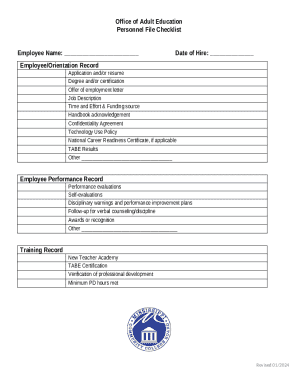
Get the free BISHOP FOX CYBERSECURITY STYLE GUIDE
Show details
BISHOP FOX CYBERSECURITY STYLE GUIDE VERSION 1.1 JUNE 27, 2018This work is licensed under a Creative Commons AttributionShareAlike 2.0 Generic License. Bishop Fox Contact Information: +1 ×480× 6218967
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign bishop fox cybersecurity style

Edit your bishop fox cybersecurity style form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your bishop fox cybersecurity style form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit bishop fox cybersecurity style online
To use the professional PDF editor, follow these steps:
1
Log in to account. Click Start Free Trial and register a profile if you don't have one yet.
2
Prepare a file. Use the Add New button to start a new project. Then, using your device, upload your file to the system by importing it from internal mail, the cloud, or adding its URL.
3
Edit bishop fox cybersecurity style. Rearrange and rotate pages, add and edit text, and use additional tools. To save changes and return to your Dashboard, click Done. The Documents tab allows you to merge, divide, lock, or unlock files.
4
Get your file. When you find your file in the docs list, click on its name and choose how you want to save it. To get the PDF, you can save it, send an email with it, or move it to the cloud.
It's easier to work with documents with pdfFiller than you can have believed. You may try it out for yourself by signing up for an account.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out bishop fox cybersecurity style

How to fill out bishop fox cybersecurity style
01
To fill out Bishop Fox Cybersecurity Style, follow these steps:
02
Begin by opening the Bishop Fox Cybersecurity Style document on your computer.
03
Read through the document carefully to understand the requirements and guidelines.
04
Start by entering the title of your document at the top. Make sure it accurately represents the content.
05
Use appropriate headings and subheadings to structure your document.
06
Write the content of your document following the Bishop Fox Cybersecurity Style guidelines, which include clear and concise language, avoiding jargon or technical terms unless necessary, and providing accurate and reliable information.
07
Include relevant references and citations if required.
08
Proofread your document for grammar, spelling, and formatting errors.
09
Once you are satisfied with your document, save it in the desired format and location.
10
Submit or share the filled-out Bishop Fox Cybersecurity Style document as instructed.
Who needs bishop fox cybersecurity style?
01
The Bishop Fox Cybersecurity Style is beneficial for anyone or any organization involved in the field of cybersecurity. This style guide provides guidelines and best practices for writing cybersecurity-related documents, ensuring clarity, consistency, and professionalism in communication. It is useful for cybersecurity professionals, researchers, students, and organizations that deal with cybersecurity-related topics, including but not limited to developing policies, writing reports, creating training materials, or communicating with stakeholders. By following the Bishop Fox Cybersecurity Style, individuals and organizations can enhance the effectiveness and professionalism of their written communication in the cybersecurity domain.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I modify bishop fox cybersecurity style without leaving Google Drive?
You can quickly improve your document management and form preparation by integrating pdfFiller with Google Docs so that you can create, edit and sign documents directly from your Google Drive. The add-on enables you to transform your bishop fox cybersecurity style into a dynamic fillable form that you can manage and eSign from any internet-connected device.
How do I edit bishop fox cybersecurity style straight from my smartphone?
The best way to make changes to documents on a mobile device is to use pdfFiller's apps for iOS and Android. You may get them from the Apple Store and Google Play. Learn more about the apps here. To start editing bishop fox cybersecurity style, you need to install and log in to the app.
How do I complete bishop fox cybersecurity style on an iOS device?
pdfFiller has an iOS app that lets you fill out documents on your phone. A subscription to the service means you can make an account or log in to one you already have. As soon as the registration process is done, upload your bishop fox cybersecurity style. You can now use pdfFiller's more advanced features, like adding fillable fields and eSigning documents, as well as accessing them from any device, no matter where you are in the world.
What is bishop fox cybersecurity style?
Bishop Fox cybersecurity style refers to the methodology and practices used by Bishop Fox, a cybersecurity consulting firm, to assess and address security vulnerabilities.
Who is required to file bishop fox cybersecurity style?
Companies and organizations seeking to improve their cybersecurity posture can benefit from using Bishop Fox cybersecurity style.
How to fill out bishop fox cybersecurity style?
Bishop Fox cybersecurity style can be implemented by hiring Bishop Fox consultants or by following their recommended best practices and recommendations.
What is the purpose of bishop fox cybersecurity style?
The purpose of Bishop Fox cybersecurity style is to help organizations identify and mitigate cybersecurity risks, protect sensitive information, and improve overall security posture.
What information must be reported on bishop fox cybersecurity style?
Information that must be reported on Bishop Fox cybersecurity style includes identified vulnerabilities, risk assessments, and recommended security measures.
Fill out your bishop fox cybersecurity style online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Bishop Fox Cybersecurity Style is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.