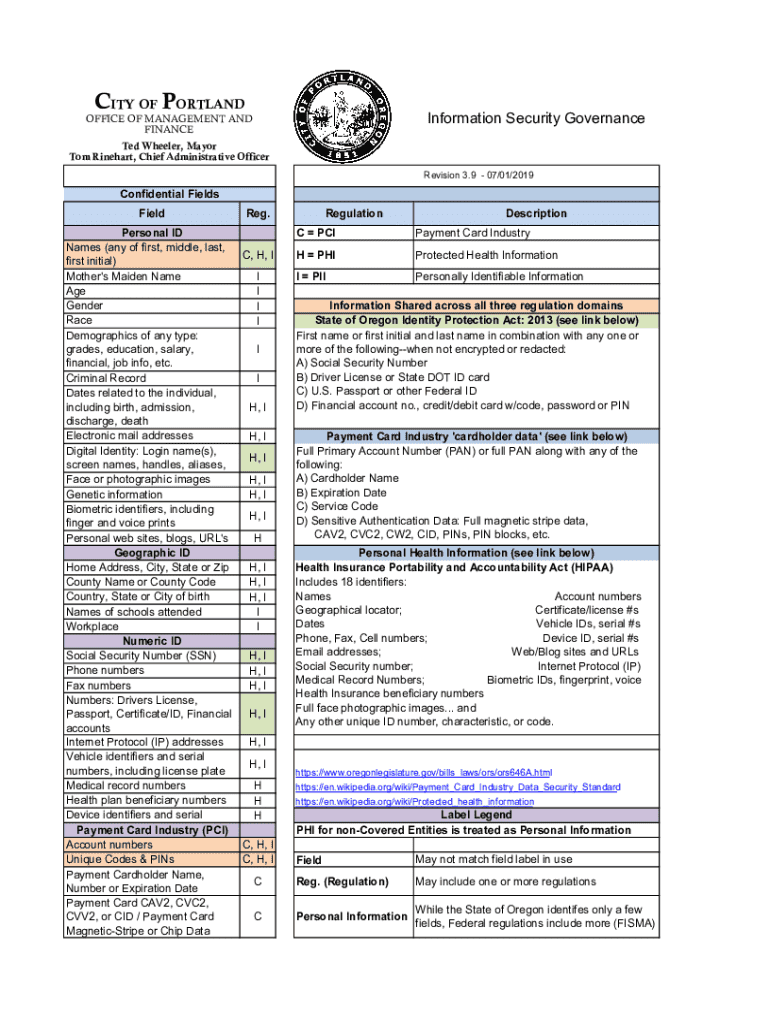
Get the free Information Security Governance
Get, Create, Make and Sign information security governance



Editing information security governance online
Uncompromising security for your PDF editing and eSignature needs
How to fill out information security governance

How to fill out information security governance
Who needs information security governance?
Information Security Governance Form - How-to Guide Long-Read
Understanding information security governance
Information security governance refers to the framework and processes that ensure an organization’s information is effectively protected while aligning with business goals. At its core, this concept revolves around the strategic management of information security to mitigate risks associated with data breaches and unauthorized access. By establishing clear governance, organizations can define roles, responsibilities, and policies associated with their information security efforts.
The relevance of governance in information security frameworks cannot be overstated. It serves as the backbone for decision-making processes and sets the tone for a security-focused culture. Having a structured governance approach allows organizations to proactively manage risks and comply with various regulations, thereby safeguarding sensitive data effectively.
Role of forms in governance
Structured forms play a pivotal role in the governance processes by providing a consistent means to capture and disseminate information. These forms not only streamline the data collection needed for making informed decisions but also enhance transparency and accountability within the governance framework. The relationship between forms and compliance requirements is significant; organized documentation supports adherence to legal standards and regulatory obligations, thus minimizing liability.
The need for an information security governance form
An information security governance form is essential for various organizations, regardless of their size or industry. Small businesses can utilize these forms to establish foundational security processes, while mid-sized and enterprise-level organizations may leverage them to manage complex frameworks and comply with extensive regulatory requirements. Industries such as finance, healthcare, and government are particularly critical in maintaining stringent security governance due to the sensitive nature of the information they handle.
Moreover, teams responsible for managing sensitive information can significantly benefit from this structured approach. The framework-based governance ensures that each department understands its role and the importance of communication in mitigating risks. This enhances collaboration and accountability, informing all stakeholders of their responsibilities in maintaining information security.
Key components of an information security governance form
An effective information security governance form consists of various essential elements that capture the core aspects of governance. First and foremost, the governance objectives and a clear scope description outline what the form seeks to accomplish. This clarity helps teams understand the direction and purpose of their information security strategies.
Secondly, identifying stakeholders and clearly defining their roles within the governance process are crucial. Each team member's responsibilities should align with the organization's overarching security goals, providing a sense of ownership over security measures. Additionally, incorporating a risk management methodology into the form ensures that any potential threats are identified and addressed systematically.
Interactive features and templates
The flexibility of modern information security governance forms is enhanced by interactive features and customizable templates. For instance, organization-specific fields can be integrated, allowing teams to tailor the form according to their unique processes and security needs. Each field should be designed with relevance in mind, ensuring that data captured efficiently contributes to ongoing governance.
Steps to create and utilize an information security governance form
Creating your information security governance form begins with identifying its scope and purpose. Consider what you aim to achieve with the form, whether it’s compliance, risk assessment, or stakeholder communication. Next, gather input from key stakeholders within your organization. This involvement ensures that the form reflects the diverse perspectives and needs of different teams.
After gathering insights, the design process can begin. Utilize cloud-based editing tools to create a visually appealing and functional form. The use of platforms like pdfFiller allows for seamless collaboration, making it easier for teams to provide input and finalize content efficiently.
Filling out the form effectively
Completing the information security governance form requires attention to detail and clarity. Common pitfalls include vague language or overlooked regulatory aspects, so it's crucial to ensure precision when filling out each section. Best practices involve using clear terminology and avoiding jargon, making the form accessible to all team members regardless of their technical expertise.
Managing and updating your information security governance form
Establishing a review process for your information security governance form is vital. Regular updates are necessary to adapt to changing regulatory requirements and business practices. Scheduling reviews helps maintain the form's relevance and ensures that it continues to meet organizational needs.
Using tools like pdfFiller for ongoing management makes it easier to edit and revise the document. With collaborative features, team members can contribute their feedback and updates, fostering a culture of shared responsibility around security governance.
Compliance and regulatory considerations
Organizations must navigate a complex landscape of legal frameworks that impact governance, including GDPR, HIPAA, and others. Understanding these regulations is crucial, as they inform how the governance form is structured to support compliance efforts effectively. This understanding ensures that the organization can demonstrate its commitment to protecting sensitive information as required by law.
Maintaining thorough documentation for audits and assessments is equally important. The information security governance form should be accompanied by key documents that provide evidence of compliance, making organization records invaluable during external audits.
Real-world applications and case studies
Real-world examples provide insight into effective information security governance practices. For instance, a financial institution may implement the form to ensure compliance with stringent regulatory requirements while maintaining robust security protocols. Such case studies highlight the benefits of a systematic approach to governance and the potential pitfalls of neglecting comprehensive documentation.
Moreover, tailoring the form for specific industries like healthcare or government can optimize its effectiveness. Given their unique regulatory requirements, industry-specific adaptations can enhance compliance and security measures, providing a more effective governance framework.
Challenges in maintaining information security governance
Organizations face several challenges when maintaining information security governance. Resistance from stakeholders and team members can hinder progress, as can the rapid pace of technological change. Concerns over how to update practices can stymie effective governance strategies, requiring proactive communication and educational efforts to mitigate pushback.
To overcome these governance challenges, organizations should foster a culture centered around security. By promoting awareness and involving executive leadership in governance initiatives, teams can build the support necessary for lasting change, ensuring that security remains a priority across the organization.
Future trends in information security governance
The landscape of information security governance is continuously evolving. Emerging practices, particularly the incorporation of AI and automation, are set to transform governance processes, making them more efficient and responsive. Organizations should stay ahead of these trends to ensure their frameworks remain robust and aligned with best practices.
Predicting future challenges is equally important. Upcoming regulatory changes may impact how organizations approach their governance, necessitating proactive adaptations to align with new legal requirements. Anticipating these shifts will empower organizations to maintain security governance effectively.
Final thoughts on information security governance
Continuous improvement and adaptation are essential components of effective information security governance. Organizations must prioritize evolving their governance practices to stay compliant and proactive in an increasingly complex security landscape. Encouragement for teams to regularly utilize the governance form for updates and assessments can streamline these efforts.
By leveraging technology such as pdfFiller, organizations can enhance their document management practices. This cloud-based platform empowers users to seamlessly edit and manage the information security governance form, fostering an efficient and collaborative approach to security governance.






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I edit information security governance from Google Drive?
How do I complete information security governance online?
Can I edit information security governance on an Android device?
What is information security governance?
Who is required to file information security governance?
How to fill out information security governance?
What is the purpose of information security governance?
What information must be reported on information security governance?
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.



















