Get the free Cyber Risk Management Guide for Our Agents and Brokers
Get, Create, Make and Sign cyber risk management guide



How to edit cyber risk management guide online
Uncompromising security for your PDF editing and eSignature needs
How to fill out cyber risk management guide

How to fill out cyber risk management guide
Who needs cyber risk management guide?
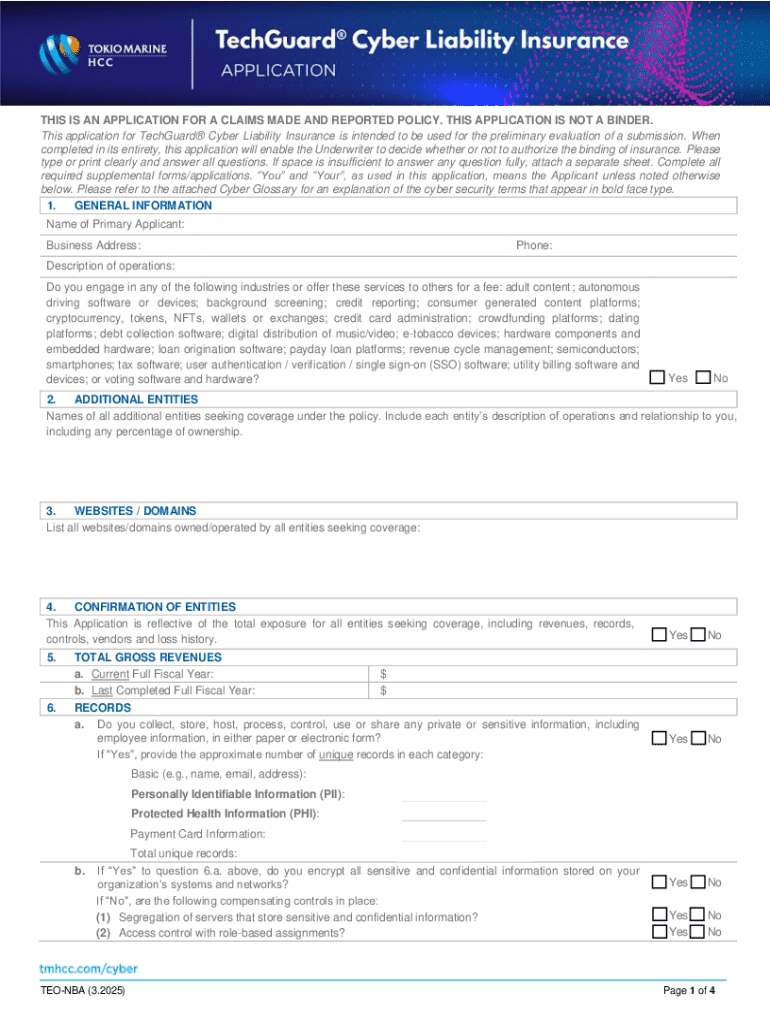
Cyber Risk Management Guide Form
Understanding cyber risk management
Cyber risk management is defined as the process of identifying, assessing, and mitigating risks that impact the confidentiality, integrity, and availability of information systems. Its importance is underscored by the rapid digital transformation affecting all organizations today, where cyber threats are increasingly sophisticated and pervasive. Understanding these risks is crucial for organizations looking to safeguard their assets, maintain customer trust, and comply with legal regulations.
Key components of cyber risk include threat identification, vulnerability assessment, risk analysis, and the implementation of effective controls. In a world where cyber attacks can lead to significant financial loss, brand damage, and regulatory penalties, effective cyber risk management is not just optional—it's a necessity.
The cyber risk management process
The cyber risk management process begins with the identification of cyber security risks, which involves various techniques and tools to pinpoint potential threats. Organizations can utilize tools such as vulnerability scanners, security information and event management (SIEM) systems, and threat intelligence platforms to assist in risk identification.
Once risks have been identified, the next step is the assessment of cyber security risks. This involves evaluating the likelihood of each risk materializing and its potential impact on the organization. Risk assessment methodologies can be classified into qualitative approaches, where descriptive categories are used, and quantitative methods, employing numerical values to assess risk severity.
Developing a cybersecurity risk management strategy
Creating a comprehensive cyber risk management plan is essential for effectively mitigating risks. A well-structured plan should include essential elements such as an overview of the risk landscape, prioritized risks, and specific mitigation strategies. Aligning this plan with business objectives ensures that cybersecurity measures support broader organizational goals.
Setting up effective risk mitigation measures requires a mix of technical and administrative strategies. Organizations must select appropriate measures based on their risk profile, available resources, and regulatory landscape. Common techniques include firewalls, encryption, employee training, and incident response plans.
Risk management frameworks
Various standards and frameworks provide structured approaches to cyber risk management. Prominent ones include the NIST Cybersecurity Framework and ISO 27001. Each framework offers guidelines on assessing and managing cyber risks effectively, and choosing the right one depends on your organization’s specific needs, industry standards, and regulatory requirements.
Implementation of these frameworks involves key steps such as conducting a current state assessment, establishing a governance structure, creating an implementation plan, and regularly reviewing processes for continual improvement. These frameworks enable organizations to adopt a structured approach toward cyber resilience.
Roles and responsibilities in cyber risk management
Internal compliance and audit teams play crucial roles in the risk management process by ensuring adherence to policies and regulations. Establishing best practices for collaboration between these teams and IT security personnel fosters a holistic approach to managing cyber risks.
Clearly defining these roles within teams enhances accountability and facilitates better communication, which is vital for effective risk management.
Tools for effective cyber risk management
To enhance the efficiency of cyber risk management efforts, leveraging collaborative and communication tools is crucial. When selecting risk management software, look for features that support ease of use, security, reporting capabilities, and integration with existing systems. Cloud-based platforms facilitate document management, offering benefits like accessibility and real-time collaboration.
Additionally, incorporating risk management analytics and reporting tools allows for data-driven decision making. Creating regular reports not only keeps stakeholders informed but also illustrates the effectiveness of implemented risk strategies and compliance with regulatory standards.
Continuous monitoring and improvement
Continuous monitoring is vital for effective cyber risk management, as new threats evolve and emerge frequently. Ongoing risk assessment practices ensure that your risk management strategy remains relevant and effective. Tools such as automated risk assessment platforms can simplify the process of monitoring and evaluating risks over time.
Incorporating feedback into your risk management practices is equally critical. Looping feedback allows organizations to refine their strategies based on lessons learned from incidents and assessments, which ultimately enhances the overall cybersecurity posture.
Advanced cyber risk management techniques
As cyber threats continue to evolve, organizations must navigate complexities in cyber risk landscapes. Common challenges include sophisticated attacks such as ransomware, as well as internal threats from employees. Analyzing real-world incidents, like major data breaches, teaches valuable lessons that can refine risk management strategies.
Advanced techniques like threat modeling enable organizations to anticipate and analyze potential threats, while vulnerability analysis identifies weaknesses that could be targeted by cybercriminals. Tools such as threat modeling software can provide frameworks for anticipating attack vectors and adjusting defenses accordingly.
Measuring cyber risk management maturity
Assessing your organization's cybersecurity practices can provide insights into its risk management maturity. Self-assessment tools and methodologies help determine the effectiveness of current practices, highlighting strengths and areas for improvement. Creating maturity models allows for targeted improvements, ensuring that as threats evolve, so too does your organization's risk management strategy.
Implementing improvement pathways based on maturity assessments fosters a culture of continuous learning and adaptation, which is crucial for maintaining a robust cybersecurity framework.
Practical steps for document management in cyber risk
Using pdfFiller for creating and managing cyber risk management documentation streamlines the entire process. The platform’s e-signing features enhance the efficiency of document finalization, while collaboration tools enable teams to work together seamlessly.
Interactive tools on pdfFiller further enhance user experience and engagement. By providing educational content directly related to risk management documentation, teams can improve their understanding while managing essential documents.






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I send cyber risk management guide for eSignature?
Can I sign the cyber risk management guide electronically in Chrome?
How do I edit cyber risk management guide on an iOS device?
What is cyber risk management guide?
Who is required to file cyber risk management guide?
How to fill out cyber risk management guide?
What is the purpose of cyber risk management guide?
What information must be reported on cyber risk management guide?
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.






















