Get the free Computer Incident Report Form - eastquogue k12 ny
Show details
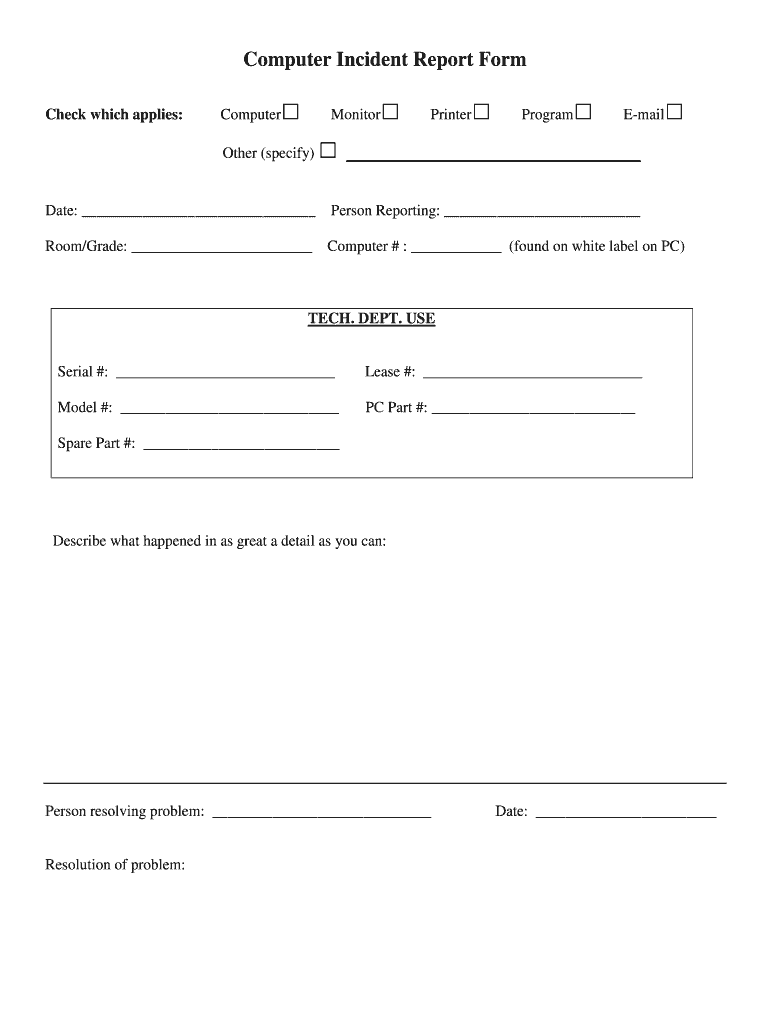
Computer Incident Report Form Check which applies: Printer Program Email Other (specify) Computer Monitor Date: Person Reporting: Room×Grade: Computer # : (found on white label on PC) TECH. DEPT.
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign computer incident report form

Edit your computer incident report form form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your computer incident report form form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit computer incident report form online
To use the professional PDF editor, follow these steps below:
1
Register the account. Begin by clicking Start Free Trial and create a profile if you are a new user.
2
Simply add a document. Select Add New from your Dashboard and import a file into the system by uploading it from your device or importing it via the cloud, online, or internal mail. Then click Begin editing.
3
Edit computer incident report form. Replace text, adding objects, rearranging pages, and more. Then select the Documents tab to combine, divide, lock or unlock the file.
4
Save your file. Select it from your records list. Then, click the right toolbar and select one of the various exporting options: save in numerous formats, download as PDF, email, or cloud.
pdfFiller makes dealing with documents a breeze. Create an account to find out!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out computer incident report form

How to fill out a computer incident report form?
01
Read the instructions: Before starting to fill out the computer incident report form, make sure to carefully read any instructions provided. These instructions will guide you on how to accurately complete the form and include all the necessary information.
02
Provide contact details: Begin by filling out your contact information, including your name, job title, department, and contact number. This helps identify the person reporting the incident and enables further communication if needed.
03
Specify the incident details: In the next section, provide a detailed description of the computer incident. Include the date, time, and location of the incident. Describe what exactly happened, how it occurred, and any specific details surrounding the event.
04
Identify affected systems or equipment: Indicate the computer systems, equipment, or software that were impacted by the incident. This could include specific devices, servers, databases, or applications. Clearly list all affected resources to ensure proper assessment and resolution.
05
Mention witnesses or involved parties: If there were any witnesses or individuals involved in the incident, provide their names and contact information. This helps establish additional testimonies or assists in conducting further investigations, if necessary.
06
Provide any evidence or supporting documentation: If you have any relevant evidence or supporting documents related to the incident, such as screenshots, error messages, or email exchanges, attach them to the form. This supporting documentation can help in the investigation or assessment process.
07
Detail the impact and severity: Describe the impact the incident had on business operations, data confidentiality, system availability, or any other relevant factors. Assess the severity of the incident, using a scale or classification provided in the form, to determine the appropriate response or priority level.
08
Suggest mitigation or corrective actions: Offer any initial recommendations for mitigating the incident or taking corrective actions. This can include steps taken to prevent similar incidents from occurring in the future or suggested improvements to existing security measures.
09
Submit the form: After completing the form, make sure to review all the information provided for accuracy and completeness. Then, follow the designated submission process, whether that's through an online platform or by physically submitting a printed copy to the designated authority.
Who needs a computer incident report form?
01
Organizations: Businesses, government agencies, educational institutions, and other organizations often require computer incident report forms. These forms aid in documenting and addressing any security breaches, system failures, or IT-related incidents that occur within their networks or infrastructure.
02
IT departments or administrators: IT departments or administrators within organizations typically use computer incident report forms. They depend on these forms to effectively track and analyze incidents, assess their impact, and develop appropriate response strategies.
03
Incident response teams: Incident response teams, comprising IT professionals specializing in handling cyber incidents or security breaches, rely on computer incident report forms. These forms provide valuable information for their investigation, analysis, and resolution efforts.
04
Compliance or regulatory bodies: Certain industries or sectors, such as banking, healthcare, or finance, may have specific regulations or compliance requirements regarding incident reporting. Compliance or regulatory bodies often mandate the use of computer incident report forms to ensure incidents are properly documented and reported.
05
Security or risk management professionals: Security or risk management professionals within organizations utilize computer incident report forms as a tool for monitoring incidents, identifying trends, and improving overall security posture. These forms allow them to assess the effectiveness of existing security measures and make necessary adjustments.
In conclusion, filling out a computer incident report form involves providing contact details, specifying incident details, identifying affected systems, mentioning witnesses or involved parties, providing evidence or supporting documentation, detailing the impact and severity, suggesting mitigation or corrective actions, and finally submitting the form. The form is typically required by organizations, IT departments, incident response teams, compliance or regulatory bodies, and security or risk management professionals.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How do I edit computer incident report form online?
With pdfFiller, it's easy to make changes. Open your computer incident report form in the editor, which is very easy to use and understand. When you go there, you'll be able to black out and change text, write and erase, add images, draw lines, arrows, and more. You can also add sticky notes and text boxes.
How do I fill out computer incident report form using my mobile device?
You can easily create and fill out legal forms with the help of the pdfFiller mobile app. Complete and sign computer incident report form and other documents on your mobile device using the application. Visit pdfFiller’s webpage to learn more about the functionalities of the PDF editor.
How do I complete computer incident report form on an Android device?
On Android, use the pdfFiller mobile app to finish your computer incident report form. Adding, editing, deleting text, signing, annotating, and more are all available with the app. All you need is a smartphone and internet.
What is computer incident report form?
The computer incident report form is a document used to record details of any computer or network security breaches or incidents.
Who is required to file computer incident report form?
Any organization or individual who experiences a computer or network security incident is required to file a computer incident report form.
How to fill out computer incident report form?
To fill out the computer incident report form, one must provide detailed information about the incident, including the date and time of occurrence, nature of the incident, impact on the system, and any remediation steps taken.
What is the purpose of computer incident report form?
The purpose of the computer incident report form is to document and investigate security incidents, assess the impact on systems, and implement measures to prevent similar incidents in the future.
What information must be reported on computer incident report form?
Information such as the date and time of the incident, description of the incident, affected systems or data, and any actions taken in response to the incident must be reported on the computer incident report form.
Fill out your computer incident report form online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Computer Incident Report Form is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.





















