Fine-tune Signature Release For Free
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.
0
Forms filled
0
Forms signed
0
Forms sent
Discover the simplicity of processing PDFs online
Upload your document in seconds

Fill out, edit, or eSign your PDF hassle-free

Download, export, or share your edited file instantly
Top-rated PDF software recognized for its ease of use, powerful features, and impeccable support






Every PDF tool you need to get documents done paper-free
Create & edit PDFs
Generate new PDFs from scratch or transform existing documents into reusable templates. Type anywhere on a PDF, rewrite original PDF content, insert images or graphics, redact sensitive details, and highlight important information using an intuitive online editor.
Fill out & sign PDF forms
Say goodbye to error-prone manual hassles. Complete any PDF document electronically – even while on the go. Pre-fill multiple PDFs simultaneously or extract responses from completed forms with ease.
Organize & convert PDFs
Add, remove, or rearrange pages inside your PDFs in seconds. Create new documents by merging or splitting PDFs. Instantly convert edited files to various formats when you download or export them.
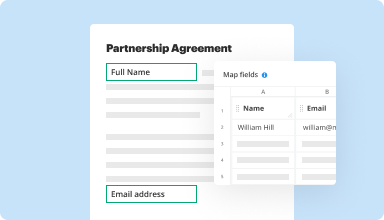
Collect data and approvals
Transform static documents into interactive fillable forms by dragging and dropping various types of fillable fields on your PDFs. Publish these forms on websites or share them via a direct link to capture data, collect signatures, and request payments.
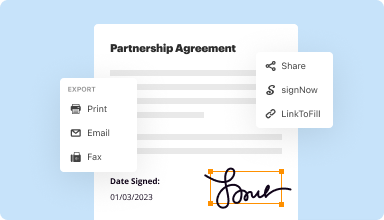
Export documents with ease
Share, email, print, fax, or download edited documents in just a few clicks. Quickly export and import documents from popular cloud storage services like Google Drive, Box, and Dropbox.
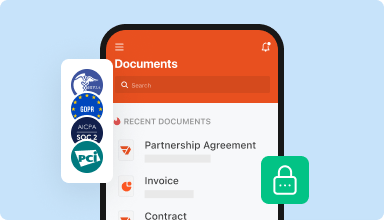
Store documents safely
Store an unlimited number of documents and templates securely in the cloud and access them from any location or device. Add an extra level of protection to documents by locking them with a password, placing them in encrypted folders, or requesting user authentication.
Customer trust by the numbers
64M+
users worldwide
4.6/5
average user rating
4M
PDFs edited per month
9 min
average to create and edit a PDF
Join 64+ million people using paperless workflows to drive productivity and cut costs
Why choose our PDF solution?
Cloud-native PDF editor
Access powerful PDF tools, as well as your documents and templates, from anywhere. No installation needed.
Top-rated for ease of use
Create, edit, and fill out PDF documents faster with an intuitive UI that only takes minutes to master.
Industry-leading customer service
Enjoy peace of mind with an award-winning customer support team always within reach.
What our customers say about pdfFiller
See for yourself by reading reviews on the most popular resources:
The forms are in a different size, doesn't match exactly the form and sometime may be rejected by the instituion or company that issue the original form.
2014-08-14
I hope to come back to this, as I have just signed up only a week ago. however, I had an unexpected event and need to tighten my finances. Great service though!
2017-08-15
I filled in IRS 990, Schedules A & O but didn't know I was using PDFfiller and when I tried to print I found I was locked out, so I had to subscribe and still have filled our forms that are locked out. Need timely hep in unlocking these documents. Since this experience and subscribing to PDFfiller (annual Suscrition) I have found it works very well. I contract for a Jazz club's 5 venues sites and have to fill out two cities' forms that I found easy to get using PDFfiller. I also became the treasurer of the Jazz Club again and had to bring out IRS 990s up to dat--non-profit. Again fond using PDFfiller to get fillable forms easy, better than going to IRI.gov.
2018-12-09
PDF filler has really helped my business. It is very affordable and easy to use. I can't see myself ever not using this great service form my customers.
2019-03-24
spanish feedback: me encanta la manera tan facil en que podemos conectar con aquellos clientes que tienen dificultad para todo cuando se necesita una firma, puedes usar emails, textos y mas, te da solucioin a tu trabajo y eso es LO GENIAL QUE AHI PARA TODO TIPO DE CLIENTE UNA SOLUCION
2024-09-27
I think 40 dollars is too much, but...
I think 40 dollars is too much, what you offer is well worth it except for the fact that it's a service I would only use occasionally. So 40 bucks every month is way too much for me. But I do love what you offer.
2024-03-07
I had a billing issue and customer…
I had a billing issue and customer support identified my problem and solved it with ease, no hassle, and immediately. Just good customer support. That makes the entire experience worth it, and the product worth paying for in my opinion.
2022-04-09
I didn't know a service like this existed but it is so convenient and safe or what is happening with the COVID-19 pandemic. I was able to mail very important documents without leaving my home.
2020-09-26
What do you like best?
Very easy to upload my documents, clean them up and edit and add information. I like that it stores all my documents that I've worked with.
What do you dislike?
Printing from the site has so many print windows to go through.
Recommendations to others considering the product:
Easy, Cost Effective. There is not a lot of features to overwhelm someone. For us, it works great as we only need to edit information on new documents but only receive the originals on paper so this is the easiest to get them filled out, and into electronic format for future use
What problems are you solving with the product? What benefits have you realized?
We complete our bid documents on this program and the PDF filler keeps the information professional, legible and I can go back and edit as needed. Easy and Cost effective solution for our small company
2020-08-18
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
What is signature in case of IDS IPS?
A signature is a set of rules that an IDS and an IPS used to detect typical intrusive activity, such as DoS attacks. You can easily install signatures using IDS and IPS management software such as Cisco IDM. Sensors enable you to modify existing signatures and define new ones.
Where do you put IDS and IPS?
Positioning an IPS/IDS on the Network An intrusion prevention system (IPS) usually sits directly behind the firewall, adding another layer of analysis that removes dangerous contents from the data flow.
Can IDS and IPS work together?
IDS and IPS work together to provide a network security solution. An IDS capture packets in real time, processes them, and can respond to threats, but works on copies of data traffic to detect suspicious activity by using signatures.
Where do network IDS go?
You can put the IDS outside the firewall (assuming you've hardened it appropriately) and behind the router. If you want to see what potentially malicious internal traffic you have inside your perimeter then monitoring from a point between the firewall and internal LAN is more appropriate.
What is IDS and IPS?
IDS vs. IPS: What is the Difference? Intrusion Detection Systems (IDS) analyze network traffic for signatures that match known cyberattacks. Intrusion Prevention Systems (IPS) also analyzes packets, but can also stop the packet from being delivered based on what kind of attacks it detects helping stop the attack.
What is IDS IPS which layer in OSI does it work?
IDS / IPS : Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) solutions form an integral part of a robust network defense solution. It monitors all network packets right from OSI Layer 2 (Data) to Layer 7 (Application), and stores this vast amount of information in its database.
How does IPS signature work?
Signature-Based In Signature-Based approach, predefined signatures or patterns of well-known network attacks are encoded into the IPS device by its vendors. The predefined patterns are then used to detect an attack by comparing the patterns that an attack contains, against the ones that are stockpiled in IPS.
How do signature based IPS work?
Signature-Based In Signature-Based approach, predefined signatures or patterns of well-known network attacks are encoded into the IPS device by its vendors. The predefined patterns are then used to detect an attack by comparing the patterns that an attack contains, against the ones that are stockpiled in IPS.
#1 usability according to G2
Try the PDF solution that respects your time.






