Get the free Notice of Security Breach to the HHS/Media - TFP Data Systems
Show details
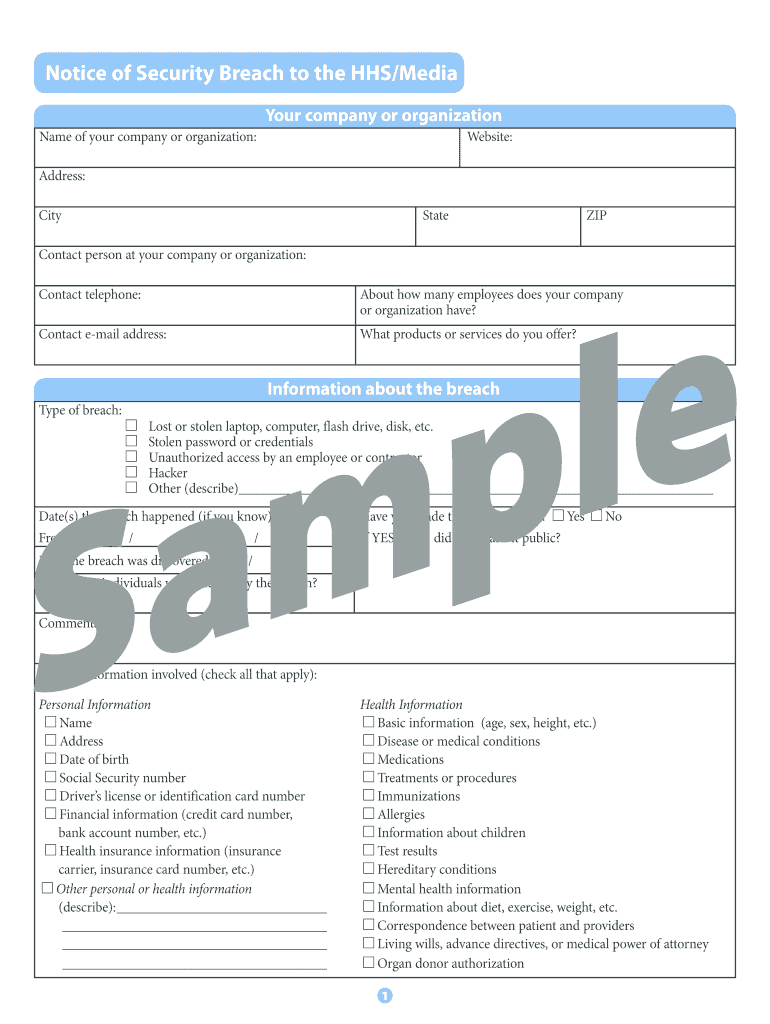
Notice of Security Breach to the HHS/Media Your company or organization Name of your company or organization: Website: Address: City State ZIP Contact person at your company or organization: Contact
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign notice of security breach

Edit your notice of security breach form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your notice of security breach form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit notice of security breach online
To use our professional PDF editor, follow these steps:
1
Create an account. Begin by choosing Start Free Trial and, if you are a new user, establish a profile.
2
Prepare a file. Use the Add New button. Then upload your file to the system from your device, importing it from internal mail, the cloud, or by adding its URL.
3
Edit notice of security breach. Rearrange and rotate pages, add new and changed texts, add new objects, and use other useful tools. When you're done, click Done. You can use the Documents tab to merge, split, lock, or unlock your files.
4
Save your file. Select it from your records list. Then, click the right toolbar and select one of the various exporting options: save in numerous formats, download as PDF, email, or cloud.
pdfFiller makes working with documents easier than you could ever imagine. Try it for yourself by creating an account!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out notice of security breach

How to fill out a notice of security breach:
01
Gather all relevant information: Start by collecting all the necessary details related to the security breach. This includes the date and time the breach occurred, the type of breach that occurred (e.g., data theft, unauthorized access), and any specific information that was compromised.
02
Determine the affected parties: Identify all the individuals or entities that may have been impacted by the security breach. This may include customers, employees, or any other stakeholders whose personal or sensitive information was exposed.
03
Include a clear and concise description of the breach: In the notice, provide a thorough explanation of how the security breach occurred. Use simple and non-technical language to ensure that the recipients can easily understand the nature and severity of the incident.
04
Provide contact information: Include contact details to ensure that affected parties can easily reach out for more information or assistance. This should include a dedicated helpline or email address, as well as a mailing address if necessary.
05
Explain the potential impact: Clearly outline the potential consequences and risks that may result from the security breach. This can include identity theft, financial loss, or any other relevant concerns. Offer guidance and resources on how affected parties can protect themselves or mitigate the possible effects of the breach.
06
Outline the next steps: Provide information on the actions you are taking to address the security breach. This can include steps you are taking to strengthen your security measures, conducting investigations, or cooperating with law enforcement agencies. Assure the affected parties that you are committed to resolving the issue and preventing future breaches.
Who needs a notice of security breach?
01
Affected individuals: Any individuals whose personal or sensitive information has been compromised as a result of the breach need to be notified. This includes customers, employees, or any other individuals whose data was exposed.
02
Regulatory bodies: Depending on the industry and jurisdiction, certain regulatory bodies may require organizations to report security breaches and provide notices. It is essential to understand and comply with any specific legal obligations regarding breach notifications.
03
Internal stakeholders: It is crucial to inform internal stakeholders such as management, relevant departments, or board members about the security breach. This ensures that appropriate measures can be taken to address the breach and prevent similar incidents in the future.
04
Business partners and service providers: If the breach involves any business partners, vendors, or service providers, they should be promptly notified to minimize any potential impact on their operations or data security.
05
Legal counsel and insurance providers: It is advisable to consult with legal counsel and notify insurance providers about the security breach. This can help in navigating legal obligations, accessing breach response services, and evaluating potential coverage for any resulting liabilities.
Note: It is crucial to consult with legal and cybersecurity professionals to ensure compliance with applicable laws and regulations, as breach notification requirements may vary depending on the jurisdiction and industry. The provided information serves as a general guideline and should not be considered as legal advice.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is notice of security breach?
Notice of security breach is a formal notification given to individuals or authorities when sensitive information has been compromised.
Who is required to file notice of security breach?
Businesses, organizations, or individuals who experience a security breach involving personal information are required by law to file a notice of security breach.
How to fill out notice of security breach?
Notice of security breach should include details of the breach, the type of information exposed, the number of individuals affected, and steps taken to mitigate the damage.
What is the purpose of notice of security breach?
The purpose of notice of security breach is to inform individuals whose personal information may have been compromised, so they can take steps to protect themselves from potential harm.
What information must be reported on notice of security breach?
Information reported on notice of security breach typically includes the date and nature of the breach, types of information affected, number of individuals impacted, and contact information for further inquiries.
How can I manage my notice of security breach directly from Gmail?
The pdfFiller Gmail add-on lets you create, modify, fill out, and sign notice of security breach and other documents directly in your email. Click here to get pdfFiller for Gmail. Eliminate tedious procedures and handle papers and eSignatures easily.
Can I edit notice of security breach on an iOS device?
Create, edit, and share notice of security breach from your iOS smartphone with the pdfFiller mobile app. Installing it from the Apple Store takes only a few seconds. You may take advantage of a free trial and select a subscription that meets your needs.
Can I edit notice of security breach on an Android device?
With the pdfFiller mobile app for Android, you may make modifications to PDF files such as notice of security breach. Documents may be edited, signed, and sent directly from your mobile device. Install the app and you'll be able to manage your documents from anywhere.
Fill out your notice of security breach online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Notice Of Security Breach is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.