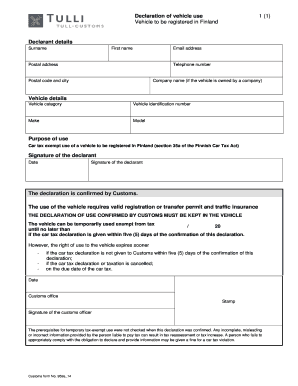
Get the free ISU Security Management Policy - isu
Show details
This document outlines the security management policies and procedures for Idaho State University, aiming to prevent, detect, contain, and correct security violations associated with electronic data.
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign isu security management policy

Edit your isu security management policy form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your isu security management policy form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing isu security management policy online
To use our professional PDF editor, follow these steps:
1
Create an account. Begin by choosing Start Free Trial and, if you are a new user, establish a profile.
2
Simply add a document. Select Add New from your Dashboard and import a file into the system by uploading it from your device or importing it via the cloud, online, or internal mail. Then click Begin editing.
3
Edit isu security management policy. Replace text, adding objects, rearranging pages, and more. Then select the Documents tab to combine, divide, lock or unlock the file.
4
Save your file. Select it in the list of your records. Then, move the cursor to the right toolbar and choose one of the available exporting methods: save it in multiple formats, download it as a PDF, send it by email, or store it in the cloud.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out isu security management policy

How to fill out ISU Security Management Policy
01
Begin by gathering all relevant information and documents that pertain to your organization's security practices.
02
Review the ISU Security Management Policy template and guidelines provided by your organization.
03
Fill in the organization’s name and relevant contact details at the top of the document.
04
Identify and outline the goals of your security management policy, ensuring alignment with organizational objectives.
05
Define the scope of the policy, specifying which departments or functions it applies to.
06
List the key roles and responsibilities associated with security management within your organization.
07
Clearly articulate the security protocols and best practices that need to be followed.
08
Outline the process for reporting security incidents and breaches.
09
Include any training requirements for staff regarding security awareness and compliance.
10
Review the policy for clarity, accuracy, and completeness; then submit it for approval to the relevant stakeholders.
Who needs ISU Security Management Policy?
01
All employees and staff members of the organization who handle sensitive data or information.
02
Management and executive teams responsible for overseeing security protocols and compliance.
03
IT and security personnel tasked with implementing and maintaining security measures.
04
External partners and vendors who may interact with the organization's data or systems.
05
Regulatory bodies or auditors who require compliance documentation and evidence of security measures.
Fill
form
: Try Risk Free






People Also Ask about
What are the three types of security policies?
The three main types of policies — organisational (master) policies, issue-specific policies, and system-specific policies — each play a critical role in a comprehensive security framework.
What are the three types of security?
The Foundation of Security. Comprehensive security is the key to any organization. There are three categories of security controls that businesses must consider: management security, operational security, and physical security. Each type is important for overall security and to protect against threats.
What are the 3 principles for the information security policy?
What are the 3 Principles of Information Security? The basic tenets of information security are confidentiality, integrity and availability. Every element of the information security program must be designed to implement one or more of these principles.
What are the 3 main data protection policies?
The GDPR outlines several core principles that should be reflected in your organization's data protection policy: Lawfulness, fairness, and transparency: Personal data must be processed in a lawful, fair, and transparent manner, with clear communication to data subjects about how their data is being used.
Where can you find the Information Security Policy and acceptable usage policy?
It is available in Lexb. It is accessible only by the Information Security group (ISG) and is available in their SharePointc.
What is a security management policy?
A security policy (also called an information security policy or IT security policy) is a document that spells out the rules, expectations, and overall approach that an organization uses to maintain the confidentiality, integrity, and availability of its data.
What are the three security policy rule types?
The three types of Security policy rules that can be created are intra-zone, inter-zone, and universal. However, the default rule type among these three is the universal rule type.
What are the 5 key elements of a security policy?
The 5 Essential Elements of an Information Security Policy Purpose and Scope. Roles and Responsibilities. Information Classification and Control. Data Protection and Privacy. Incident Response and Management.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is ISU Security Management Policy?
The ISU Security Management Policy outlines the framework and guidelines for maintaining security within the organization. It defines roles, responsibilities, and procedures to protect information, assets, and personnel.
Who is required to file ISU Security Management Policy?
All employees, contractors, and third-party vendors who have access to ISU systems or data are required to be familiar with and adhere to the ISU Security Management Policy.
How to fill out ISU Security Management Policy?
To fill out the ISU Security Management Policy, individuals should carefully read the policy document, understand the security requirements, and complete any required forms or checklists as specified in the policy.
What is the purpose of ISU Security Management Policy?
The purpose of the ISU Security Management Policy is to establish a secure environment by minimizing risk, protecting sensitive information, and ensuring compliance with legal and regulatory requirements.
What information must be reported on ISU Security Management Policy?
Information that must be reported includes security incidents, breaches, vulnerabilities, access requests, and compliance with security training or awareness programs.
Fill out your isu security management policy online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Isu Security Management Policy is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.