
Get the free effective digital forensic analysis of ntfs disk image form - ubicc
Show details
Special Issue on ICIT 2009 Conference - Applied Computing EFFECTIVE DIGITAL FORENSIC ANALYSIS OF THE NTFS DISK IMAGE Mamoun Alazab Sitalakshmi Venkatraman Paul Watters University of Ballarat Australia m.alazab s. 47264 GB 210 1024 01h C87C8h 0xAA55 CONCLUSIONS AND RESEARCH DIRECTIONS FUTURE Recent methods adopted by computer intruders attackers and malwares are to target hidden and deleted data so that they could evade from virus scanners and bec...
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign effective digital forensic analysis
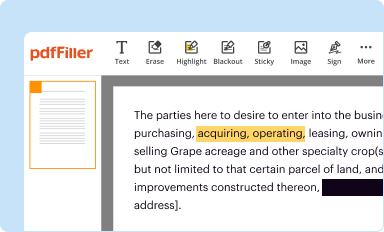
Edit your effective digital forensic analysis form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.
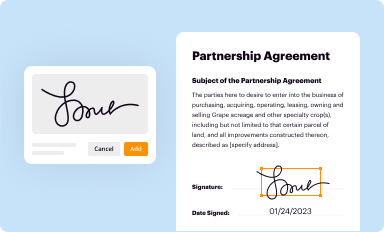
Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your effective digital forensic analysis form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit effective digital forensic analysis online
To use our professional PDF editor, follow these steps:
1
Create an account. Begin by choosing Start Free Trial and, if you are a new user, establish a profile.
2
Prepare a file. Use the Add New button. Then upload your file to the system from your device, importing it from internal mail, the cloud, or by adding its URL.
3
Edit effective digital forensic analysis. Add and change text, add new objects, move pages, add watermarks and page numbers, and more. Then click Done when you're done editing and go to the Documents tab to merge or split the file. If you want to lock or unlock the file, click the lock or unlock button.
4
Get your file. When you find your file in the docs list, click on its name and choose how you want to save it. To get the PDF, you can save it, send an email with it, or move it to the cloud.
pdfFiller makes working with documents easier than you could ever imagine. Create an account to find out for yourself how it works!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out effective digital forensic analysis
Question: Write point by point how to fill out effective digital forensic analysis. Who needs effective digital forensic analysis?
To fill out an effective digital forensic analysis, follow these steps:
01
Identify the purpose: Clearly define the objective or goal of the forensic analysis. This could be anything from investigating a cybercrime to recovering lost data.
02
Acquire relevant data: Collect all the necessary digital evidence that might be relevant to the analysis. This could include images, emails, log files, network traffic, etc.
03
Secure the evidence: Ensure that the collected evidence is secured properly to maintain its integrity. This involves making a copy of the original data and storing it in a forensically sound manner to prevent any unintended modifications.
04
Analyze the evidence: Use specialized forensic software and techniques to examine the acquired data. This may involve keyword searches, file carving, data recovery, decryption, and metadata analysis, among others.
05
Interpret the findings: Analyze the results of the forensic examination and interpret the evidence in the context of the investigation or purpose. This requires a deep understanding of digital forensics principles and methodologies.
06
Document the analysis: Record all the steps taken, findings, and interpretations in a well-documented report. This report should be detailed, accurate, and concise, ensuring that it covers all aspects of the analysis process.
07
Present the findings: Communicate the analysis results clearly and effectively to the relevant stakeholders, such as law enforcement, attorneys, or organizational management. This may involve presenting in court, providing expert testimony, or preparing executive summaries.
Who needs effective digital forensic analysis?
01
Law enforcement agencies: Digital forensic analysis is crucial for solving cybercrimes, prosecuting criminals, and gathering evidence for legal proceedings.
02
Legal professionals: Lawyers and attorneys often rely on digital forensic analysis to uncover relevant evidence in civil or criminal cases.
03
Corporations and organizations: Digital forensic analysis helps companies investigate data breaches, identify insider threats, and ensure compliance with industry regulations.
04
Government agencies: Governments employ digital forensic analysis for tasks like national security investigations, intelligence gathering, and detecting cyber threats.
05
IT security professionals: By conducting digital forensic analysis, IT professionals can identify vulnerabilities, assess the impact of security incidents, and develop strategies for future prevention.
In conclusion, an effective digital forensic analysis involves the careful acquisition, analysis, and interpretation of digital evidence. It is essential for various stakeholders, including law enforcement, legal professionals, corporations, government agencies, and IT security professionals.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I modify effective digital forensic analysis without leaving Google Drive?
Using pdfFiller with Google Docs allows you to create, amend, and sign documents straight from your Google Drive. The add-on turns your effective digital forensic analysis into a dynamic fillable form that you can manage and eSign from anywhere.
Can I create an electronic signature for the effective digital forensic analysis in Chrome?
You can. With pdfFiller, you get a strong e-signature solution built right into your Chrome browser. Using our addon, you may produce a legally enforceable eSignature by typing, sketching, or photographing it. Choose your preferred method and eSign in minutes.
How do I fill out the effective digital forensic analysis form on my smartphone?
You can quickly make and fill out legal forms with the help of the pdfFiller app on your phone. Complete and sign effective digital forensic analysis and other documents on your mobile device using the application. If you want to learn more about how the PDF editor works, go to pdfFiller.com.
What is effective digital forensic analysis?
Effective digital forensic analysis refers to the process of examining digital devices, networks, and systems to gather and analyze evidence of cybercrimes or other digital incidents. It involves the use of specialized tools and techniques to identify, collect, preserve, and analyze digital evidence in a forensically sound manner.
Who is required to file effective digital forensic analysis?
Effective digital forensic analysis is typically conducted by digital forensic analysts who are trained in the field of cybercrime investigation and forensic analysis. These professionals may work in law enforcement agencies, government organizations, or private companies that deal with cybersecurity incidents.
How to fill out effective digital forensic analysis?
Filling out an effective digital forensic analysis involves various stages and steps, including:
1. Identifying the purpose and scope of the analysis
2. Acquiring and preserving digital evidence
3. Conducting a detailed examination of the evidence
4. Analyzing the findings and drawing conclusions
5. Documenting the entire process and preparing a comprehensive report
What is the purpose of effective digital forensic analysis?
The purpose of effective digital forensic analysis is to uncover and investigate cybercrimes, security breaches, or other digital incidents. It aims to collect and analyze digital evidence that can be used in legal proceedings, incident response, or to strengthen cybersecurity measures to prevent future attacks.
What information must be reported on effective digital forensic analysis?
The information reported in an effective digital forensic analysis may vary depending on the purpose and scope of the analysis. However, typical information that may be included in the report includes details about the digital devices or systems analyzed, the methods used for acquisition and examination of evidence, the findings of the analysis, any conclusions or recommendations drawn, and the overall process followed in conducting the analysis.
Fill out your effective digital forensic analysis online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Effective Digital Forensic Analysis is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.





















