Get the free Chronology of Data Breaches - Studylib
Show details
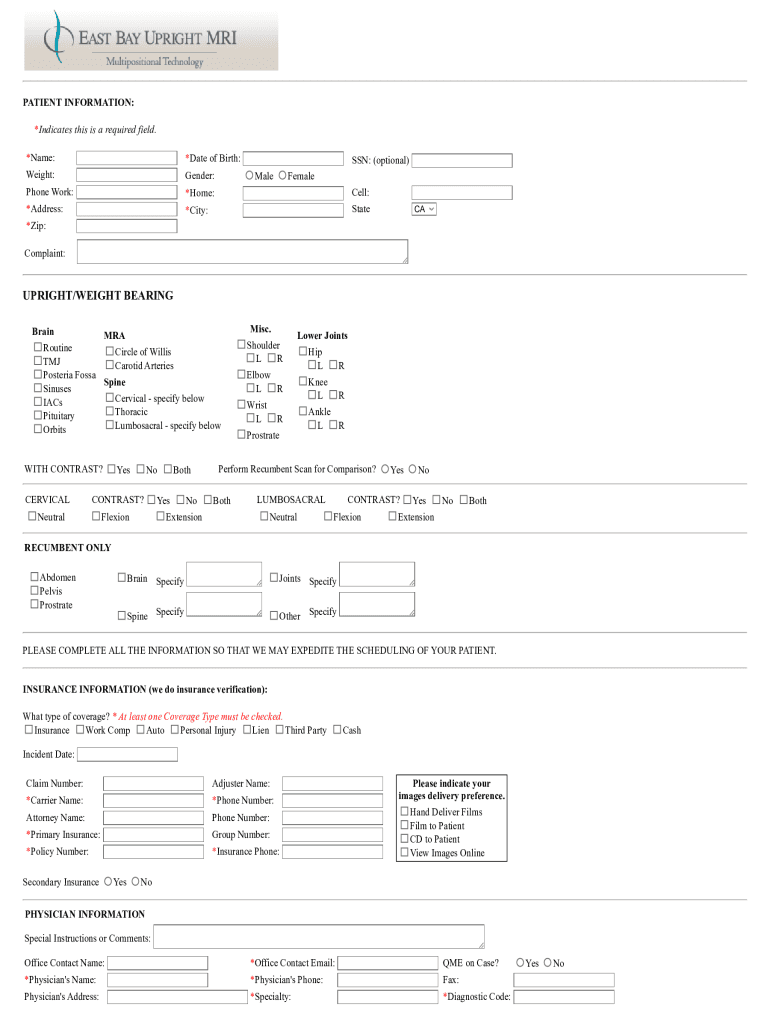
PATIENT INFORMATION: *Indicates this is a required field. *Name:*Date of Birth:Weight:Gender:Phone Work:*Home:Cell:*Address:*City:State SSN: (optional) MaleFemale CA×Zip: Complaint:UPRIGHT/WEIGHT
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign chronology of data breaches

Edit your chronology of data breaches form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your chronology of data breaches form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing chronology of data breaches online
Follow the guidelines below to take advantage of the professional PDF editor:
1
Log in to account. Start Free Trial and register a profile if you don't have one.
2
Prepare a file. Use the Add New button to start a new project. Then, using your device, upload your file to the system by importing it from internal mail, the cloud, or adding its URL.
3
Edit chronology of data breaches. Rearrange and rotate pages, add new and changed texts, add new objects, and use other useful tools. When you're done, click Done. You can use the Documents tab to merge, split, lock, or unlock your files.
4
Get your file. When you find your file in the docs list, click on its name and choose how you want to save it. To get the PDF, you can save it, send an email with it, or move it to the cloud.
pdfFiller makes dealing with documents a breeze. Create an account to find out!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out chronology of data breaches

How to fill out chronology of data breaches
01
To fill out chronology of data breaches, follow these steps:
02
Start by gathering all relevant information regarding the data breaches. This includes the dates when the breaches occurred, the types of data affected, the extent of the breach, and any actions taken to resolve the issue.
03
Create a chronological timeline of the data breaches, starting from the earliest incident to the most recent one.
04
Clearly outline the details of each data breach, including the specific vulnerabilities that led to the breach, any known sources or causes of the breach, and the impact it had on the affected individuals or organizations.
05
Include any legal or regulatory actions taken in response to the data breaches, such as lawsuits, penalties, or charges filed against the responsible parties.
06
Document the remedial measures implemented to address the breaches and prevent future incidents, such as enhanced data security protocols, staff training, or system upgrades.
07
Regularly update the chronology as new information becomes available or as additional data breaches occur.
08
Ensure the accuracy and integrity of the information by cross-referencing it with reliable sources and conducting thorough research.
09
Consider organizing the chronology in a clear and concise format, such as a table or timeline, to facilitate understanding and analysis of the data breaches.
10
Share the completed chronology with relevant stakeholders, such as internal management, legal teams, or regulatory authorities, as needed.
11
Periodically review and revise the chronology to reflect any changes or developments related to the data breaches.
Who needs chronology of data breaches?
01
A chronology of data breaches can be useful for various individuals and entities, including:
02
- Organizations and businesses that have experienced data breaches, as it provides a comprehensive overview of the incidents and helps in understanding the scope and impact of the breaches.
03
- Data protection officers and cybersecurity professionals, as it allows them to identify patterns, trends, or common vulnerabilities across multiple breaches, aiding in developing proactive security measures.
04
- Legal teams and regulatory authorities, as it serves as a reference for investigations, legal proceedings, or enforcement actions related to data breaches.
05
- Research institutions and academics studying data breaches, as it provides valuable data points for analysis, monitoring trends, and identifying areas of improvement in data security practices.
06
- Consumers and individuals concerned about their personal data, as it offers transparency and awareness about the frequency and magnitude of data breaches, enabling informed decisions regarding cybersecurity measures or service providers.
07
- Media outlets or journalists covering cybersecurity incidents, as it acts as a reliable source of information for reporting and creating awareness about data breaches.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I modify chronology of data breaches without leaving Google Drive?
People who need to keep track of documents and fill out forms quickly can connect PDF Filler to their Google Docs account. This means that they can make, edit, and sign documents right from their Google Drive. Make your chronology of data breaches into a fillable form that you can manage and sign from any internet-connected device with this add-on.
How do I make edits in chronology of data breaches without leaving Chrome?
Install the pdfFiller Chrome Extension to modify, fill out, and eSign your chronology of data breaches, which you can access right from a Google search page. Fillable documents without leaving Chrome on any internet-connected device.
How can I fill out chronology of data breaches on an iOS device?
Install the pdfFiller iOS app. Log in or create an account to access the solution's editing features. Open your chronology of data breaches by uploading it from your device or online storage. After filling in all relevant fields and eSigning if required, you may save or distribute the document.
What is chronology of data breaches?
Chronology of data breaches is a detailed timeline of all significant data breaches that have occurred within an organization.
Who is required to file chronology of data breaches?
Any organization or entity that has experienced a data breach is required to file chronology of data breaches.
How to fill out chronology of data breaches?
Chronology of data breaches should be filled out by documenting the date, time, type of breach, affected data, cause of breach, and actions taken in response.
What is the purpose of chronology of data breaches?
The purpose of chronology of data breaches is to provide a clear overview of all data breaches to assess the impact, identify patterns, and improve cybersecurity measures.
What information must be reported on chronology of data breaches?
Information such as date, time, type of breach, affected data, cause of breach, and actions taken in response must be reported on chronology of data breaches.
Fill out your chronology of data breaches online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Chronology Of Data Breaches is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.



















