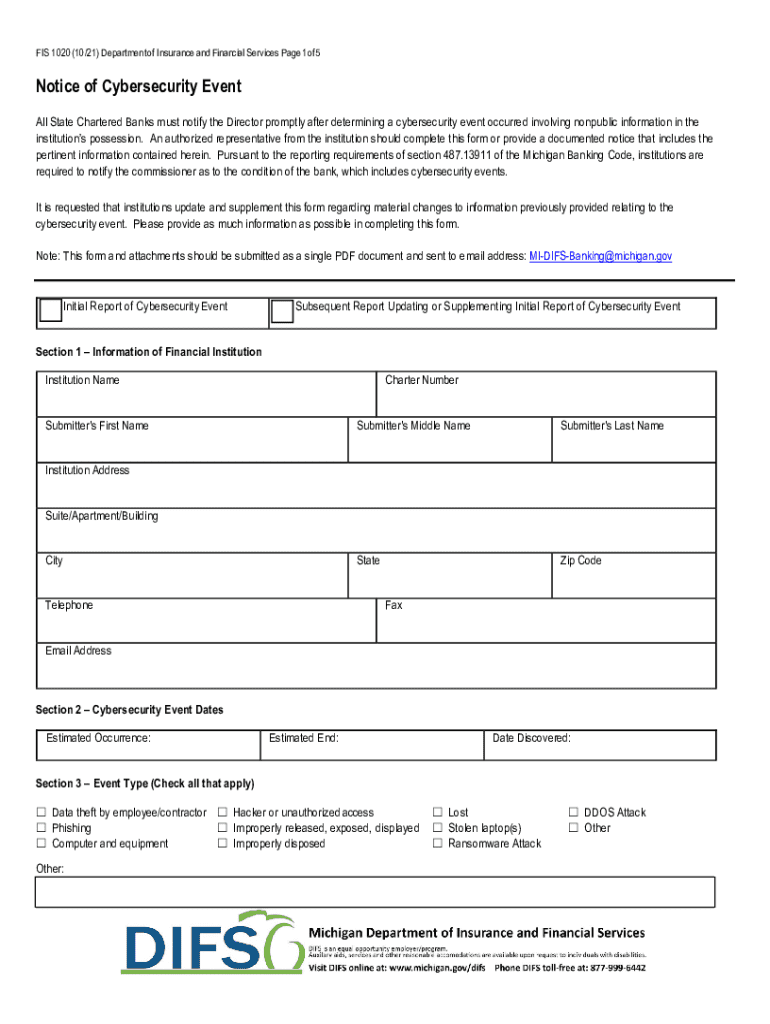
Get the free Notice of Cybersecurity Event
Get, Create, Make and Sign notice of cybersecurity event



How to edit notice of cybersecurity event online
Uncompromising security for your PDF editing and eSignature needs
How to fill out notice of cybersecurity event

How to fill out notice of cybersecurity event
Who needs notice of cybersecurity event?
Comprehensive Guide to the Notice of Cybersecurity Event Form
Understanding cybersecurity events
A cybersecurity event refers to any occurrence that potentially indicates a breach of information security policies or an invasion of an organization’s information systems. This can include unauthorized access, data compromise, or even disruptions caused by malicious software. Cybersecurity events can manifest in various forms, necessitating swift identification and appropriate response.
Types of cybersecurity events include:
The importance of reporting cybersecurity events cannot be overstated. Timely reporting not only helps organizations respond effectively but also protects stakeholders, complies with legal obligations, and enhances overall security posture.
Overview of the notice of cybersecurity event form
The notice of cybersecurity event form serves as a structured template for documenting and reporting cybersecurity incidents. Its primary purpose is to streamline the reporting process, ensuring that all necessary information is collected in a standardized manner, which aids in incident management and response.
Who needs to use this form? Individuals who have witnessed or been affected by a cybersecurity event and teams within organizations tasked with incident response should utilize it. The form is crucial for IT security personnel, compliance officers, and management, as it fosters organized communication about security breaches.
Key benefits of utilizing the form include:
Preparing to complete the notice of cybersecurity event form
Before filling out the notice of cybersecurity event form, it’s essential to identify relevant information required for effective reporting. This includes comprehensive details about the cyber incident, such as how the breach occurred, what vulnerabilities were exploited, and any immediate repercussions.
Gathering supporting documentation is crucial. Key items to collect include:
Additionally, organizations must ensure compliance with regulations such as the General Data Protection Regulation (GDPR). Understanding the legal implications of a cybersecurity event is critical for mitigating liability.
Step-by-step instructions for filling out the form
Accessing the notice of cybersecurity event form on pdfFiller is straightforward. Begin by visiting the platform and locating the specific template designed for reporting cybersecurity incidents.
The form typically includes the following sections, which must be completed thoroughly:
Tips for effective reporting
When preparing your report, using clear and concise language is vital. Ensure that your descriptions are straightforward, allowing for easy comprehension. Highlighting key points succinctly can enhance the report's effectiveness and facilitate quick understanding of the incident by stakeholders.
Additionally, make sure to avoid common mistakes such as:
Editing and collaborating on the form
Utilizing pdfFiller’s features can significantly ease your document management tasks. The platform offers an assortment of editing tools that allow users to customize their forms or reports effectively. Adding comments, annotations, or alterations can ensure that the document accurately reflects the incident details.
Collaboration is another robust feature of pdfFiller. Team members can work together in real-time, making edits or suggesting changes directly within the form. This cooperative approach is essential in managing the intricacies of cybersecurity incidents.
Digital signature options enable users to eSign the document easily, affirming its legitimacy while also streamlining the approval process.
Managing your document post-submission
Once the notice of cybersecurity event form is submitted, managing your document effectively is crucial. Tracking the status of your report ensures you remain informed about follow-up actions or additional requirements from stakeholders.
Storing and archiving reports securely is vital for maintaining compliance and protecting sensitive information. Best practices for document retention include:
Frequently asked questions (FAQs)
Common queries related to the notice of cybersecurity event form can include various aspects, such as how to report an incident, the timeline for response, and the types of incidents that must be reported.
In case of form submission issues, troubleshooting steps can involve checking internet connectivity, ensuring the form is correctly filled out, and verifying user access permissions.
Additional support and resources
For further assistance regarding the notice of cybersecurity event form, you can contact the support team through pdfFiller. Comprehensive guidelines and relevant policies can significantly help users understand reporting requirements.
Accessing additional cybersecurity resources and tools on pdfFiller can further enhance your knowledge and preparedness for managing cybersecurity events effectively.






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How do I modify my notice of cybersecurity event in Gmail?
How do I make edits in notice of cybersecurity event without leaving Chrome?
How do I edit notice of cybersecurity event on an Android device?
What is notice of cybersecurity event?
Who is required to file notice of cybersecurity event?
How to fill out notice of cybersecurity event?
What is the purpose of notice of cybersecurity event?
What information must be reported on notice of cybersecurity event?
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.















