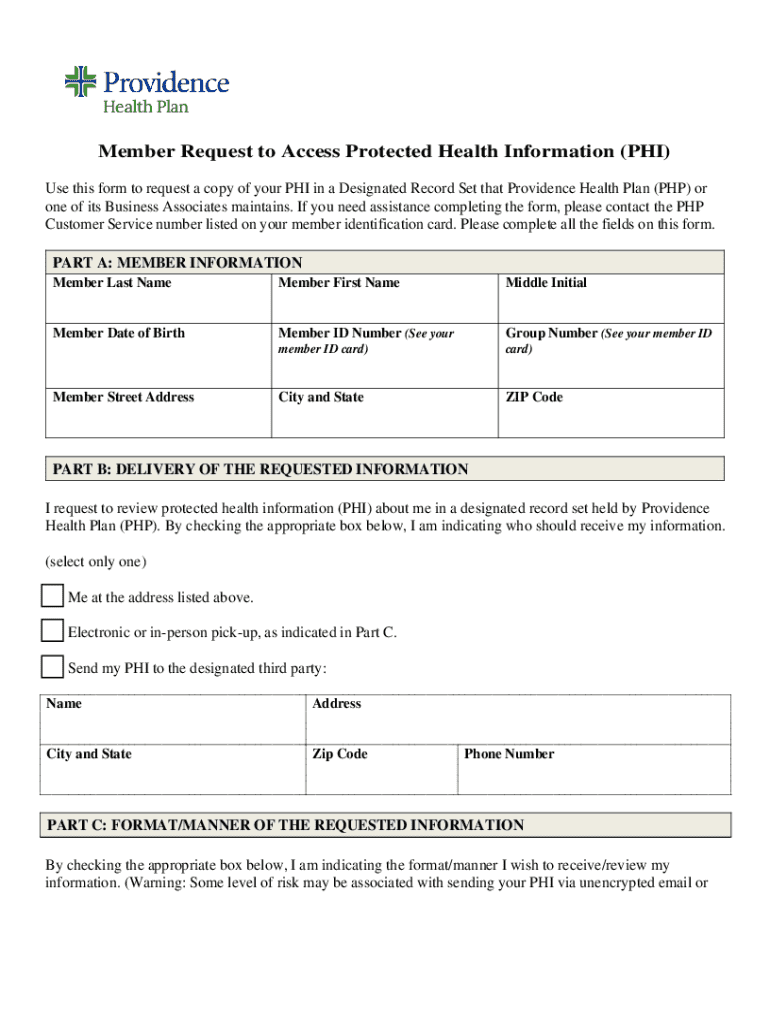
Get the free Member Request to Access Protected Health Information (phi)
Get, Create, Make and Sign member request to access



How to edit member request to access online
Uncompromising security for your PDF editing and eSignature needs
How to fill out member request to access

How to fill out member request to access
Who needs member request to access?
Navigating the Member Request to Access Form: A Comprehensive Guide
Understanding the member access request process
A member access request is an essential process that allows individuals to ask for permission to view or access specific documents or templates within an organization. In environments where sensitive information is handled, such requests are crucial to maintain confidentiality and protect proprietary data. Managing these access requests efficiently helps organizations ensure that only authorized personnel can view or alter critical information, thus safeguarding their assets and complying with relevant regulations.
Utilizing a structured access request form streamlines the process of collaboration within teams. Not only does it create a clear pathway for requests to be submitted, but it also enhances security protocols and document management. By requiring detailed information about the requester and the requested documents, organizations can better assess the necessity and appropriateness of each access request. This meticulous approach not only fosters accountability but also encourages communication and collaboration among team members.
Preparing for the access request
Before initiating the access request, it is critical to clearly identify the need for such access. Consider scenarios where information sharing is vital, such as collaborative projects, audits, or compliance checks. Understanding who needs access and why they require it helps streamline the approval process and minimizes unnecessary delays. For instance, if a new team member requires access to certain marketing materials for their onboarding, it is essential to provide the relevant context for their request.
Equally important is gathering all required information to support the access request. Requesters should prepare to provide their personal details, including their name, email, and contact number. In addition, information about the specific document, template, or data they are requesting access to must be precise and relevant. This preparation not only expedites the submission process but also enhances the chances of approval, as reviewers can quickly understand the context of the request.
Completing the member access request form
Filling out the member access request form accurately is vital to ensuring a smooth approval process. Follow these step-by-step instructions to complete your request conveniently through pdfFiller's platform:
For a successful submission, take a moment to understand the expected response time after submitting your request. Generally, organizations will have a defined timeline for review, which allows you to manage your expectations accordingly.
Verification and approval process
Once you submit your access request, it initiates a verification and approval process. Typically, the request is reviewed by a designated authority or team within the organization. Depending on the nature of the request and the volume of requests being handled, response times can vary. On average, you can expect to receive feedback within a few business days, but it's always advisable to check with your department for specific timelines.
Notifications and communication play a critical role in this stage. Once a decision has been made about your access request, organizations often reach out via email or through an internal communication platform. It's essential to keep your contact details up-to-date to avoid missing important notifications regarding your request status.
Managing document access
If your request is approved, the next steps are crucial for a seamless access experience. Depending on your organization's procedures, you will receive instructions on how to access the document or template. pdfFiller provides various features that allow users to edit, sign, and collaborate on shared documents securely. To start, familiarize yourself with the platform to leverage its functionalities for maximum effectiveness.
On the other hand, there may come a time when it is necessary to revoke access to documents. This could be due to changes in team structures, project completions, or security concerns. Organizations must have a clear process in place for revoking access to maintain document security and comply with data protection regulations. Adhering to these processes ensures that only authorized users have continual access to sensitive information.
Frequently asked questions (FAQs)
Many individuals might have concerns surrounding access requests, such as what happens if their request is denied. It is essential to remember that denial might occur for various reasons, including insufficient justification for access or a lack of permissions. Users can typically appeal an access denial, although the process may vary by organization. Therefore, understanding the specific protocols for your organization is critical.
Troubleshooting access issues also forms a key part of managing access. In instances where users encounter login problems or difficulty in completing the access request form, contacting support for assistance is the best route. Having a readily available support team can greatly reduce frustrations and expedite solutions, ultimately improving the broader experience for all users involved.
Utilizing pdfFiller for enhanced management
PdfFiller offers numerous features that enhance users' capabilities for document management. From editing PDFs to eSigning, individuals and teams can manage essential documents with ease and efficiency. The collaborative tools available allow for real-time updates and ensure that all users involved are aware of changes, thus fostering better teamwork.
For teams and individuals alike, pdfFiller stands out by providing access from anywhere. This flexibility is particularly beneficial in today’s increasingly remote work environments. Users can manage their documents, review changes, and collaborate with colleagues without being restricted to a single location. Enhanced security protocols further ensure that data remains secure, giving users peace of mind while they work.
Best practices for document access management
Regularly reviewing user access is a critical best practice that can significantly enhance document security. Conducting audits to assess who has access to specific documents or templates allows organizations to identify unnecessary permissions and potentially revoke them, thereby limiting exposure to sensitive data. This proactive approach reduces the risk of unauthorized access and enhances overall compliance efforts.
Maintaining up-to-date contact information is another vital aspect of document access management. By keeping user records current, organizations can ensure that communication regarding document access or changes is timely and effective. This not only helps when notifying users about approved requests but also assists in addressing any access issues that may arise, resulting in a more robust access management process overall.






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
Can I create an electronic signature for the member request to access in Chrome?
How do I edit member request to access straight from my smartphone?
How do I fill out member request to access on an Android device?
What is member request to access?
Who is required to file member request to access?
How to fill out member request to access?
What is the purpose of member request to access?
What information must be reported on member request to access?
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.






















