form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit operating systems security online
Use the instructions below to start using our professional PDF editor:
1
Register the account. Begin by clicking Start Free Trial and create a profile if you are a new user.
2
Prepare a file. Use the Add New button. Then upload your file to the system from your device, importing it from internal mail, the cloud, or by adding its URL.
3
Edit operating systems security. Rearrange and rotate pages, insert new and alter existing texts, add new objects, and take advantage of other helpful tools. Click Done to apply changes and return to your Dashboard. Go to the Documents tab to access merging, splitting, locking, or unlocking functions.
4
Get your file. When you find your file in the docs list, click on its name and choose how you want to save it. To get the PDF, you can save it, send an email with it, or move it to the cloud.
Dealing with documents is simple using pdfFiller.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out operating systems security

How to fill out operating systems security:
01
Identify vulnerabilities: Start by conducting a comprehensive analysis to identify any potential vulnerabilities in the operating system. This can be done through regular security audits and vulnerability assessments.
02
Install security patches and updates: Keep the operating system up to date by regularly installing security patches and updates provided by the respective vendor. These patches often address known vulnerabilities and help protect against cyber threats.
03
Configure security settings: Adjust the security settings of the operating system to enhance its protection. This includes setting up strong passwords, enabling firewalls, and implementing multifactor authentication where applicable.
04
Implement access controls: Ensure that access to the operating system is restricted only to authorized individuals or user accounts. Use role-based access control (RBAC) or access permissions to limit privileges and prevent unauthorized access.
05
Regularly backup data: Perform regular backups of important data stored on the operating system. This helps in case of system failures or security breaches, allowing for quick recovery and minimizing potential data loss.
Who needs operating systems security:
01
Individuals: Anyone who uses a computer or mobile device with an operating system should prioritize operating system security. This applies to personal devices used for everyday tasks like browsing the internet, accessing emails, or handling personal information.
02
Businesses and organizations: Organizations of all sizes require operating systems security to protect their sensitive data, intellectual property, and customer information. Cyberattacks can be highly damaging to businesses, leading to financial losses, reputational damage, and legal implications.
03
Government entities: Governments and public institutions handle vast amounts of sensitive information, including national security data, citizen records, and critical infrastructure systems. Maintaining robust operating systems security is crucial to safeguarding these assets from potential threats.
04
Healthcare providers: Healthcare organizations hold a large volume of sensitive patient data, including medical records, billing information, and personally identifiable information. Protecting this data through strong operating system security is vital to maintaining patient confidentiality and complying with privacy regulations.
Overall, operating systems security is essential for individuals, businesses, government entities, and organizations across various sectors to safeguard data, prevent unauthorized access, and mitigate cybersecurity risks.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
Can I create an electronic signature for the operating systems security in Chrome?
As a PDF editor and form builder, pdfFiller has a lot of features. It also has a powerful e-signature tool that you can add to your Chrome browser. With our extension, you can type, draw, or take a picture of your signature with your webcam to make your legally-binding eSignature. Choose how you want to sign your operating systems security and you'll be done in minutes.
How do I edit operating systems security straight from my smartphone?
The best way to make changes to documents on a mobile device is to use pdfFiller's apps for iOS and Android. You may get them from the Apple Store and Google Play. Learn more about the apps here. To start editing operating systems security, you need to install and log in to the app.
How do I fill out operating systems security using my mobile device?
On your mobile device, use the pdfFiller mobile app to complete and sign operating systems security. Visit our website (https://edit-pdf-ios-android.pdffiller.com/) to discover more about our mobile applications, the features you'll have access to, and how to get started.
What is operating systems security?
Operating systems security is the practice of protecting computer operating systems from unauthorized access, use, disclosure, disruption, modification, or destruction. It involves implementing various security measures to prevent potential threats and vulnerabilities.
Who is required to file operating systems security?
The responsibility to file operating systems security lies with the system administrators or IT department of an organization that uses computer operating systems. They are obligated to ensure the security of the operating systems in their environment.
How to fill out operating systems security?
Filling out operating systems security involves assessing the security needs of the operating systems, implementing necessary security controls, regularly monitoring for vulnerabilities, and patching the systems with security updates. It also includes documenting security policies, procedures, and incident response plans.
What is the purpose of operating systems security?
The purpose of operating systems security is to safeguard computer operating systems against potential security threats, unauthorized access, data breaches, and other forms of malicious activities. It ensures the confidentiality, integrity, and availability of sensitive information stored within the systems.
What information must be reported on operating systems security?
The information reported on operating systems security may include system vulnerabilities, security incidents, security policy compliance, access control measures, intrusion detection systems reports, and any other relevant security-related data.
Fill out your operating systems security online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Operating Systems Security is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.