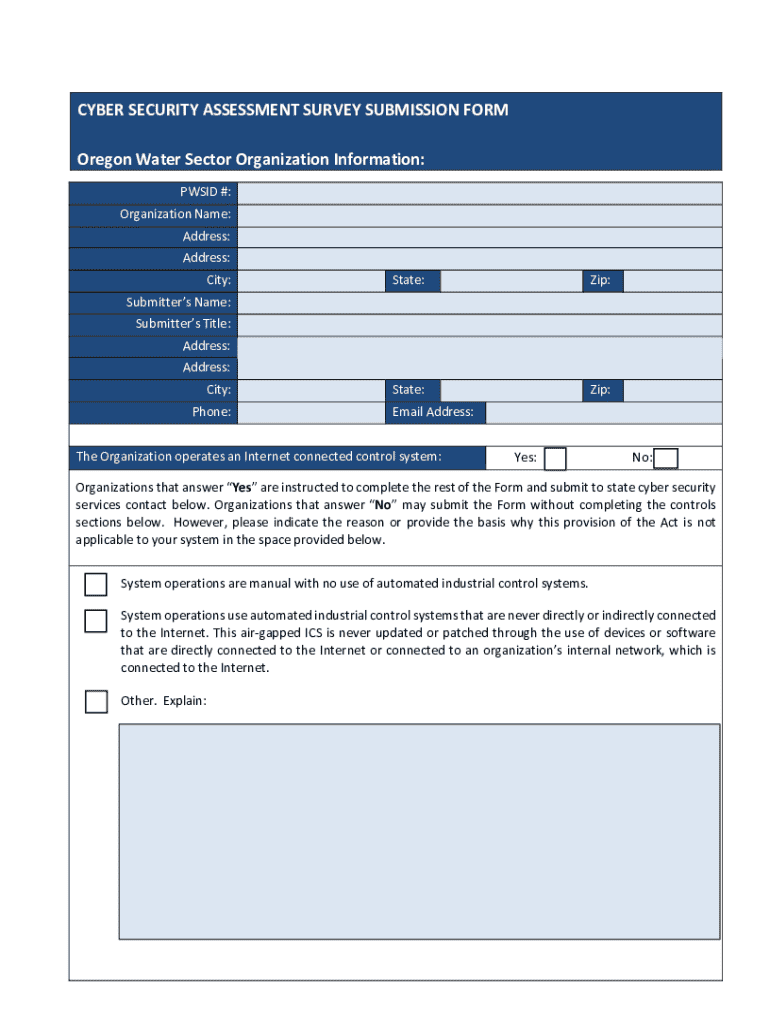
Get the free Cybersecurity Assessment Form
Get, Create, Make and Sign cybersecurity assessment form



How to edit cybersecurity assessment form online
Uncompromising security for your PDF editing and eSignature needs
How to fill out cybersecurity assessment form

How to fill out cybersecurity assessment form
Who needs cybersecurity assessment form?
Comprehensive Guide to the Cybersecurity Assessment Form
Understanding cybersecurity assessments
A cybersecurity assessment is a systematic evaluation of an organization’s information systems and security measures. It encompasses various methodologies designed to identify vulnerabilities, determine risk levels, and assess the effectiveness of current controls. In an era where digital breaches are rampant, conducting a cybersecurity assessment is crucial. It not only protects sensitive data but also preserves trust and compliance with legal obligations.
The key objectives of a cybersecurity assessment include understanding the threat landscape, evaluating current vulnerabilities, and determining compliance with cybersecurity regulations. Organizations often face pressures to conduct these assessments due to regulatory compliance, where laws like GDPR and HIPAA impose strict obligations. Furthermore, these evaluations help mitigate risks by reinforcing security protocols, ultimately ensuring stakeholder assurance.
Overview of the cybersecurity assessment form
A cybersecurity assessment form serves as a critical tool for documenting the findings of an assessment. It includes a set of predefined questions and checklists structured to gather essential information about an organization’s cybersecurity posture. Each item within the form is designed to facilitate discussions regarding potential vulnerabilities, existing measures, and areas requiring improvement.
The key components of an effective assessment form often include personal and organizational information, a review of current cybersecurity policies and practices, and specific criteria for vulnerability assessment. This structure helps ensure a comprehensive overview essential for detailed analysis and remediation planning.
Types of cybersecurity assessment forms
Cybersecurity assessment forms are not one-size-fits-all; they vary significantly based on industry needs and specific requirements of an organization. Standard assessment forms are broadly applicable but often lack the specificity needed for niche markets.
Industry-specific assessment templates, tailored to areas such as healthcare or finance, address unique regulatory and operational challenges faced by these sectors. Additionally, organizations may require tailored forms for specific needs, such as assessments geared towards remote work environments or vendor risk assessments, ensuring they adequately address all potential threats.
Filling out the cybersecurity assessment form
Completing a cybersecurity assessment form can seem daunting, but a structured approach can simplify the process. Begin by gathering all necessary information about the organization’s current cybersecurity landscape, including existing policies, technologies in use, and past security incidents.
Next, address the questionnaire items effectively, considering the current threat landscape and performing thorough risk evaluations. Each response should be documented with existing controls in place, highlighting any gaps or areas for improvement. This structured input is pivotal for a successful assessment outcome.
To ensure accurate and comprehensive responses, collaboration with team members is essential. Engaging relevant teams can yield insights and leverage existing reports and data, leading to a more effective cybersecurity assessment.
Editing and customizing your cybersecurity assessment form
After collecting and documenting the required information, it’s crucial to ensure that your cybersecurity assessment form is tailored to your organization’s specific needs. Utilizing digital tools offered by pdfFiller can significantly enhance this process. With features like interactive form fields and easy modification options, users can customize templates to ensure all critical areas are addressed.
Best practices for customizing the forms include adding additional questions and modifying templates for specific use-cases, ensuring that the final product reflects the unique requirements of your organization while maintaining a comprehensive structure.
Signing and securing your assessment form
The security and authenticity of the cybersecurity assessment form are paramount. eSigning these forms not only enhances security but also ensures compliance with legal standards. The eSignature features provided by pdfFiller can streamline this process, allowing users to sign documents easily while maintaining an audit trail.
By leveraging these features, organizations can ensure that their assessments are legally binding and that changes made to the document can be tracked and reviewed efficiently, which is essential for maintaining transparency with stakeholders.
Managing and sharing your cybersecurity assessment form
After creation, effectively managing and sharing the cybersecurity assessment form becomes crucial. Storing forms securely in the cloud not only protects sensitive information but also allows for easy access from anywhere. pdfFiller provides robust cloud storage options, ensuring your forms are safely backed and accessible for review.
When sharing the form with stakeholders, best practices include implementing permissions and access controls to restrict who can view or edit the document. Tracking revisions and feedback is also essential for continual improvement and to incorporate input from various teams.
Utilizing the results of your cybersecurity assessment
The completion of the cybersecurity assessment form is just the beginning. Analyzing the assessment outcomes is critical for identifying areas needing attention. Organizations should prioritize remediation efforts based on the findings, addressing the most significant risks first. This actionable insight is essential for not only rectifying discovered vulnerabilities but also for fortifying overall cybersecurity posture.
Continuous monitoring and reassessing cybersecurity measures based on assessment outcomes foster an environment of proactive security management. This iterative process is increasingly vital in addressing ever-evolving threats.
Tools and resources for cybersecurity assessments
Incorporating various tools can enhance the effectiveness of your cybersecurity assessment process. Recommended tools include vulnerability scanners that can automate the detection of weaknesses in your systems and threat intelligence platforms that provide valuable insights into emerging risks.
Beyond tools, additional resources such as guides, whitepapers, and community forums serve as platforms for shared knowledge and best practices in the cybersecurity realm. These resources can inform and influence how assessments are structured and conducted.
Key considerations and common pitfalls in cybersecurity assessments
Despite the best intentions, common mistakes in cybersecurity assessments can undermine the process. Critical pitfalls include inadequate stakeholder engagement, which can lead to information gaps, and neglecting external threats that may target the organization. These oversights can create vulnerabilities that go unaddressed.
Utilizing feedback from assessments to improve future evaluations is vital. By identifying shortcomings and implementing best practices, organizations can elevate their cybersecurity posture and better prepare for future risks.
Cybersecurity assessment case studies
Examining real-world examples of successful cybersecurity assessments showcases the impact effective evaluations can achieve. Organizations that have conducted thorough assessments often highlight increased security measures, reduced vulnerabilities, and enhanced compliance with regulations as their key outcomes.
Learning from these case studies enables other organizations to adapt successful strategies and avoid common pitfalls, reinforcing the importance of continual improvement and adaptation in cybersecurity strategies.
Future trends in cybersecurity assessments
Cybersecurity assessments continue to evolve alongside new technologies and emerging threats. Organizations must remain vigilant to adapt their assessments to the changing landscape. Evolving threat landscapes necessitate agile assessment frameworks to quickly address new risks.
Innovations such as AI and automation are beginning to play crucial roles in assessing vulnerabilities in real-time. As businesses move towards more dynamic environments, the importance of implementing ongoing assessments that prioritize adaptive strategies will only grow.






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I manage my cybersecurity assessment form directly from Gmail?
Can I sign the cybersecurity assessment form electronically in Chrome?
How do I edit cybersecurity assessment form on an Android device?
What is cybersecurity assessment form?
Who is required to file cybersecurity assessment form?
How to fill out cybersecurity assessment form?
What is the purpose of cybersecurity assessment form?
What information must be reported on cybersecurity assessment form?
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.















