Get the free Table of De-Identification Techniques - San Jose State University
Show details
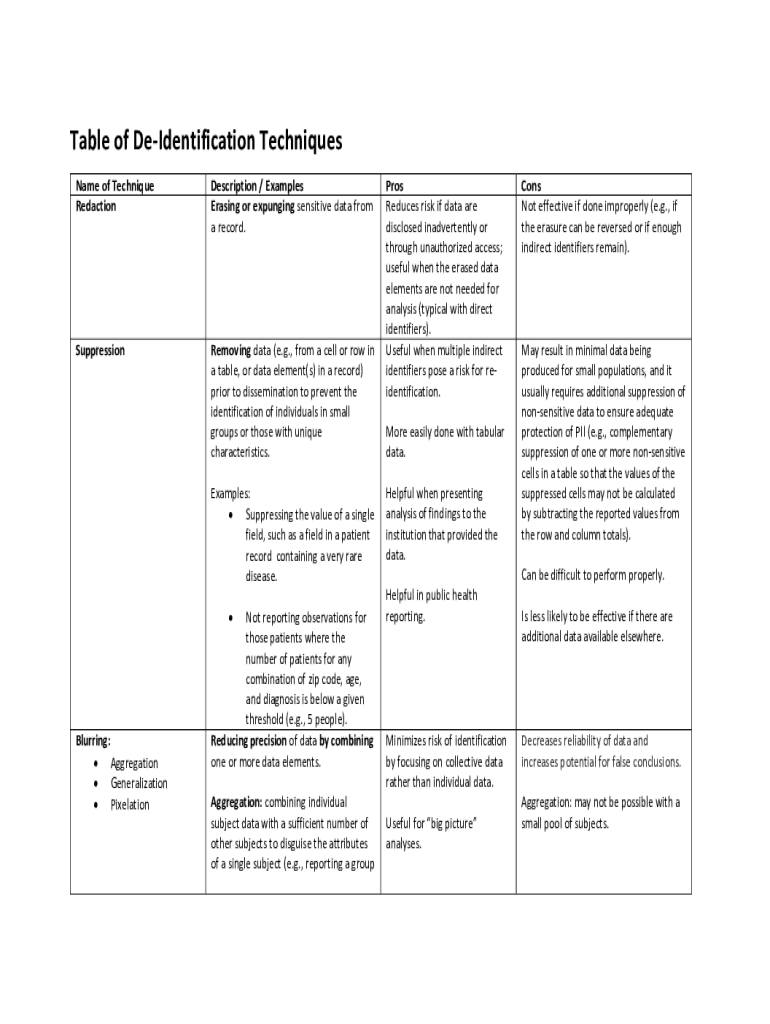
Table of Identification Techniques Name of Technique RedactionDescription / Examples Erasing or expunging sensitive data from a record. SuppressionRemoving data (e.g., from a cell or row in a table,
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign table of de-identification techniques

Edit your table of de-identification techniques form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your table of de-identification techniques form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit table of de-identification techniques online
To use the professional PDF editor, follow these steps:
1
Log in to your account. Click on Start Free Trial and register a profile if you don't have one.
2
Prepare a file. Use the Add New button to start a new project. Then, using your device, upload your file to the system by importing it from internal mail, the cloud, or adding its URL.
3
Edit table of de-identification techniques. Rearrange and rotate pages, add and edit text, and use additional tools. To save changes and return to your Dashboard, click Done. The Documents tab allows you to merge, divide, lock, or unlock files.
4
Get your file. Select the name of your file in the docs list and choose your preferred exporting method. You can download it as a PDF, save it in another format, send it by email, or transfer it to the cloud.
With pdfFiller, it's always easy to work with documents. Try it out!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out table of de-identification techniques

How to fill out table of de-identification techniques
01
Identify the data elements you want to de-identify.
02
Determine the de-identification techniques that best suit each data element.
03
Document the specific de-identification techniques used for each data element in the table.
04
Ensure compliance with data privacy regulations and guidelines while de-identifying the data.
Who needs table of de-identification techniques?
01
Organizations that handle sensitive or personal data and need to ensure compliance with privacy regulations.
02
Data protection officers and privacy professionals who are responsible for safeguarding data privacy.
03
Researchers who need to anonymize personal information for analysis purposes.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I send table of de-identification techniques for eSignature?
Once you are ready to share your table of de-identification techniques, you can easily send it to others and get the eSigned document back just as quickly. Share your PDF by email, fax, text message, or USPS mail, or notarize it online. You can do all of this without ever leaving your account.
How do I edit table of de-identification techniques online?
The editing procedure is simple with pdfFiller. Open your table of de-identification techniques in the editor. You may also add photos, draw arrows and lines, insert sticky notes and text boxes, and more.
How do I make edits in table of de-identification techniques without leaving Chrome?
table of de-identification techniques can be edited, filled out, and signed with the pdfFiller Google Chrome Extension. You can open the editor right from a Google search page with just one click. Fillable documents can be done on any web-connected device without leaving Chrome.
What is table of de-identification techniques?
The table of de-identification techniques is a structured compilation of various methods used to remove personally identifiable information from data sets to protect individual privacy.
Who is required to file table of de-identification techniques?
Organizations and entities that handle personal data, especially those subject to privacy regulations such as HIPAA or GDPR, are typically required to file the table of de-identification techniques.
How to fill out table of de-identification techniques?
To fill out the table of de-identification techniques, one must identify the specific de-identification methods used, provide examples of data processed, and describe the rationale for the chosen techniques.
What is the purpose of table of de-identification techniques?
The purpose of the table of de-identification techniques is to provide transparency in the data privacy practices of organizations and ensure compliance with relevant legal requirements for data protection.
What information must be reported on table of de-identification techniques?
The information that must be reported includes the types of de-identification techniques used, descriptions of how personal data is processed, and any risks associated with re-identification.
Fill out your table of de-identification techniques online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Table Of De-Identification Techniques is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.





















