Security Assessment Proposal Template - Page 2
What is Security Assessment Proposal Template?
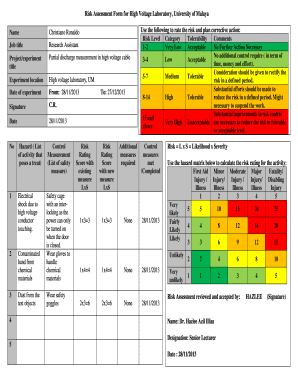
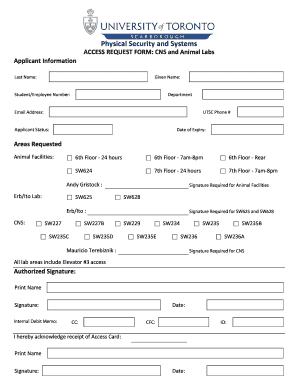
Security Assessment Proposal Template is a document used to propose a security assessment project. It outlines the objectives, scope, and methodology of the assessment, as well as the expected deliverables and timeline. This template serves as a blueprint for organizing and presenting a comprehensive security assessment proposal.
What are the types of Security Assessment Proposal Template?
There are several types of Security Assessment Proposal Templates available, depending on the specific industry or organization. Some common types include:
How to complete Security Assessment Proposal Template
Completing a Security Assessment Proposal Template involves the following steps:
pdfFiller empowers users to create, edit, and share documents online. Offering unlimited fillable templates and powerful editing tools, pdfFiller is the only PDF editor users need to get their documents done.