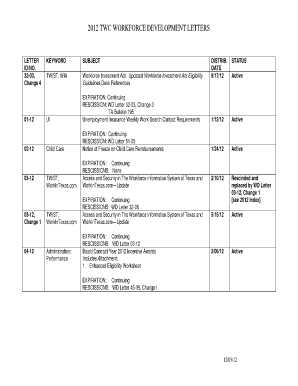
Get the free Security in Pervasive Computing: First International ...
Show details
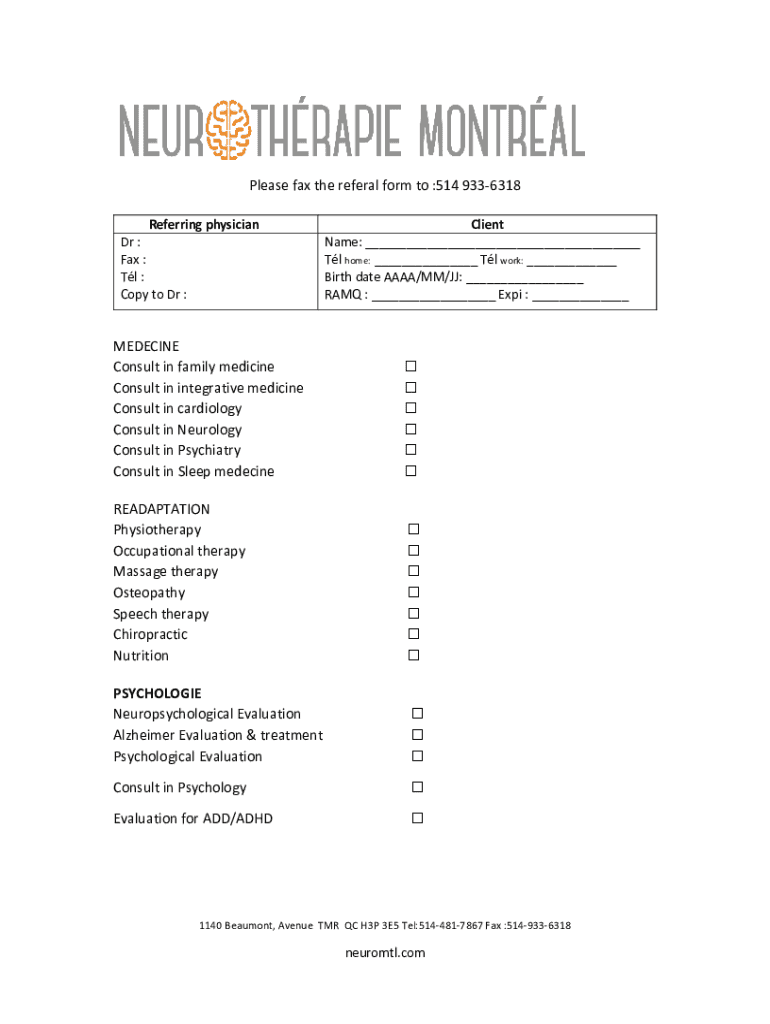
Please fax the referral form to :514 9336318 Referring physician Dr : Fax : Tl : Copy to Dr :Client Name: Tl home: Tl work: Birth date AAAA/MM/JJ: RAMQ : Exp : MEDICINE Consult in family medicine
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign security in pervasive computing

Edit your security in pervasive computing form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your security in pervasive computing form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing security in pervasive computing online
To use our professional PDF editor, follow these steps:
1
Check your account. It's time to start your free trial.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit security in pervasive computing. Text may be added and replaced, new objects can be included, pages can be rearranged, watermarks and page numbers can be added, and so on. When you're done editing, click Done and then go to the Documents tab to combine, divide, lock, or unlock the file.
4
Save your file. Select it from your list of records. Then, move your cursor to the right toolbar and choose one of the exporting options. You can save it in multiple formats, download it as a PDF, send it by email, or store it in the cloud, among other things.
Dealing with documents is simple using pdfFiller. Try it right now!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out security in pervasive computing

How to fill out security in pervasive computing
01
To fill out security in pervasive computing, follow these steps:
02
Identify the potential security risks and threats in the pervasive computing environment.
03
Implement strong authentication mechanisms to ensure that only authorized users can access the system.
04
Encrypt sensitive data to protect it from interception or unauthorized access.
05
Use secure communication protocols to ensure the confidentiality and integrity of data transmission.
06
Implement access control mechanisms to restrict the actions that users can perform within the system.
07
Regularly update and patch the software and firmware in the pervasive computing devices to address any security vulnerabilities.
08
Implement intrusion detection and prevention systems to detect and mitigate any unauthorized activities.
09
Educate users about best practices for security and raise awareness about potential security risks.
10
Monitor and audit the system to identify any security incidents and take appropriate actions to mitigate them.
11
Continuously evaluate and improve the security measures in the pervasive computing environment to adapt to evolving threats.
Who needs security in pervasive computing?
01
Anyone who uses or deploys pervasive computing systems needs security. This includes individuals, businesses, government organizations, and institutions.
02
Pervasive computing involves the use of interconnected devices and systems, such as IoT devices, wearable devices, and smart appliances. These devices collect, process, and transmit data, making them vulnerable to security threats.
03
Security in pervasive computing is essential to protect sensitive information, ensure privacy, prevent unauthorized access, and maintain the integrity and availability of the system.
04
Individuals who use pervasive computing devices, such as smartphones or smart home devices, need security to protect their personal data and privacy.
05
Businesses and organizations that deploy pervasive computing systems need security to protect their sensitive data, intellectual property, and customer information.
06
Government organizations need security in pervasive computing to protect critical infrastructure, sensitive information, and national security.
07
Institutions, such as hospitals or universities, need security in pervasive computing to protect patient records, research data, and sensitive information.
08
In summary, anyone who interacts with or deploys pervasive computing systems needs security to protect their data, privacy, and overall system integrity.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How do I fill out the security in pervasive computing form on my smartphone?
The pdfFiller mobile app makes it simple to design and fill out legal paperwork. Complete and sign security in pervasive computing and other papers using the app. Visit pdfFiller's website to learn more about the PDF editor's features.
How do I edit security in pervasive computing on an Android device?
You can make any changes to PDF files, such as security in pervasive computing, with the help of the pdfFiller mobile app for Android. Edit, sign, and send documents right from your mobile device. Install the app and streamline your document management wherever you are.
How do I fill out security in pervasive computing on an Android device?
Use the pdfFiller app for Android to finish your security in pervasive computing. The application lets you do all the things you need to do with documents, like add, edit, and remove text, sign, annotate, and more. There is nothing else you need except your smartphone and an internet connection to do this.
What is security in pervasive computing?
Security in pervasive computing refers to the protection of data and resources in environments where computing devices are embedded in everyday objects, ensuring that information is kept confidential, intact, and available only to authorized users.
Who is required to file security in pervasive computing?
Individuals or organizations that utilize pervasive computing technologies and store, process, or transmit sensitive data are required to file security measures and reports to comply with relevant regulations.
How to fill out security in pervasive computing?
To fill out security in pervasive computing, individuals or organizations must provide detailed documentation regarding their data protection strategies, risk assessment protocols, and compliance measures outlining how they safeguard information in pervasive environments.
What is the purpose of security in pervasive computing?
The purpose of security in pervasive computing is to mitigate risks associated with data breaches, unauthorized access, and misuse of personal information, thus ensuring the privacy and trust of users in these interconnected systems.
What information must be reported on security in pervasive computing?
Reports on security in pervasive computing must include details about the architecture of the system, data handling practices, security protocols implemented, risk assessment findings, and incident response plans.
Fill out your security in pervasive computing online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Security In Pervasive Computing is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.