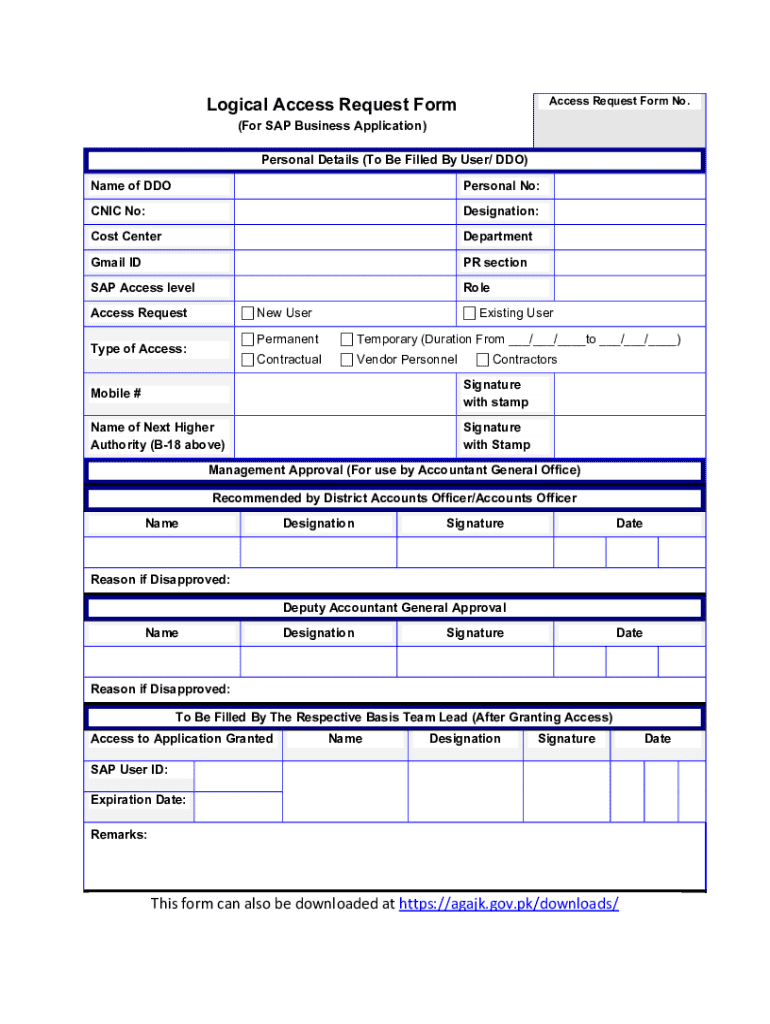
Get the free Access Request Form No. - agajk gov
Get, Create, Make and Sign access request form no



Editing access request form no online
Uncompromising security for your PDF editing and eSignature needs
How to fill out access request form no

How to fill out access request form no
Who needs access request form no?
Access request form no form: Redefining access management
Understanding access request forms
An access request form acts as a formal mechanism for individuals or teams to request access to specific documents, systems, or areas within an organization. While often regulated for compliance, the purpose of these forms is to provide a structure that ensures accountability and traceability. These forms are crucial in environments where sensitive information is handled, allowing organizations to manage permissions effectively and minimize unauthorized access.
Typically, access request forms are required in scenarios such as data protection compliance, secure file sharing, or restricted resource access. In education, for instance, students may need access to specific online resources for their projects, while in healthcare settings, staff may request access to patient records under strict compliance regulations.
Key components of access request forms
An effective access request form encompasses several key elements:
By including these components, organizations can streamline the permission process, minimizing the risk of data breaches and ensuring compliance with internal policies.
The concept of 'no form'
The term 'no form' refers to a streamlined process of managing access requests without the use of traditional forms. This approach may seem unconventional, but it can significantly enhance efficiency, particularly in fast-paced environments where speed is essential. Rather than filling out a lengthy form, users can communicate their access needs through alternative means, allowing for quicker responses and less bureaucratic red tape.
Benefits of adopting a 'no form' approach include increased agility, as team members can quickly adapt to changing access needs. Furthermore, it helps in nurturing open communication, fostering trust within teams, and ultimately addressing the core of the matter — the necessity for access rather than bogging down the process with formalities.
Scenarios where no form is applicable
There are several situations where a 'no form' process can be effectively implemented:
Understanding these specific scenarios is key to implementing an effective no-form strategy while still maintaining sufficient oversight.
How to utilize access request forms
For teams accustomed to standard processes, the traditional method of managing access requests can be straightforward. It generally involves filling out a standard access request form, which requires adhering to a predefined set of steps. Below is a step-by-step guide:
Steps for managing access requests without forms
When opting for the no-form approach, managing access requests requires clarity and efficient communication. Here are some alternative methods:
Considering these methods, organizations can maintain the integrity of their access management systems while reducing friction.
Technologies supporting access management
To facilitate the no-form process, a variety of innovative tools are available. These platforms help manage access in a streamlined manner, enhancing collaboration and security across teams. Tools such as shared drives, collaborative platforms, and project management software can all play pivotal roles in this process.
Among these, pdfFiller stands out with features designed specifically for document management. This platform empowers users to draft, edit, and manage documents efficiently — even allowing eSigning capabilities for those urgent approvals required in access requests. Its collaborative tools ensure teams stay connected while accessing the necessary resources.
Utilizing pdfFiller for document management
pdfFiller excels in supporting access requests by offering tools that account for both traditional and no-form processes. Users can easily modify their documents, send them for signatures, and track progress seamlessly. This adaptability ensures that regardless of whether a team opts for forms or not, they can always manage their documents effectively.
Best practices for handling access requests
While the method of handling access requests may vary between organizations, several best practices remain universally applicable. Security remains a top priority; therefore, protecting sensitive information is paramount. This means utilizing secure communication channels and establishing clear data handling protocols.
Streamlining the process is just as important. Organizations can improve response times and efficiency with some proactive strategies:
When applying these best practices, utilizing tools like pdfFiller can keep teams organized and compliant.
Case studies and examples
Implementing access management without relying solely on forms can yield significant benefits across various industries. For example, healthcare institutions have embraced informal request methods for accessing patient data. Effective verbal communication has been paramount in maintaining both speed and confidentiality, especially relevant during urgent situations.
In educational settings, many faculty members have adopted the no-form approach when collaborating on projects. By initiating verbal requests and utilizing shared digital platforms for resource access, they have facilitated a seamless exchange of materials, enhancing both productivity and teamwork.
Success stories
Numerous teams have experienced positive changes after transitioning to a no-form approach. A marketing team, for example, reported increased response times and enhanced collaboration simply by transitioning from formal requests to digital communications through pdfFiller. Their ability to share and review documents quickly without needing to fill out a form allowed them to focus on their project goals rather than bureaucratic hurdles.
These success stories serve to demonstrate that adopting a flexible, efficient approach to access management can drive significant improvements in productivity and team morale.
Interactive tools and resources
To effectively manage access requests, consider utilizing an array of interactive tools and resources that can support your team's needs. For instance, checklists are invaluable for ensuring nothing is overlooked when handling requests. Users can download customizable templates tailored to various situations, aiding in clear communication and consistent documentation.
FAQ sections can also contribute to a smoother process, providing answers to common questions around access management without forms. Creating a repository of such information can minimize repeated inquiries and improve efficiency.
Navigating common challenges
Transitioning to a no-form approach does carry potential challenges that teams may face. Issues such as inconsistent communication, confusion over access permissions, and lack of accountability can arise. Moreover, without a formal structure in place, there is a risk of unauthorized access if not managed adequately.
However, there are strategies to address these challenges effectively. Establishing clear communication channels and guidelines can enhance transparency and accountability. Regular checks and balances can ensure that all requests are logged properly, and follow-up actions are taken.
Ensuring that all team members are aligned on the protocol is key for seamless operations. By addressing challenges head-on, organizations can reap the benefits of a flexible yet secure access management strategy.






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How do I fill out the access request form no form on my smartphone?
How can I fill out access request form no on an iOS device?
How do I fill out access request form no on an Android device?
What is access request form no?
Who is required to file access request form no?
How to fill out access request form no?
What is the purpose of access request form no?
What information must be reported on access request form no?
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.