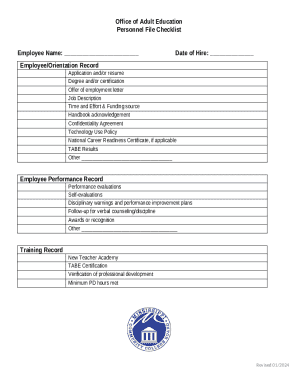
Get the free Secure & Forensic Secondary Commissioning Panel Operational Policy .doc
Show details
SUSSEX PARTNERSHIP NHS FOUNDATION TRUST SECURE AND FORENSIC SECONDARY COMMISSIONING PANEL OPERATIONAL POLICY Managing Individual Placements and Funding Applications Secure and Forensic Services 1
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign secure amp forensic secondary

Edit your secure amp forensic secondary form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your secure amp forensic secondary form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit secure amp forensic secondary online
Here are the steps you need to follow to get started with our professional PDF editor:
1
Log in to your account. Click on Start Free Trial and sign up a profile if you don't have one yet.
2
Simply add a document. Select Add New from your Dashboard and import a file into the system by uploading it from your device or importing it via the cloud, online, or internal mail. Then click Begin editing.
3
Edit secure amp forensic secondary. Text may be added and replaced, new objects can be included, pages can be rearranged, watermarks and page numbers can be added, and so on. When you're done editing, click Done and then go to the Documents tab to combine, divide, lock, or unlock the file.
4
Get your file. Select your file from the documents list and pick your export method. You may save it as a PDF, email it, or upload it to the cloud.
pdfFiller makes working with documents easier than you could ever imagine. Register for an account and see for yourself!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out secure amp forensic secondary

How to fill out secure amp forensic secondary
01
Step 1: Collect all relevant information and documents needed to fill out the secure amp forensic secondary form.
02
Step 2: Carefully read and understand the provided instructions and guidelines for completing the form.
03
Step 3: Start by filling out basic personal details, such as name, contact information, and identification number.
04
Step 4: Proceed to fill out the required sections related to the specific forensic investigation or analysis being conducted.
05
Step 5: Provide detailed and accurate information regarding the purpose, scope, and objectives of the investigation or analysis.
06
Step 6: Include any supporting evidence or documentation that may be necessary for reviewing the application.
07
Step 7: Double-check all the entered information to ensure accuracy and completeness.
08
Step 8: Submit the form along with any required attachments or supporting documentation as instructed.
09
Step 9: Follow up on the status of the application if necessary.
10
Step 10: Keep a copy of the filled-out form and any submitted documents for your records.
Who needs secure amp forensic secondary?
01
People or organizations involved in forensic investigations or analyses requiring secure data processing and documentation may need to fill out the secure amp forensic secondary form.
02
Law enforcement agencies, forensic laboratories, private investigators, or professionals involved in analyzing digital evidence may require this form.
03
Individuals or organizations conducting forensic audits, data breach investigations, or any other type of digital forensics may also need to complete this form.
04
The secure amp forensic secondary form ensures that sensitive forensic data is handled securely and appropriately, making it necessary for anyone involved in these types of investigations or analyses.
05
It helps maintain the integrity and confidentiality of the collected evidence and ensures compliance with legal and ethical standards in forensic procedures.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How do I execute secure amp forensic secondary online?
Filling out and eSigning secure amp forensic secondary is now simple. The solution allows you to change and reorganize PDF text, add fillable fields, and eSign the document. Start a free trial of pdfFiller, the best document editing solution.
How do I edit secure amp forensic secondary online?
pdfFiller not only lets you change the content of your files, but you can also change the number and order of pages. Upload your secure amp forensic secondary to the editor and make any changes in a few clicks. The editor lets you black out, type, and erase text in PDFs. You can also add images, sticky notes, and text boxes, as well as many other things.
How do I edit secure amp forensic secondary straight from my smartphone?
The pdfFiller mobile applications for iOS and Android are the easiest way to edit documents on the go. You may get them from the Apple Store and Google Play. More info about the applications here. Install and log in to edit secure amp forensic secondary.
What is secure amp forensic secondary?
Secure amp forensic secondary is a form used to report sensitive information related to security incidents and forensic investigations.
Who is required to file secure amp forensic secondary?
Organizations that have experienced security incidents or are undergoing forensic investigations are required to file secure amp forensic secondary.
How to fill out secure amp forensic secondary?
Secure amp forensic secondary should be filled out by providing detailed information about the security incident or forensic investigation, including dates, details, and outcomes.
What is the purpose of secure amp forensic secondary?
The purpose of secure amp forensic secondary is to ensure that sensitive information related to security incidents and forensic investigations is reported accurately and in a timely manner.
What information must be reported on secure amp forensic secondary?
Information such as the nature of the security incident, actions taken to mitigate the incident, and findings from forensic investigations must be reported on secure amp forensic secondary.
Fill out your secure amp forensic secondary online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Secure Amp Forensic Secondary is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.