Get the free this form is used to request access to blackout data for discretion add comments and more msockid 309f288769c46228034e3e1d683d63cc
Get, Create, Make and Sign this form is used



How to edit this form is used online
Uncompromising security for your PDF editing and eSignature needs
How to fill out this form is used

How to fill out data center access request
Who needs data center access request?
Understanding the Data Center Access Request Form: A Comprehensive Guide
Understanding the data center access request form
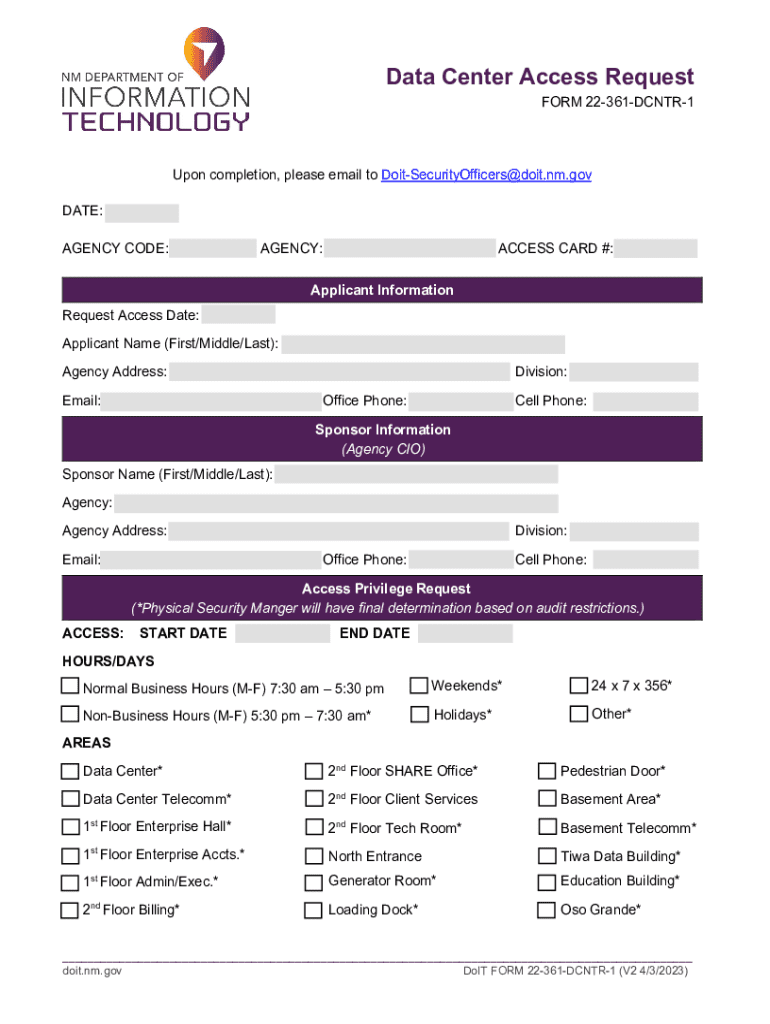
The data center access request form is a formal document that enables individuals or teams to request access to a data center. This essential form serves multiple purposes, primarily aimed at ensuring the secure and regulated management of access to sensitive environments where critical data and infrastructure are housed. By requiring thorough details about the individual seeking access, this form minimizes risks and enhances security protocols within the facility.
Secure access to data centers is paramount due to the nature of the information stored and managed in these facilities. Providing access to unauthorized personnel can lead to data breaches or operational disruptions. Therefore, a well-structured access request process is crucial for maintaining integrity and compliance with data protection regulations.
Who should use the data center access request form?
The data center access request form is intended for a variety of audiences, primarily those who are connectively involved in the management and utilization of data center resources. This includes IT teams and system administrators responsible for maintaining data integrity, project managers requiring temporary access for specific tasks, and external partners or vendors who need access for maintenance and support.
Understanding eligibility criteria for access is essential. While IT personnel typically have unrestricted access, external partners may undergo a more rigorous approval process. It's crucial to adhere to the governing organization’s protocols to streamline operations while ensuring security.
Detailed requirements for completing the form
When filling out the data center access request form, there are necessary documentation requirements that must accompany the request. First, personal identification must be provided, which often includes a government-issued ID or an employee number. This documentation verifies that the person requesting access is duly authorized to do so.
Additionally, project approval letters from relevant stakeholders may be necessary to substantiate the request for access. This requirement ensures that the access is directly tied to specific operational needs and is not granted without proper justification.
Step-by-step guide to filling out the data center access request form
Filling out the data center access request form can be straightforward if approached systematically. The first step involves gathering all required information. Compile necessary identification, project details, and any items that substantiate your access request. This preparatory work can streamline the form-filling process.
Next, accurately fill out your personal information, ensuring there are no discrepancies that could delay approval. It's essential to specify your access needs clearly—describe what kind of access you require and why it is necessary. Providing a robust justification can significantly impact the approval process.
Tips for a successful data center access request
To enhance the chances of a successful data center access request, it is vital to avoid common pitfalls. One major error is submitting incomplete information, which can lead to unnecessary delays. Another frequent mistake is lacking the proper documentation that might be requested at a later stage. Therefore, being thorough in your preparation is essential.
Some best practices include crafting clear justification statements. Articulate precisely why access is required, how long it will be needed, and the tasks intended during the access period. Additionally, ensure that requests are submitted timely, especially if they pertain to time-sensitive projects.
Managing your access request
After submitting your data center access request form, tracking its status is essential for planning purposes. Most organizations will provide a way to check the current status of your request, which can be crucial for keeping projects on track and ensuring that access is granted when needed.
If your request is denied, understand what steps to take next. It may be useful to gather feedback on why the request was denied. Knowing the reasons allows you to address them for a reapplication. Familiarize yourself with the appeal process, as this may provide another avenue to gain access. In urgent situations, inquire about the possibility of expediting your access request.
Termination of access: a necessary process
Access termination is a critical aspect of maintaining data center security. When access is no longer needed or if an employee leaves the organization, it is essential to have a clear process in place for terminating access promptly. This step is crucial in upholding security protocols and preventing unauthorized access.
Notifying relevant parties is paramount during the termination process. This includes informing security personnel and your direct supervisor to ensure that all systems are updated accordingly. Revoking access ensures compliance with data management frameworks and safeguards against potential security breaches.
Frequently asked questions (FAQs)
When using the data center access request form, you might have several questions. For instance, if you need access for a different purpose than stated, it’s generally best to submit a new request specifying the new intent. This ensures that the request is evaluated based on the correct context.
The timeframe for approval can vary depending on the organization; however, it’s common for a typical request to take anywhere from one to five business days. Submitting your request well in advance of any anticipated need is advisable to avoid disruptions. Lastly, once submitted, most forms are generally not editable. It’s wisest to ensure all information is accurate before sending your request.
Interactive tools and features for online requests
Utilizing pdfFiller for your data center access request form can significantly enhance your document management experience. With its array of online document management features, users can create, edit, and manage access requests smoothly from any location. This tool not only allows for immediate document access but also ensures compliance with organizational standards.
Key features of pdfFiller that can improve the completion and submission of the access request form include eSigning capabilities for quick authorizations and collaboration tools that facilitate team submissions. Document templates are also available for various access requests, streamlining the process even further by allowing users to build upon established formats.
Conclusion
In conclusion, understanding and correctly utilizing the data center access request form is integral for both individuals and organizations. This guide has provided a thorough breakdown of the form's importance, filling requirements, and tips for ensuring successful submission. Effective access management within data centers is not just a task but a vital component supporting overall data security and regulatory compliance.
As you navigate the access request process, keep in mind the importance of proper documentation, justification for access, and the timely submission of requests. By leveraging tools like pdfFiller, users can streamline these processes significantly, ensuring compliance and security are always at the forefront.






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I manage my this form is used directly from Gmail?
How can I edit this form is used on a smartphone?
Can I edit this form is used on an iOS device?
What is data center access request?
Who is required to file data center access request?
How to fill out data center access request?
What is the purpose of data center access request?
What information must be reported on data center access request?
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.