Get the free Wireless access control - The evolution starts here
Show details
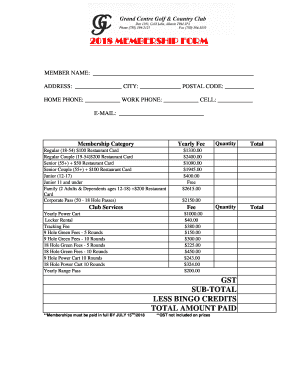
Period TechnologyWireless access control The evolution starts here2aperiotechnology.com.contents Period System Overview Application45 Key Features Hub Communication Period ComponentsAU100 Series Escutcheon610C100
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign wireless access control

Edit your wireless access control form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your wireless access control form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit wireless access control online
To use our professional PDF editor, follow these steps:
1
Create an account. Begin by choosing Start Free Trial and, if you are a new user, establish a profile.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit wireless access control. Text may be added and replaced, new objects can be included, pages can be rearranged, watermarks and page numbers can be added, and so on. When you're done editing, click Done and then go to the Documents tab to combine, divide, lock, or unlock the file.
4
Save your file. Select it from your records list. Then, click the right toolbar and select one of the various exporting options: save in numerous formats, download as PDF, email, or cloud.
With pdfFiller, dealing with documents is always straightforward. Try it now!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out wireless access control

How to fill out wireless access control:
01
Start by gathering all the necessary equipment and documentation. This may include the access control system itself, wireless access points, user manuals, and any other relevant materials.
02
Familiarize yourself with the specific instructions provided by the manufacturer or service provider. This will ensure that you follow the correct process for setting up and configuring wireless access control.
03
Begin by physically installing the wireless access points in the desired locations. These access points will create the wireless network that will be used for access control.
04
Connect the access points to the central access control system using the provided cables and connectors. Ensure that the connections are secure and properly aligned.
05
Power on the access control system and access points. Follow the manufacturer's instructions on how to properly power up the devices.
06
Access the control system's configuration interface either through a web browser or a dedicated software application. This interface will allow you to define and manage access control policies, user permissions, and other settings.
07
Configure the wireless access control system according to your specific requirements. This may involve setting up user accounts, assigning access levels, creating time schedules, or defining any other access control rules.
08
Test the wireless access control system to ensure its proper functionality. This includes verifying that users can successfully authenticate and gain access to the network, as well as checking for any potential issues or errors.
09
Once the system is set up and tested, document all the configuration settings and keep a backup of the configuration files. This will help in case of any future system changes or troubleshooting needs.
Who needs wireless access control?
01
Organizations with multiple access points and a large number of users require wireless access control to ensure secure and controlled access to their network.
02
Businesses that deal with sensitive data, such as financial institutions, healthcare providers, or government agencies, rely on wireless access control to protect their information from unauthorized access.
03
Educational institutions, including schools and universities, often implement wireless access control to regulate internet access for students, staff, and visitors.
04
Retail stores and shopping centers use wireless access control to manage access to their Wi-Fi networks, provide guest Wi-Fi services, and track customer behavior.
05
Hotels, resorts, and hospitality establishments utilize wireless access control to offer secure Wi-Fi access to guests while protecting their network infrastructure.
06
Industrial facilities and manufacturing plants employ wireless access control to secure their wireless networks, ensuring that only authorized personnel can connect to critical systems and devices.
07
Residential buildings and apartment complexes often install wireless access control to manage access to shared Wi-Fi networks, ensuring a reliable and secure internet connection for residents.
08
Public venues such as airports, stadiums, and conference centers utilize wireless access control to manage and optimize network performance while maintaining security for all users.
09
Healthcare facilities, including hospitals and clinics, rely on wireless access control to implement secure Wi-Fi networks for staff, patients, and guests, complying with regulations and protecting sensitive patient data.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is wireless access control?
Wireless access control is a security system that uses wireless technology to manage and regulate access to a property or facility.
Who is required to file wireless access control?
Any organization or individual that wants to implement a wireless access control system.
How to fill out wireless access control?
Wireless access control can be filled out by configuring the settings through a software interface, inputting user information and access privileges.
What is the purpose of wireless access control?
The purpose of wireless access control is to enhance security by controlling who can access a property or facility and when.
What information must be reported on wireless access control?
Information such as user identification, access permissions, time of access, and any access control events.
Can I create an eSignature for the wireless access control in Gmail?
You can easily create your eSignature with pdfFiller and then eSign your wireless access control directly from your inbox with the help of pdfFiller’s add-on for Gmail. Please note that you must register for an account in order to save your signatures and signed documents.
How do I fill out the wireless access control form on my smartphone?
On your mobile device, use the pdfFiller mobile app to complete and sign wireless access control. Visit our website (https://edit-pdf-ios-android.pdffiller.com/) to discover more about our mobile applications, the features you'll have access to, and how to get started.
How do I fill out wireless access control on an Android device?
On an Android device, use the pdfFiller mobile app to finish your wireless access control. The program allows you to execute all necessary document management operations, such as adding, editing, and removing text, signing, annotating, and more. You only need a smartphone and an internet connection.
Fill out your wireless access control online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Wireless Access Control is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.