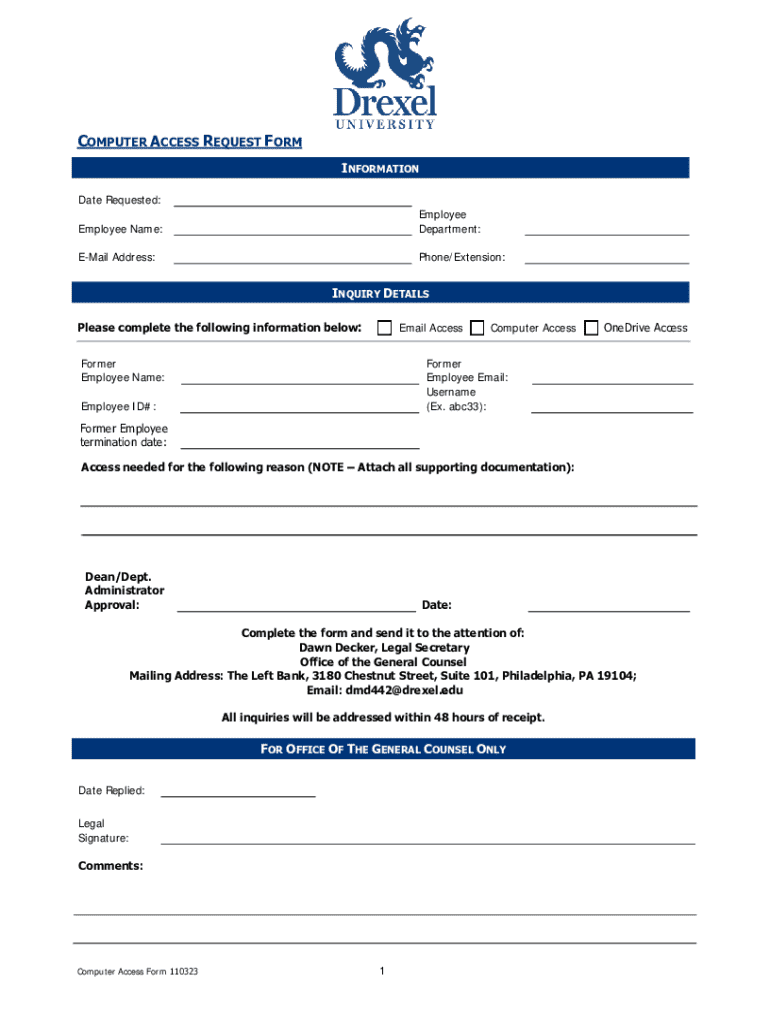
Get the free Computer Access Request Form
Get, Create, Make and Sign computer access request form



Editing computer access request form online
Uncompromising security for your PDF editing and eSignature needs
How to fill out computer access request form

How to fill out computer access request form
Who needs computer access request form?
Understanding the Computer Access Request Form
Understanding the computer access request form
A computer access request form is a formal document used by organizations to regulate access to their computer systems and data. This form aims to ensure only authorized personnel can access sensitive information, preventing unauthorized use and potential data breaches. In today's data-driven environments, where information security is paramount, an effective access control mechanism is essential.
Access control is critical for any organization, as it helps to safeguard confidential materials, comply with legal regulations, and maintain the overall integrity of data management systems. Without proper controls, organizations risk exposing themselves to cybersecurity threats, resulting in financial and reputational damage.
Key elements of the computer access request form
A well-structured computer access request form should contain several key components to effectively gather all necessary information. The first crucial section includes the requestor's information, such as their name, department, and contact details. This helps the reviewing authority to verify the individual's identity and role within the organization.
Next, it should specify the type of access needed. Common access levels might include read-only access, administrative rights, or system configuration permissions, depending on the user's responsibilities. Additionally, the form should outline the duration of access required. This can vary from a few hours for temporary access to ongoing access for permanent employees.
How to fill out the computer access request form effectively
Filling out a computer access request form correctly is vital to avoiding delays or rejections. Start by carefully entering your personal information in the requestor section. Ensure that all details are accurate and up to date, as errors can lead to complications in the approval process.
Next, clearly specify the type of access you are requesting. Define whether you need administrative access, read-only access, or specific application access. Providing this detail helps administrators understand the request better and enables them to assess the implications of granting such access.
Understanding organizational policies regarding access requests can save you time in the long run. Familiarize yourself with specific guidelines, as these might outline what information is mandatory or any templates that are preferred.
Editing and managing your computer access request form
Using platforms like pdfFiller is instrumental in creating and editing access request forms efficiently. With pdfFiller's tools, users can quickly make adjustments to their forms, ensuring that they align with evolving organizational standards. You can easily create custom templates that suit your organization’s unique needs while simplifying the submission process.
The platform allows users to add or remove fields, enabling the tailoring of forms to better capture necessary details specific to various roles or departments. Consequently, this customization leads to more accurate and effective requests, ultimately streamlining the approval process.
Collaborating on access requests with your team
Collaboration is crucial when managing access requests. pdfFiller makes it easier for teams to submit forms collectively or share them for review among stakeholders. Team members can access the same document, add comments, and suggest changes to ensure accuracy and completeness before submission.
By tracking the submission and approval process through pdfFiller, organizations can identify bottlenecks and improve response times. This not only enhances productivity but also fosters open communication among team members, ensuring everyone stays informed about the request's progress.
eSigning and finalizing your submission
The electronic signature (eSignature) is essential for validating the submission of your computer access request form. This not only confirms that the requestor has authorized the submission but also provides a secure, legal binding to the document. Utilization of pdfFiller’s eSignature feature ensures that your signed forms are accepted and compliant with legal standards without the need for physical paperwork.
When eSigning your form using pdfFiller, it's important to follow the prompts to ensure that your signature meets all requirements. Moreover, safeguarding the document’s integrity and confidentiality is paramount; pdfFiller’s encryption methods protect your submissions from unauthorized access.
Common questions and troubleshooting tips
Upon submission of your computer access request form, many individuals might wonder about the status of their request. It’s common to feel anxious as approvals can vary in time due to various administrative workflows. However, most organizations have procedures in place for tracking requests, and you should reach out to the IT department or designated authority for updates.
If you encounter issues while filling out or submitting the form, familiarize yourself with common troubleshooting tips. Ensuring that all fields are complete before clicking submit will minimize the chance of errors. Also, consider reviewing the organizational guidelines regarding digital forms for clearer instructions specific to your company’s processes.
Exploring related forms and templates
Beyond the standard computer access request form, organizations may require several related forms depending on operational needs. For instance, a remote access request form allows employees to gain access to organizational resources remotely, while a telecommunication access request form facilitates access to communication tools and networks.
Implementing various specialized forms ensures comprehensive security measures are in place tailored to specific needs within your organization. Platforms like pdfFiller can assist in building custom templates, enhancing efficiency for the overall document management process.
Analyzing form submission insights
Utilizing pdfFiller's analytics tools can provide organizations with valuable insights regarding form submissions. These insights can reveal trends and patterns related to access requests, helping teams identify common needs across different departments.
Understanding the data collected from request submissions can assist in making informed decisions regarding data access policies and procedures. Enhanced analytics lead to proactive adjustments, ensuring that access controls remain efficient and effective.
Maximizing the use of the computer access request form
Regular review and updates of the computer access request form are essential to remain compliant with changing regulations and evolving technology. An organization’s policies should reflect current risks, challenges, and the state of technology to ensure relevant and secure access.
Encouraging feedback from users on the form’s effectiveness can reveal potential improvements. Involving teams in this review process fosters a culture of security awareness and compliance. Effective access management through continuous updates will not only safeguard information but also streamline operational efficiency.






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How do I execute computer access request form online?
How do I fill out computer access request form using my mobile device?
How do I complete computer access request form on an Android device?
What is computer access request form?
Who is required to file computer access request form?
How to fill out computer access request form?
What is the purpose of computer access request form?
What information must be reported on computer access request form?
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.















