Last updated on
Nov 13, 2024
Form Application - Public Key Online For Free
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.
0
Forms filled
0
Forms signed
0
Forms sent
Try these PDF tools
Edit PDF
Quickly edit and annotate PDFs online.
Start now
Sign
eSign documents from anywhere.
Start now
Request signatures
Send a document for eSignature.
Start now
Share
Instantly send PDFs for review and editing.
Start now
Merge
Combine multiple PDFs into one.
Start now
Rearrange
Rearrange pages in a PDF document.
Start now
Compress
Compress PDFs to reduce their size.
Start now
Convert
Convert PDFs into Word, Excel, JPG, or PPT files and vice versa.
Start now
Create from scratch
Start with a blank page.
Start now
Edit DOC
Edit Word documents.
Start now
Discover the simplicity of processing PDFs online
Upload your document in seconds

Fill out, edit, or eSign your PDF hassle-free

Download, export, or share your edited file instantly
Top-rated PDF software recognized for its ease of use, powerful features, and impeccable support






Every PDF tool you need to get documents done paper-free
Create & edit PDFs
Generate new PDFs from scratch or transform existing documents into reusable templates. Type anywhere on a PDF, rewrite original PDF content, insert images or graphics, redact sensitive details, and highlight important information using an intuitive online editor.
Fill out & sign PDF forms
Say goodbye to error-prone manual hassles. Complete any PDF document electronically – even while on the go. Pre-fill multiple PDFs simultaneously or extract responses from completed forms with ease.
Organize & convert PDFs
Add, remove, or rearrange pages inside your PDFs in seconds. Create new documents by merging or splitting PDFs. Instantly convert edited files to various formats when you download or export them.
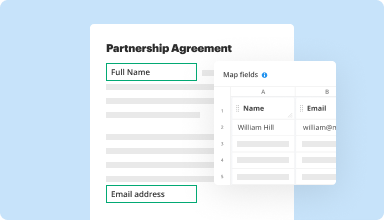
Collect data and approvals
Transform static documents into interactive fillable forms by dragging and dropping various types of fillable fields on your PDFs. Publish these forms on websites or share them via a direct link to capture data, collect signatures, and request payments.
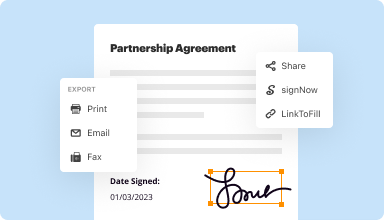
Export documents with ease
Share, email, print, fax, or download edited documents in just a few clicks. Quickly export and import documents from popular cloud storage services like Google Drive, Box, and Dropbox.
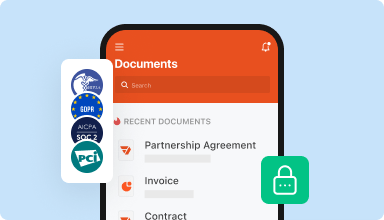
Store documents safely
Store an unlimited number of documents and templates securely in the cloud and access them from any location or device. Add an extra level of protection to documents by locking them with a password, placing them in encrypted folders, or requesting user authentication.
Customer trust by the numbers
64M+
users worldwide
4.6/5
average user rating
4M
PDFs edited per month
9 min
average to create and edit a PDF
Join 64+ million people using paperless workflows to drive productivity and cut costs
Why choose our PDF solution?
Cloud-native PDF editor
Access powerful PDF tools, as well as your documents and templates, from anywhere. No installation needed.
Top-rated for ease of use
Create, edit, and fill out PDF documents faster with an intuitive UI that only takes minutes to master.
Industry-leading customer service
Enjoy peace of mind with an award-winning customer support team always within reach.
What our customers say about pdfFiller
See for yourself by reading reviews on the most popular resources:
An easy to use program, great features, that allows you to complete and edit PDF forms. I'm no computer expert, but found this program straight forward to follow. Makes completing forms online so much easier than printing onto paper and filling out the long way. Would highly recommend it.
2018-08-19
Best filler ever! I love pdf filler. I can fill out important docs, keepbthem all in one place, fax them, save them, print them... This is a virtual office and a secretary. I love it!
2019-10-14
Makes PDF files easy to manage!
It makes it easy for our employees to attain and manage pdf files on the go. It saves every time and is easily accessible.
There are times when it takes a few times to bring up the document. This may just be an internet issue on my end.
2018-12-08
Are you one that needs to easily sign documents and return by email? this is the software to use
None
I really liked how the software navigates you through the document so quickly so you don't forget to fill in any information, and it tells you if the recipient receives it.
It's supposed to have just about any document you would need or want but I couldn't find any of the ones I needed. It was frustrating trying to look for a document and not be able to figure out where the list was.
2017-11-15
He tenido una buena experiencia, pero lo único a mejorar que al realizar cualquier modificación queden alineados al texto, ya que al guardar el documento se pierde.
2024-05-05
What do you like best?
I. An fill in forms without printing any paper.
What do you dislike?
I haven't found any downsides using pdf filler
What problems is the product solving and how is that benefiting you?
I don't have to print as many papers anymore and I can also fax without being in the office.
2022-11-08
experience
At first it seemed hard, trying to figure out how to save the completed document, and to get to the next step of saving the document and sending it by email. But I got it now. Thanks
2022-07-25
I was able to make a Loan Agreement in purchasing a Manufactured Home in Florida for my x-husband so we could have it and a POA for him at the closing on May 23, 2022. Thanks for your help in this free document service that finally worked for me. I live in Michigan and needed to protect my interest in this new home for him and two others that used to live in his Adult Foster Care Home in Grand Rapids, MI seventeen years ago. So I really appreciated your documents that we both will sign and he will have his Notarized at the Closing.
Thanks again,
Wilma Forsythe
2022-05-26
Easy of use
Easy of use, readily available help to resolve my problems in navigating the site, extensive library of forms. Very satisfied the one source of pdf fill that has worked for me.
2025-01-28
Form Application - Public Key Feature
The Form Application with Public Key feature simplifies and secures your online interactions. By leveraging public key technology, your data remains protected while enabling easy access and validation.
Key Features of Public Key
Secure data encryption and decryption
Identity verification for users
Seamless integration with existing systems
User-friendly interface for easy navigation
Scalable solutions to meet growing demands
Potential Use Cases
Securely transmitting sensitive information
Validating user identity for online services
Facilitating secure communications between parties
Enhancing e-commerce transactions with added security
Managing access control in corporate environments
With the Form Application's Public Key feature, you can address key security concerns. It helps protect your data from unauthorized access, ensuring that only intended users can obtain and use it. This simple and effective tool strengthens your online presence and builds trust with your users.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
What are the applications of public key cryptography?
Applications. The most obvious application of a public key encryption system is in encrypting communication to provide confidentiality a message that a sender encrypts using the recipient's public key can be decrypted only by the recipient's paired private key.
What is public key cryptography used for?
A Definition of Public Key Cryptography Public key cryptography uses a pair of keys to encrypt and decrypt data to protect it against unauthorized access or use. Network users receive a public and private key pair from certification authorities. This key is used to encrypt the message, and to send it to the recipient.
What is public key cryptography and why is it important?
Public key cryptography has become an important means of ensuring confidentiality, notably through its use of key distribution, where users seeking private communication exchange encryption keys. It also features digital signatures which allow users to sign keys to verify their identities.
Why is public key cryptography?
Public key cryptography uses a pair of keys to encrypt and decrypt data to protect it against unauthorized access or use. Network users receive a public and private key pair from certification authorities. If other users want to encrypt data, they get the intended recipient's public key from a public directory.
What is public key certificate and how does it work?
Public key certificates are part of a public key infrastructure that deals with digitally signed documents. The other components are public key encryption, trusted third parties (such as the certification authority), and mechanisms for certificate publication and issuing.
How many keys are there in public key cryptography and what are they used for?
For every user, there is 1 Private key and 1 Public key. The Private key is used to decrypt messages from other users. The Public key is used by everyone else to encrypt messages for that user. If you have 5 users, there are 5 Private keys and 5 Public keys.
What are the applications of cryptography?
Applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications. Cryptography prior to the modern age was effectively synonymous with encryption, the conversion of information from a readable state to apparent nonsense.
What is cryptography and its application?
Cryptography is used in many applications like banking transactions cards, computer passwords, and e- commerce transactions. Three types of cryptographic techniques used in general.
#1 usability according to G2
Try the PDF solution that respects your time.






