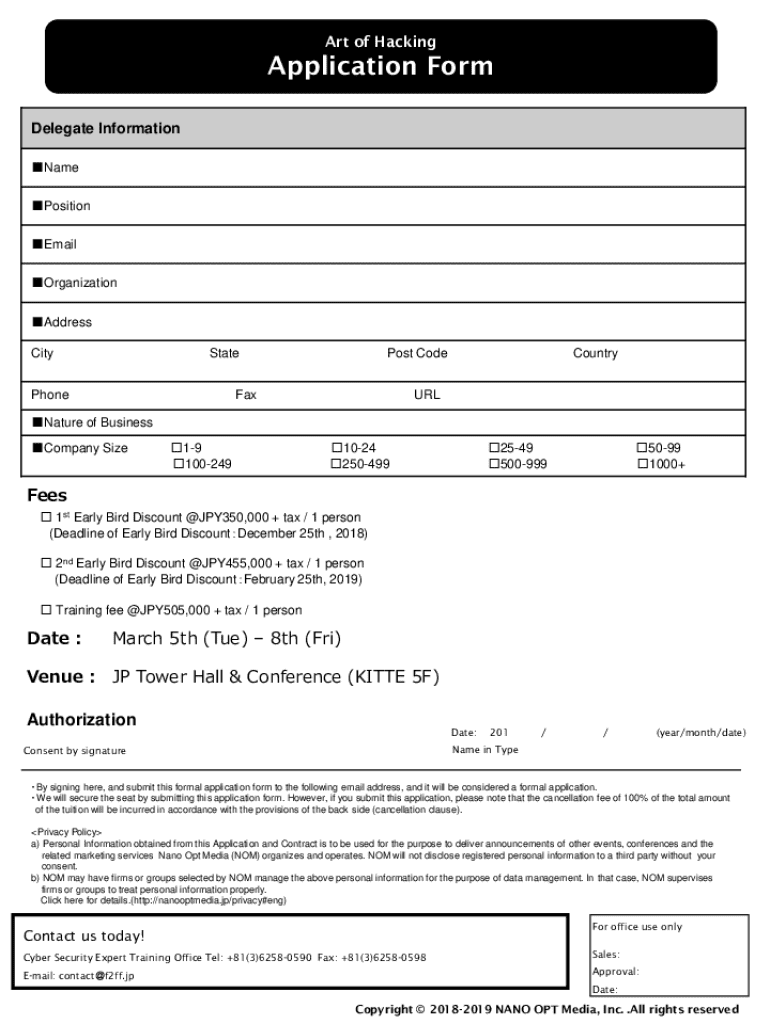
Get the free Art of Hacking
Get, Create, Make and Sign art of hacking



How to edit art of hacking online
Uncompromising security for your PDF editing and eSignature needs
How to fill out art of hacking

How to fill out art of hacking
Who needs art of hacking?
Art of Hacking Form: A Comprehensive Guide
Understanding the art of hacking form
The art of hacking form involves creating, managing, and utilizing forms designed for efficient data collection and organization. These forms are crucial in various contexts, including business, education, and healthcare, as they streamline processes and improve data accuracy. By utilizing hacking forms, users enhance their productivity and ensure compliance with legal standards.
Common use cases of hacking forms include job applications, feedback surveys, and medical history forms. Each context requires a specialized approach to ensure that the form meets the specific needs of the audience, capturing all necessary information while remaining user-friendly.
pdfFiller provides a diverse selection of hacking forms tailored to meet various needs. From templates to customizable options, it allows users to craft forms that resonate with their specific applications.
Getting started with your hacking form
Accessing your hacking form through pdfFiller is a straightforward process. Users can visit the pdfFiller website and navigate to the forms section where they can find available templates. Upon selecting a template, users can begin customizing it to suit their needs.
The user interface of pdfFiller is designed to be intuitive. Users can drag and drop elements, edit text, and change the design without extensive training. Notable features include the ability to collaborate in real-time, which is essential for team projects.
These features not only enhance the user experience but also provide the tools necessary for effective form management.
Crafting your hacking form
When crafting a hacking form, essential elements must be included to facilitate thorough data collection. Key sections to consider are the title and purpose of the form, which should be clear to all users, followed by vital input fields, checkboxes, and signature sections.
Choosing the right template from pdfFiller can streamline this process. It's crucial to select a template that aligns with your objectives while allowing for customization. Users can incorporate specific branding elements, colors, and logos to make the form personalized.
Utilizing pdfFiller's editing tools allows for easy adjustments to ensure that your hacking form is comprehensive and meets the intended needs.
Filling out the hacking form effectively
Accurately completing your hacking form is paramount to ensure data integrity and usability. Here are several tips to assist users in this process: always read the form instructions carefully, fill in all mandatory fields, and double-check your entries before submission.
Common mistakes include overlooking required fields and not using clear, concise language. Utilizing tools such as the auto-fill feature offered by pdfFiller can speed up the process and reduce errors.
These strategies not only enhance accuracy but also ensure a smoother experience when filling out forms.
eSigning your hacking form
Incorporating electronic signatures into your hacking forms brings numerous benefits, including enhanced security, speed, and convenience. With pdfFiller, adding an electronic signature is a simple process. Users can create their digital signature or upload an image of their handwritten signature directly into the form.
The integrity of eSigned documents is maintained through robust security measures, ensuring compliance with legal requirements. Users can feel confident that their documents are legally binding and secure.
This feature makes pdfFiller a go-to solution for professionals looking for efficient document management.
Collaborating with teams on hacking forms
Collaboration is essential when working with teams on hacking forms. pdfFiller facilitates seamless collaboration through its various features. Users can share forms with team members for input or feedback, ensuring collective insights are integrated into the final document.
Utilizing comment features allows for discussions around specific sections of the form, creating an interactive document review process. Additionally, version control options help track changes, ensuring that everyone is aligned throughout the creation process.
These collaborative features promote teamwork and ensure the final hacking form reflects the collective goal of the group.
Managing your hacking form post-completion
Once your hacking form is complete, effective management is vital for future access and organization. Storing forms in the cloud ensures that they are readily available on various devices. pdfFiller offers features for categorizing and tagging documents, making it easy to find specific forms later.
For seamless retrieval, consider adopting a systematic approach to document management that includes naming conventions and regular reviews of stored files. Integrating your hacking forms with other document management tools can further streamline processes and enhance productivity.
Implementing these strategies will help users maximize the utility of their hacking forms long after they've been completed.
Best practices for hacking forms
Creating hacking forms that adhere to best practices is essential for ensuring legal compliance and user satisfaction. Conducting thorough research on relevant laws and regulations governing forms is vital. This encompasses aspects such as data protection, accessibility, and retention policies.
To create user-friendly and accessible forms, consider employing straightforward language, logical layouts, and clear instructions. Additionally, gathering feedback from users about their experiences with the form can provide insights into areas for improvement for future iterations.
By adhering to best practices, users can create forms that not only meet their needs but also positively impact their audience.
Advanced techniques for hacking forms
For users seeking to enhance their hacking forms, incorporating advanced techniques such as conditional logic can greatly improve usability. Conditional logic allows the form to change dynamically based on user responses, guiding them toward relevant sections, thus streamlining their experience.
Advanced PDF features like calculations and validations can also be implemented via pdfFiller, which allows for more complex forms that require data processing. Exploring potential integrations with other software can further expand the capabilities of your hacking forms.
Implementing these advanced techniques can not only improve the form's functionality but also enhance the user experience significantly.
The future of hacking forms
As technology continues to evolve, the creation and management of hacking forms are also set to progress. Emerging trends such as artificial intelligence and automation are beginning to play a prominent role in document creation and management. These technologies can assist users in crafting forms that not only gather data effectively but also analyze it for actionable insights.
Future document solutions will likely offer more robust security features, improved integration capabilities, and intuitive user interfaces, making it easier for individuals and teams to manage their documentation needs efficiently.
Staying ahead of these trends will position users to capitalize on the capabilities of the evolving digital landscape.
Troubleshooting common issues with hacking forms
Encountering challenges while filling out hacking forms is common, but many issues can be easily resolved. Identifying common filling errors such as incomplete fields or mismatched data can streamline the correction process. Ensuring compliance with the required formats for entries can reduce many unforeseen issues during submission.
When facing electronic signature problems, users should verify that all necessary fields are completed and that the signature is properly inserted. Compatibility issues across different devices and browsers can often be rectified by updating software or changing settings.
Utilizing these troubleshooting strategies will enhance user confidence and proficiency when dealing with hacking forms.
User testimonials and success stories
Hacking forms created using pdfFiller have enabled numerous individuals and teams to manage their documentation needs seamlessly. Users report significant improvements in workflow efficiency, particularly when using collaborative features and electronic signatures.
Success stories illustrate how pdfFiller has transformed the document management process for various organizations, showcasing the platform's ability to cater to diverse form-related needs.
These testimonials highlight the effectiveness of pdfFiller as a leading solution for hacking form creation and management.






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I edit art of hacking from Google Drive?
How do I execute art of hacking online?
Can I edit art of hacking on an Android device?
What is art of hacking?
Who is required to file art of hacking?
How to fill out art of hacking?
What is the purpose of art of hacking?
What information must be reported on art of hacking?
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.






















