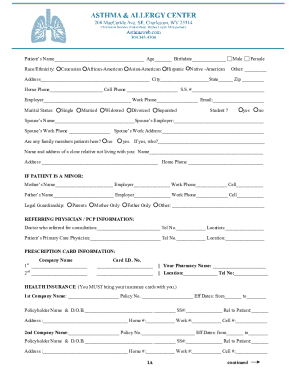
Get the free Assessment of Effective Risk in Software - mecs-press
Show details
I.J. Information Engineering and Electronic Business, 2013, 4, 5864
Published Online October 2013 in M ECS (http://www.mecspress.org/)
DOI: 10.5815/ indeed.2013.04.08Assessment of Effective Risk in
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign assessment of effective risk

Edit your assessment of effective risk form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your assessment of effective risk form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit assessment of effective risk online
To use our professional PDF editor, follow these steps:
1
Set up an account. If you are a new user, click Start Free Trial and establish a profile.
2
Upload a file. Select Add New on your Dashboard and upload a file from your device or import it from the cloud, online, or internal mail. Then click Edit.
3
Edit assessment of effective risk. Replace text, adding objects, rearranging pages, and more. Then select the Documents tab to combine, divide, lock or unlock the file.
4
Get your file. Select your file from the documents list and pick your export method. You may save it as a PDF, email it, or upload it to the cloud.
pdfFiller makes dealing with documents a breeze. Create an account to find out!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out assessment of effective risk

How to fill out assessment of effective risk?
01
Identify potential risks: Begin by identifying all potential risks that could impact the project, organization, or business. This can include both internal and external risks such as financial, operational, regulatory, or technological risks.
02
Assess the likelihood: Evaluate and determine the likelihood of each identified risk occurring. Consider factors such as historical data, expert opinions, or statistical analysis to gauge the probability of each risk eventuating.
03
Estimate potential impact: Assess the potential impact or consequences of each identified risk. Consider the financial, operational, reputational, or legal impacts that could arise if the risk materializes. This step helps in prioritizing risks based on their severity.
04
Prioritize risks: Once you have assessed the likelihood and impact, prioritize the risks based on a predetermined criteria or framework. This helps in determining which risks require immediate attention and mitigation efforts.
05
Develop mitigation strategies: For each prioritized risk, develop appropriate risk mitigation strategies. These strategies can include risk avoidance, risk transfer, risk reduction, or risk acceptance. Tailor the strategies to each specific risk, aligning them with organizational goals and risk appetite.
06
Assign responsibility and timeline: Identify the person or team responsible for implementing the risk mitigation strategies. Set clear timelines and deadlines for each action item to ensure timely execution.
07
Monitor and review: Continuously monitor the effectiveness of the implemented risk mitigation strategies. Regularly review the assessment of effective risk to update and adjust the strategies as needed. This step ensures ongoing risk management and enables proactive responses to emerging risks.
Who needs assessment of effective risk?
01
Project managers: Project managers need assessment of effective risk in order to identify and manage potential risks that can impact project timelines, budgets, and deliverables. It helps them make informed decisions and take necessary actions to minimize risks.
02
Business owners: Business owners require assessment of effective risk to evaluate and understand the potential risks that can affect their operations, financial stability, and reputation. It assists them in developing risk mitigation strategies and protecting their business interests.
03
Risk management professionals: Risk management professionals specialize in assessing, analyzing, and managing risks. They utilize effective risk assessments to identify, evaluate, and prioritize risks for organizations, enabling them to implement appropriate risk management strategies.
04
Regulatory bodies: Regulatory bodies rely on assessment of effective risk to evaluate the compliance and risk exposure of organizations operating within their jurisdiction. It helps them ensure that organizations are effectively managing and mitigating risks to protect stakeholders and the public interest.
In conclusion, filling out an assessment of effective risk involves identifying potential risks, assessing their likelihood and impact, prioritizing risks, developing mitigation strategies, monitoring, and reviewing the effectiveness of implemented strategies. This process is important for project managers, business owners, risk management professionals, and regulatory bodies to proactively manage and mitigate risks.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How do I modify my assessment of effective risk in Gmail?
assessment of effective risk and other documents can be changed, filled out, and signed right in your Gmail inbox. You can use pdfFiller's add-on to do this, as well as other things. When you go to Google Workspace, you can find pdfFiller for Gmail. You should use the time you spend dealing with your documents and eSignatures for more important things, like going to the gym or going to the dentist.
Can I create an electronic signature for signing my assessment of effective risk in Gmail?
With pdfFiller's add-on, you may upload, type, or draw a signature in Gmail. You can eSign your assessment of effective risk and other papers directly in your mailbox with pdfFiller. To preserve signed papers and your personal signatures, create an account.
How do I edit assessment of effective risk on an iOS device?
No, you can't. With the pdfFiller app for iOS, you can edit, share, and sign assessment of effective risk right away. At the Apple Store, you can buy and install it in a matter of seconds. The app is free, but you will need to set up an account if you want to buy a subscription or start a free trial.
What is assessment of effective risk?
Assessment of effective risk is the process of evaluating potential risks and determining the effectiveness of strategies in place to manage and mitigate those risks.
Who is required to file assessment of effective risk?
Certain organizations, particularly those in regulatory industries such as finance and healthcare, are required to file assessment of effective risk.
How to fill out assessment of effective risk?
Assessment of effective risk is typically filled out by designated risk management teams within an organization, following specific guidelines and protocols.
What is the purpose of assessment of effective risk?
The purpose of assessment of effective risk is to identify potential risks, evaluate current risk management strategies, and make informed decisions to improve risk mitigation.
What information must be reported on assessment of effective risk?
Information such as identified risks, current controls in place, effectiveness of controls, and proposed improvements must be reported on assessment of effective risk.
Fill out your assessment of effective risk online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Assessment Of Effective Risk is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.