
Get the free Cyber Security PII Incident Report Form. Cyber Security PII Incident Report Form
Show details
US Department of Agriculture Security Operations Center Cybersecurity Incident Report Personally Identifiable Information (PIN) Incident This Cybersecurity Incident Report follows established guidelines
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign cyber security pii incident
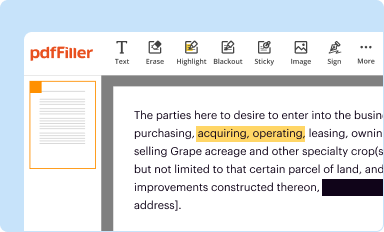
Edit your cyber security pii incident form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.
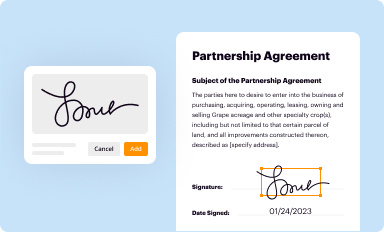
Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your cyber security pii incident form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit cyber security pii incident online
To use the services of a skilled PDF editor, follow these steps:
1
Register the account. Begin by clicking Start Free Trial and create a profile if you are a new user.
2
Upload a file. Select Add New on your Dashboard and upload a file from your device or import it from the cloud, online, or internal mail. Then click Edit.
3
Edit cyber security pii incident. Rearrange and rotate pages, add new and changed texts, add new objects, and use other useful tools. When you're done, click Done. You can use the Documents tab to merge, split, lock, or unlock your files.
4
Get your file. Select your file from the documents list and pick your export method. You may save it as a PDF, email it, or upload it to the cloud.
With pdfFiller, dealing with documents is always straightforward. Try it now!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out cyber security pii incident
How to fill out cyber security pii incident
01
To fill out a cyber security PII incident report, follow these steps:
02
Start by gathering all the necessary information related to the incident. This includes details about the affected individual (such as name, contact information, and any PII involved), the nature of the incident, and any evidence or documentation available.
03
Provide a detailed description of the incident, including how and when it occurred, the potential impact on the individual or organization, and any relevant background information.
04
Classify the severity of the incident based on predefined criteria or guidelines. This will help in determining the appropriate response and level of urgency.
05
Document any actions taken to mitigate the incident or prevent further harm. This may include notifying affected individuals, law enforcement, or relevant authorities.
06
Record any additional steps or measures taken to address the incident, such as implementing new security protocols or increasing monitoring.
07
Include any recommendations or suggestions for preventing similar incidents in the future.
08
Finally, ensure that the incident report is securely stored and accessible only to authorized personnel involved in the investigation or response process.
Who needs cyber security pii incident?
01
Cyber security PII incident reports are essential for any individual or organization that handles or stores Personally Identifiable Information (PII). This includes:
02
- Businesses and corporations that collect customer information for transactions or services
03
- Government agencies that deal with citizen records and sensitive data
04
- Healthcare organizations that handle medical records and personal health information
05
- Educational institutions that store student data and academic records
06
- Financial institutions that process financial transactions and store banking information
07
- Non-profit organizations that collect donor or member information
08
- Any individual or entity that is subject to data privacy regulations or laws
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How do I complete cyber security pii incident online?
pdfFiller makes it easy to finish and sign cyber security pii incident online. It lets you make changes to original PDF content, highlight, black out, erase, and write text anywhere on a page, legally eSign your form, and more, all from one place. Create a free account and use the web to keep track of professional documents.
Can I create an electronic signature for signing my cyber security pii incident in Gmail?
You may quickly make your eSignature using pdfFiller and then eSign your cyber security pii incident right from your mailbox using pdfFiller's Gmail add-on. Please keep in mind that in order to preserve your signatures and signed papers, you must first create an account.
How do I fill out the cyber security pii incident form on my smartphone?
The pdfFiller mobile app makes it simple to design and fill out legal paperwork. Complete and sign cyber security pii incident and other papers using the app. Visit pdfFiller's website to learn more about the PDF editor's features.
What is cyber security pii incident?
A cyber security PII incident refers to any occurrence where personally identifiable information (PII) is compromised, accessed, or disclosed without authorization due to a security breach, cyber attack, or negligence.
Who is required to file cyber security pii incident?
Organizations that collect, store, or process personal information are generally required to file a cyber security PII incident report, particularly if the incident affects individuals' personal data.
How to fill out cyber security pii incident?
To fill out a cyber security PII incident report, provide detailed information including the nature of the incident, the type and amount of PII impacted, the date of the incident, and steps taken to mitigate the damage and prevent future occurrences.
What is the purpose of cyber security pii incident?
The purpose of reporting a cyber security PII incident is to ensure transparency, facilitate investigation and remediation, protect affected individuals, and help authorities mitigate risks associated with data breaches.
What information must be reported on cyber security pii incident?
Information that must be reported includes the type of PII compromised, details of the incident, the number of affected individuals, the response actions taken, and contacts for follow-up.
Fill out your cyber security pii incident online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Cyber Security Pii Incident is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.


















