Get the free Cyber & Data Breach Application CYBERSURE (Long Form)
Show details
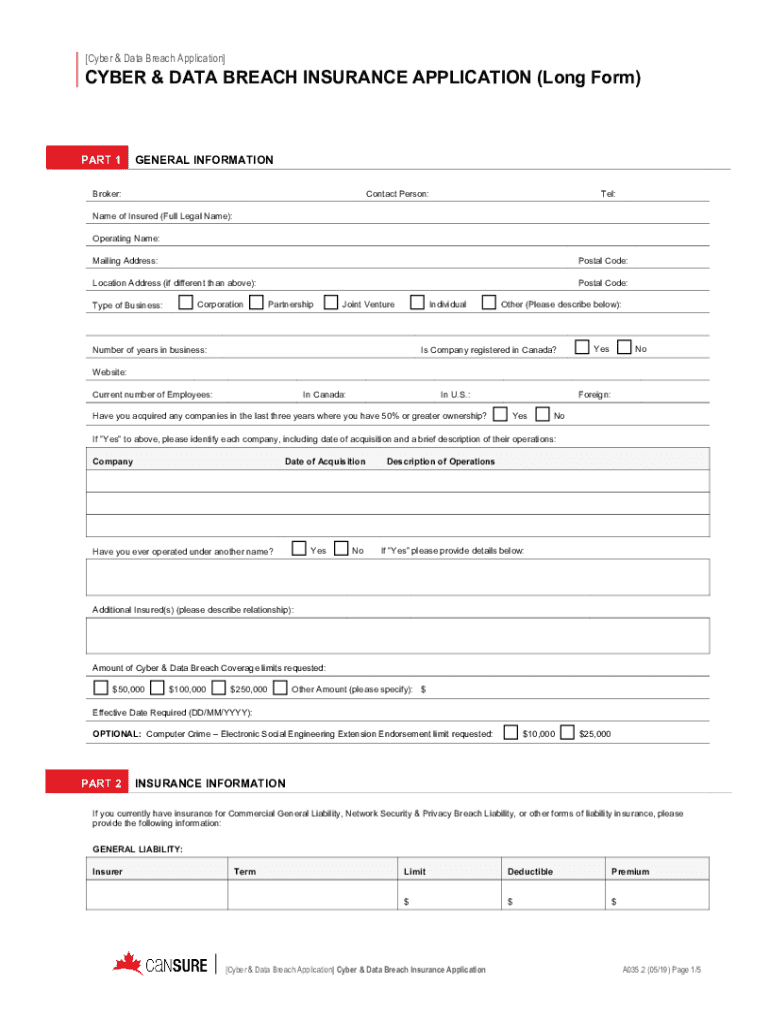
Cyber & Data Breach Application CENSURE (Long Form)For use with StandAlone policies or requests for limits above $250,000T: 604.685.6533 TOLL FREE T: 1.877.685.6533 F: 604.685.6554 E: info cansure.com
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign cyber ampamp data breach

Edit your cyber ampamp data breach form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your cyber ampamp data breach form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing cyber ampamp data breach online
Use the instructions below to start using our professional PDF editor:
1
Set up an account. If you are a new user, click Start Free Trial and establish a profile.
2
Prepare a file. Use the Add New button to start a new project. Then, using your device, upload your file to the system by importing it from internal mail, the cloud, or adding its URL.
3
Edit cyber ampamp data breach. Add and replace text, insert new objects, rearrange pages, add watermarks and page numbers, and more. Click Done when you are finished editing and go to the Documents tab to merge, split, lock or unlock the file.
4
Get your file. Select your file from the documents list and pick your export method. You may save it as a PDF, email it, or upload it to the cloud.
It's easier to work with documents with pdfFiller than you can have ever thought. Sign up for a free account to view.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out cyber ampamp data breach

How to fill out cyber ampamp data breach
01
To fill out a cyber data breach report, follow these steps:
02
Begin by identifying the type of data breach that occurred. This could include unauthorized access, malware infection, or insider threat, among others.
03
Gather all the relevant information about the breach, such as the date and time it occurred, the systems or devices affected, and the potential impact on the organization.
04
Document any immediate actions taken to mitigate the breach, such as disconnecting affected systems from the network or blocking compromised user accounts.
05
Identify the potential individuals or entities affected by the breach, including customers, employees, or partners.
06
Assess the severity and scope of the breach by determining the volume and sensitivity of the compromised data.
07
Analyze the root cause of the breach to identify any vulnerabilities or weaknesses in the organization's security controls.
08
Develop a detailed incident response plan to prevent similar breaches in the future, including steps for communication, remediation, and continuous monitoring.
09
Complete the cyber data breach report by summarizing the key findings, actions taken, and recommendations for further improvement.
10
Review the report for accuracy and ensure all necessary details are included before submitting it to the appropriate authorities or stakeholders.
11
Follow any legal or regulatory requirements for reporting the data breach, which may vary depending on the jurisdiction and industry.
12
By following these steps, you can effectively fill out a cyber data breach report and take necessary actions to address the incident.
Who needs cyber ampamp data breach?
01
Anyone who collects, stores, or processes sensitive data needs to be aware of cyber data breaches. This includes organizations of all sizes and industries, such as businesses, government agencies, healthcare providers, financial institutions, and educational institutions.
02
Cyber data breaches can have severe consequences, including financial losses, reputational damage, legal liabilities, and compromised customer trust. Therefore, anyone who handles sensitive data needs to understand the risks and take proactive measures to prevent and respond to data breaches.
03
Additionally, cybersecurity professionals, incident response teams, legal advisors, and IT personnel play a crucial role in managing cyber data breaches and ensuring compliance with relevant regulations.
04
By understanding who needs cyber data breach prevention and response, organizations can allocate resources and implement appropriate security measures to protect their data and avoid potential damages.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How do I edit cyber ampamp data breach online?
With pdfFiller, you may not only alter the content but also rearrange the pages. Upload your cyber ampamp data breach and modify it with a few clicks. The editor lets you add photos, sticky notes, text boxes, and more to PDFs.
Can I create an electronic signature for the cyber ampamp data breach in Chrome?
Yes, you can. With pdfFiller, you not only get a feature-rich PDF editor and fillable form builder but a powerful e-signature solution that you can add directly to your Chrome browser. Using our extension, you can create your legally-binding eSignature by typing, drawing, or capturing a photo of your signature using your webcam. Choose whichever method you prefer and eSign your cyber ampamp data breach in minutes.
Can I edit cyber ampamp data breach on an iOS device?
Create, edit, and share cyber ampamp data breach from your iOS smartphone with the pdfFiller mobile app. Installing it from the Apple Store takes only a few seconds. You may take advantage of a free trial and select a subscription that meets your needs.
What is cyber ampamp data breach?
A cyber and data breach refers to an incident where unauthorized individuals gain access to sensitive data, often leading to data theft, exposure, or alteration.
Who is required to file cyber ampamp data breach?
Organizations that experience a data breach involving personal data of individuals are generally required to file a report, including businesses, government entities, and non-profits.
How to fill out cyber ampamp data breach?
To fill out a cyber and data breach report, organizations should provide details about the breach, including the nature of the breach, types of data involved, number of individuals affected, and steps taken to mitigate the breach.
What is the purpose of cyber ampamp data breach?
The purpose of filing a cyber and data breach report is to ensure compliance with legal requirements, inform affected individuals, and enhance future data protection measures.
What information must be reported on cyber ampamp data breach?
The report typically must include the date of the breach, a description of the breach, types of data compromised, number of individuals affected, and actions taken to address the breach.
Fill out your cyber ampamp data breach online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Cyber Ampamp Data Breach is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.





















