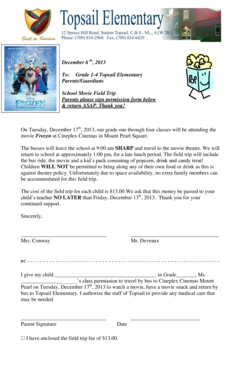
Get the free Security Protocols and Public Gathering Guidelines
Show details
The role of the Department of Planning and Construction is to help assess needs for and provide physical facilities to support the mission of Moore County Schools. The Operations Department constructs,
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign security protocols and public

Edit your security protocols and public form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your security protocols and public form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing security protocols and public online
Here are the steps you need to follow to get started with our professional PDF editor:
1
Create an account. Begin by choosing Start Free Trial and, if you are a new user, establish a profile.
2
Prepare a file. Use the Add New button. Then upload your file to the system from your device, importing it from internal mail, the cloud, or by adding its URL.
3
Edit security protocols and public. Replace text, adding objects, rearranging pages, and more. Then select the Documents tab to combine, divide, lock or unlock the file.
4
Save your file. Choose it from the list of records. Then, shift the pointer to the right toolbar and select one of the several exporting methods: save it in multiple formats, download it as a PDF, email it, or save it to the cloud.
With pdfFiller, it's always easy to work with documents.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out security protocols and public

How to fill out security protocols and public
01
Understand the specific security protocols and public policy requirements that need to be followed.
02
Gather all necessary information and documentation needed to complete the security protocols and public forms.
03
Carefully read each section of the security protocols and public forms, ensuring all information is accurate and complete.
04
Fill out each field on the security protocols and public forms accurately and truthfully.
05
Review the completed security protocols and public forms to check for any errors or missing information before submitting.
06
Submit the completed security protocols and public forms according to the specified instructions and deadlines.
Who needs security protocols and public?
01
Organizations that handle sensitive information and data.
02
Government agencies or departments that deal with national security.
03
Individuals or businesses that want to protect their assets and information from threats or breaches.
04
Any entity that wants to maintain a secure environment for their operations and stakeholders.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How do I modify my security protocols and public in Gmail?
You may use pdfFiller's Gmail add-on to change, fill out, and eSign your security protocols and public as well as other documents directly in your inbox by using the pdfFiller add-on for Gmail. pdfFiller for Gmail may be found on the Google Workspace Marketplace. Use the time you would have spent dealing with your papers and eSignatures for more vital tasks instead.
Can I edit security protocols and public on an iOS device?
Use the pdfFiller app for iOS to make, edit, and share security protocols and public from your phone. Apple's store will have it up and running in no time. It's possible to get a free trial and choose a subscription plan that fits your needs.
How do I complete security protocols and public on an iOS device?
Install the pdfFiller iOS app. Log in or create an account to access the solution's editing features. Open your security protocols and public by uploading it from your device or online storage. After filling in all relevant fields and eSigning if required, you may save or distribute the document.
What is security protocols and public?
Security protocols and public refer to the specific measures and guidelines put in place to ensure the safety and security of information and resources that are accessible to the general public.
Who is required to file security protocols and public?
All organizations and entities that handle sensitive information or provide public services are required to file security protocols and public.
How to fill out security protocols and public?
Security protocols and public can be filled out by following the guidelines and requirements set by the governing body or regulatory agency overseeing security measures.
What is the purpose of security protocols and public?
The purpose of security protocols and public is to protect sensitive information, prevent unauthorized access, and ensure the safety of public services and resources.
What information must be reported on security protocols and public?
Information such as security measures, encryption methods, data protection policies, and emergency response protocols must be reported on security protocols and public.
Fill out your security protocols and public online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Security Protocols And Public is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.