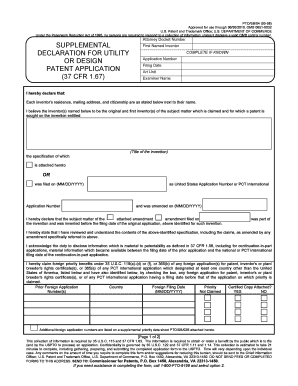
Get the free Document Title IT Security Assessment Questionnaire - umshare miami
Show details
Information Technology Security Assurance & Compliance Email: CIO Miami.edu Phone: 3052430281-Page 1 of 5 Document Title: IT Security Assessment Questionnaire Complete all required fields to the best
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign document title it security

Edit your document title it security form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your document title it security form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit document title it security online
Follow the steps below to benefit from a competent PDF editor:
1
Set up an account. If you are a new user, click Start Free Trial and establish a profile.
2
Prepare a file. Use the Add New button. Then upload your file to the system from your device, importing it from internal mail, the cloud, or by adding its URL.
3
Edit document title it security. Add and change text, add new objects, move pages, add watermarks and page numbers, and more. Then click Done when you're done editing and go to the Documents tab to merge or split the file. If you want to lock or unlock the file, click the lock or unlock button.
4
Get your file. Select the name of your file in the docs list and choose your preferred exporting method. You can download it as a PDF, save it in another format, send it by email, or transfer it to the cloud.
The use of pdfFiller makes dealing with documents straightforward.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out document title it security

How to fill out a document titled "IT Security"?
01
Start by clearly identifying the purpose of the document. Determine why you need to create a document specifically focused on IT security. This could be for internal use, to communicate with stakeholders, or to comply with legal or regulatory requirements.
02
Begin with a concise and descriptive title. The document title should clearly indicate that it pertains to IT security. Consider including additional details such as the date of creation or version number to help with organization and tracking.
03
Provide a brief introduction that outlines the scope and objectives of the document. This section should explain what the document aims to achieve and any limitations or boundaries it may have. It can serve as a high-level summary or executive summary for those who need a quick overview.
04
Clearly define the audience or intended readers of the document. Determine who will benefit from understanding the contents of the document and tailor the language and level of technical detail accordingly. This could include IT professionals, executives, or other stakeholders who need to be aware of the security measures in place.
05
Include a table of contents or an organized structure for easy navigation. Break down the document into logical sections or chapters, each addressing a specific aspect of IT security. This allows readers to quickly locate relevant information and skip to the sections they need without having to go through the entire document.
06
Provide clear and concise instructions or guidelines on IT security best practices. This may include policies, procedures, and recommended measures to protect data, systems, and networks. Use bullet points, numbered lists, or flowcharts to present information in a structured and easily understandable manner.
07
Incorporate any relevant diagrams, charts, or visuals to enhance understanding. Visual representations can help clarify complex concepts and make the document more engaging and accessible. Graphs, network diagrams, and system architectures can be particularly useful when discussing IT security.
Who needs a document titled "IT Security"?
01
IT professionals: Individuals responsible for managing and maintaining IT systems and networks will need to understand the IT security measures outlined in the document. This includes system administrators, network engineers, and cybersecurity experts.
02
Executives and decision-makers: The document can provide important insights and recommendations for executives who need to make informed decisions regarding IT security investments, strategies, and resource allocation.
03
Employees: All employees within an organization should be aware of basic IT security practices to safeguard sensitive information and prevent security breaches. The document can serve as a training resource to educate employees on their roles and responsibilities in maintaining IT security.
In conclusion, filling out a document titled "IT Security" involves clearly defining its purpose, providing a descriptive title, outlining its scope and objectives, identifying the intended audience, and organizing the content in a logical and easy-to-navigate structure. The document should be tailored to IT professionals, executives, and employees who require knowledge of IT security practices.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How do I execute document title it security online?
pdfFiller has made it simple to fill out and eSign document title it security. The application has capabilities that allow you to modify and rearrange PDF content, add fillable fields, and eSign the document. Begin a free trial to discover all of the features of pdfFiller, the best document editing solution.
How do I make edits in document title it security without leaving Chrome?
Get and add pdfFiller Google Chrome Extension to your browser to edit, fill out and eSign your document title it security, which you can open in the editor directly from a Google search page in just one click. Execute your fillable documents from any internet-connected device without leaving Chrome.
How can I fill out document title it security on an iOS device?
Install the pdfFiller app on your iOS device to fill out papers. Create an account or log in if you already have one. After registering, upload your document title it security. You may now use pdfFiller's advanced features like adding fillable fields and eSigning documents from any device, anywhere.
What is document title it security?
Document title it security refers to a form or report that outlines the security measures in place to protect sensitive information.
Who is required to file document title it security?
Organizations and businesses that handle sensitive information are required to file document title it security.
How to fill out document title it security?
Document title it security can be filled out by detailing the security measures in place, including encryption protocols, access controls, and monitoring systems.
What is the purpose of document title it security?
The purpose of document title it security is to ensure that sensitive information is adequately protected from unauthorized access and potential security breaches.
What information must be reported on document title it security?
Information such as security measures in place, potential risks, incident response procedures, and security training programs must be reported on document title it security.
Fill out your document title it security online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Document Title It Security is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.