Get the free www.cisa.govBomb-Threat-Procedure-ChecklistBOMB THREAT PROCEDURES BOMB THREAT CHECKL...
Show details
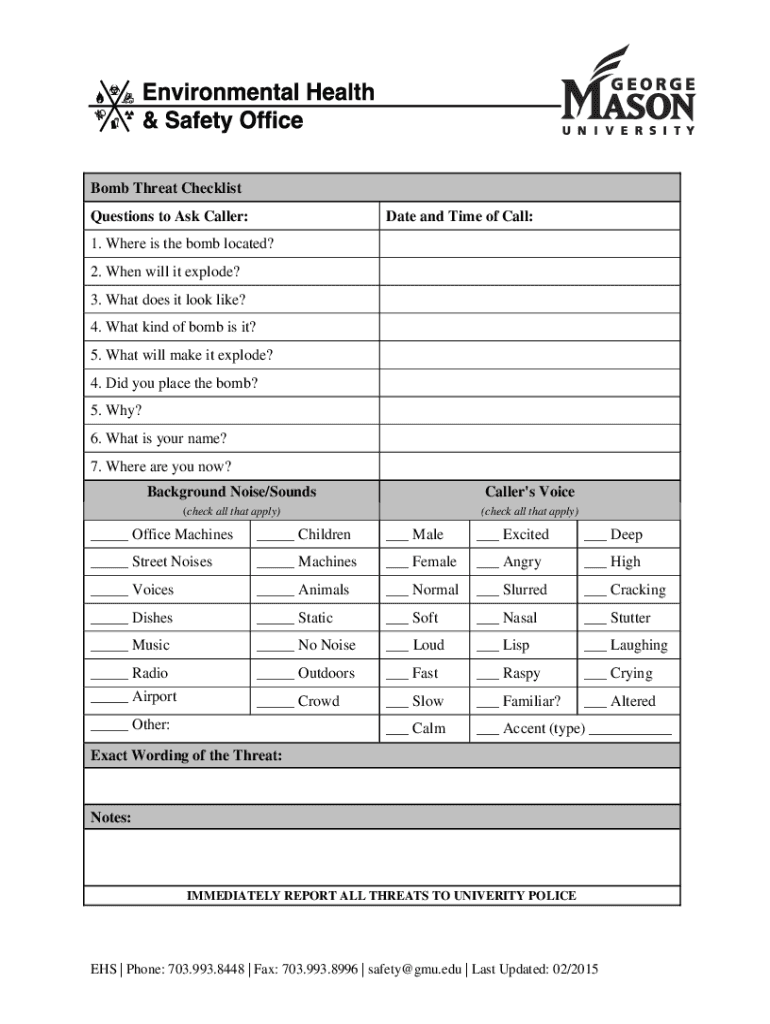
Bomb Threat Checklist Questions to Ask Caller:Date and Time of Call:1. Where is the bomb located? 2. When will it explode? 3. What does it look like? 4. What kind of bomb is it? 5. What will make
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb
Edit your wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.
Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb online
To use the professional PDF editor, follow these steps below:
1
Register the account. Begin by clicking Start Free Trial and create a profile if you are a new user.
2
Simply add a document. Select Add New from your Dashboard and import a file into the system by uploading it from your device or importing it via the cloud, online, or internal mail. Then click Begin editing.
3
Edit wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb. Rearrange and rotate pages, add and edit text, and use additional tools. To save changes and return to your Dashboard, click Done. The Documents tab allows you to merge, divide, lock, or unlock files.
4
Save your file. Choose it from the list of records. Then, shift the pointer to the right toolbar and select one of the several exporting methods: save it in multiple formats, download it as a PDF, email it, or save it to the cloud.
Dealing with documents is simple using pdfFiller. Try it now!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb
How to fill out wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb
01
To fill out the wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb checklist, follow these steps:
02
- Start by providing the necessary contact information, including the name, title, phone number, and email address of the person completing the checklist.
03
- Next, indicate the date and time of the bomb threat incident.
04
- Provide detailed information about the threat, such as the location of the bomb, the type of bomb, and any specific instructions or demands.
05
- Assess the credibility of the threat by considering factors like the source of the threat and any previous bomb threats.
06
- Coordinate with law enforcement authorities and follow their instructions for evacuations and searches.
07
- Document the actions taken during the bomb threat incident, including communication with authorities and evacuation procedures.
08
- Review and update the checklist regularly to ensure it remains up-to-date and effective in responding to bomb threats.
Who needs wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb?
01
Any organization or entity that wants to establish a proper bomb threat response procedure should use the wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb. This checklist is beneficial for schools, government agencies, public venues, offices, hospitals, and any other place where there is a potential risk of bomb threats. By having a comprehensive bomb threat procedure in place, organizations can ensure the safety of their employees, visitors, and assets in case of such emergencies.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I send wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb for eSignature?
When you're ready to share your wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb, you can send it to other people and get the eSigned document back just as quickly. Share your PDF by email, fax, text message, or USPS mail. You can also notarize your PDF on the web. You don't have to leave your account to do this.
How do I make edits in wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb without leaving Chrome?
Download and install the pdfFiller Google Chrome Extension to your browser to edit, fill out, and eSign your wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb, which you can open in the editor with a single click from a Google search page. Fillable documents may be executed from any internet-connected device without leaving Chrome.
How do I edit wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb straight from my smartphone?
The best way to make changes to documents on a mobile device is to use pdfFiller's apps for iOS and Android. You may get them from the Apple Store and Google Play. Learn more about the apps here. To start editing wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb, you need to install and log in to the app.
What is wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb?
The bomb threat procedures checklist provides guidance on how to respond to bomb threats.
Who is required to file wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb?
All individuals responsible for building security are required to file the bomb threat procedures checklist.
How to fill out wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb?
To fill out the bomb threat procedures checklist, provide detailed instructions on how to respond to a bomb threat.
What is the purpose of wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb?
The purpose of the bomb threat procedures checklist is to ensure that proper protocols are in place to respond to bomb threats.
What information must be reported on wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb?
The bomb threat procedures checklist must include contact information, evacuation procedures, and law enforcement notification protocols.
Fill out your wwwcisagovbomb-threat-procedure-checklistbomb threat procedures bomb online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Wwwcisagovbomb-Threat-Procedure-Checklistbomb Threat Procedures Bomb is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.





















