Free Security Roadmap Word Templates - Page 4
What are Security Roadmap Templates?
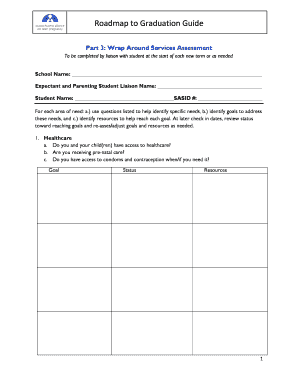
Security Roadmap Templates are essential tools used to plan, implement, and manage security strategies within an organization. They provide a framework for establishing, monitoring, and improving security measures to protect sensitive information and assets. By using Security Roadmap Templates, businesses can ensure they have a clear plan in place to address potential security threats and vulnerabilities.
What are the types of Security Roadmap Templates?
There are several types of Security Roadmap Templates available, each tailored to different security needs and requirements. Some common types include: 1. Network Security Roadmap Templates 2. Cybersecurity Roadmap Templates 3. Data Protection Roadmap Templates 4. Compliance Roadmap Templates 5. Incident Response Roadmap Templates
How to complete Security Roadmap Templates
Completing Security Roadmap Templates is a straightforward process that involves the following steps: 1. Define your security objectives and goals 2. Identify potential security risks and vulnerabilities 3. Develop a timeline for implementing security measures 4. Assign responsibilities to team members 5. Monitor and evaluate the effectiveness of the security roadmap regularly
Remember, pdfFiller empowers users to create, edit, and share documents online. Offering unlimited fillable templates and powerful editing tools, pdfFiller is the only PDF editor users need to get their documents done.