Your Complete Guide to Creating a Cloud Security Policy Template Form
Understanding the cloud security policy
Cloud security policies serve as the foundational guidelines that dictate how organizations protect their data in cloud environments. These policies articulate the strategies and protocols necessary to mitigate risks associated with data breaches and cyber threats. As organizations increasingly migrate to the cloud, establishing a robust security policy becomes paramount to ensure data integrity, confidentiality, and availability.
In a cloud context, the importance of security extends beyond traditional IT boundaries, emphasizing the need for tailored strategies that encompass cloud service providers, shared responsibilities, and regulatory compliance. Key components of a cloud security policy include access control, data protection, incident response, and monitoring efforts. By addressing these components, businesses can adopt a proactive approach to cybersecurity excellence and data governance.
Why you need a cloud security policy template
A cloud security policy template provides a structured foundation for organizations to develop their own security policies. Utilizing a template yields numerous benefits, including significant time savings and resource optimization in policy creation. It acts as a framework that guides teams through the complexities of ensuring compliance with various regulations, thus reducing the likelihood of missteps and enhancing overall cybersecurity posture.
Saves time and effort: By relying on a pre-existing template, teams can focus on customizing sections relevant to their specific needs rather than starting from scratch.
Ensures compliance with regulations: Adhering to industry standards is crucial, and a template provides a roadmap to meet these requirements effectively.
Facilitates collaboration and standardization: A unified template allows various stakeholders to contribute to the policy seamlessly, ensuring everyone is on the same page.
Common scenarios where a cloud security policy is essential include employee onboarding processes, third-party vendor assessments, and incidents involving data breaches. Each of these scenarios requires a well-defined approach to security to safeguard sensitive information.
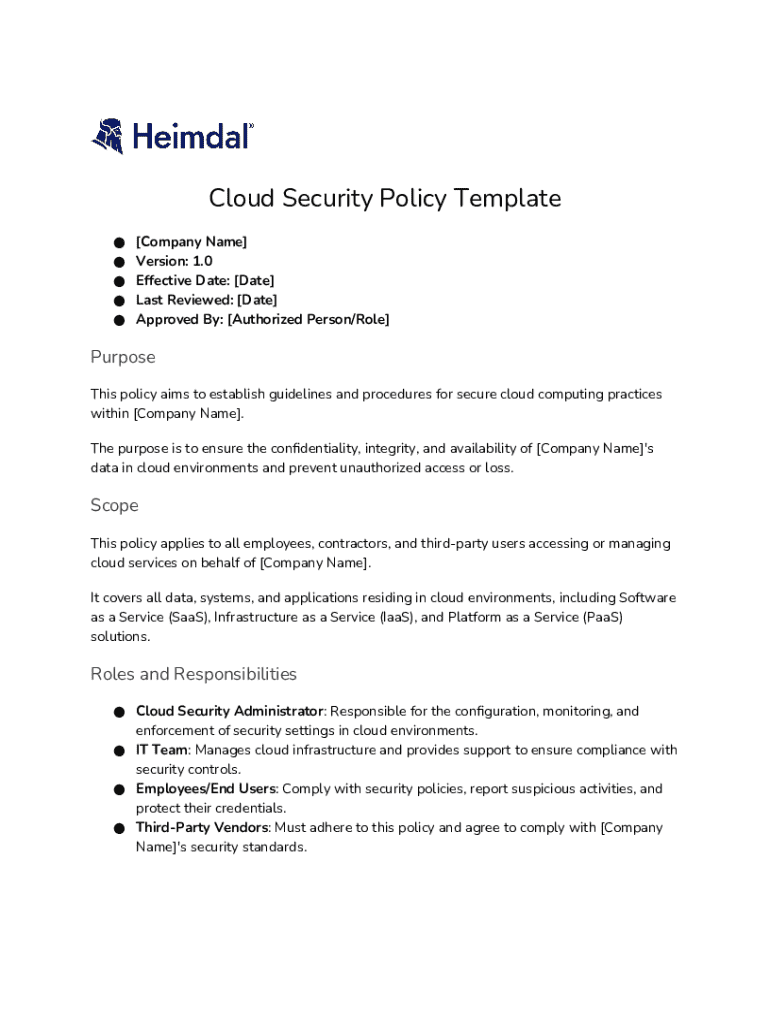
What’s included in the cloud security policy template
A comprehensive cloud security policy template is made up of several vital sections that ensure it addresses the security challenges organizations face. Understanding these sections helps organizations tailor their policies to fit their specific needs effectively.
Purpose and scope: This section outlines the document's objectives and the specific cloud environments and services it applies to.
Roles and responsibilities: Defining who is responsible for security measures helps establish accountability across the organization.
Data protection measures: This includes policies on data encryption, access controls, and monitoring to safeguard sensitive information.
Incident response procedures: This section outlines steps for addressing security breaches, ensuring prompt mitigation and recovery.
Customization options allow organizations of various sizes—whether startups or established enterprises—to adapt the template based on their unique workflows and operational needs. Balancing comprehensive coverage with flexibility is crucial for effective policy implementation.
Step-by-step guide to filling out the cloud security policy template
Before diving into the template, preparing adequately is critical. Gather necessary information, including existing policies, legal requirements, and key stakeholders who can contribute valuable insights.
Filling out the template: Section-by-section
Personalizing the purpose and scope: Modify this section to reflect your organization's specific cloud usage and security aspirations.
Defining roles and responsibilities: Establish clear lines of accountability to ensure thorough implementation of security practices.
Implementing data protection strategies: Assess current data environments and define measures that align with best practices for data security.
Establishing incident response protocols: Outline procedures that your team will follow in the event of a security incident, ensuring they are well-practiced.
Documenting these aspects effectively requires not just attention to detail, but also clarity in communication. Tips for successful documentation include maintaining a straightforward language and avoiding jargon where possible, which aids in understanding across different organizational levels.
Interactive tools and features for enhanced collaboration
Using pdfFiller’s editing tools can significantly enhance collaboration when filling out a cloud security policy template. Users can highlight sections that need attention and leave comments for team members, streamlining the review process.
Highlighting and commenting: Annotate the template to draw attention to specific areas that require discussion or revision.
Version control: Keep track of all changes made to the document, ensuring that you can revert to prior versions if necessary.
eSigning the completed policy: Use electronic signatures to expedite the policy approval process, making it easier to enforce the policy swiftly.
Collaborating with teams: Utilize sharing features to distribute the template among team members and gather their feedback in real time.
These interactive capabilities streamline the workflow, making it easier for organizations to adopt comprehensive security strategies effectively. The ability to work collaboratively ensures that diverse viewpoints are integrated into the final document.
Best practices for managing your cloud security policy
The dynamic nature of cloud services necessitates that organizations regularly review and update their security policies. Implementing a cycle of continuous improvement helps to keep the policies relevant and effective against emerging threats and compliance requirements.
Regular reviews and updates: Establish a schedule for policy reviews to incorporate changes in technology, regulations, and organizational structure.
Training staff on policy importance and compliance: Educate employees on the policy's content and the significance of adhering to it, fostering a culture of security.
Incorporating feedback for continuous improvement: Create an environment where team members can suggest enhancements to the policy, ensuring it evolves to meet new challenges.
By investing time in these best practices, organizations can create a robust framework that strengthens their cybersecurity defenses while supporting business objectives.
Real-world examples of effective cloud security policies
Exploring case studies and real-world examples of successful cloud security policy implementation provides valuable lessons. Organizations that prioritize their cloud security policies frequently report lower instances of data breaches and improved compliance with regulatory standards.
Case study A: This tech startup implemented a comprehensive cloud security policy that resulted in a 40% reduction in security incidents.
Case study B: A financial institution utilized a robust template to enhance their data protection measures, leading to improved compliance ratings.
Lessons learned from notable breaches highlight the absence of a structured policy as a common denominator in many incidents. On the other hand, organizations actively maintaining and refining their cloud security policies can experience significant improvements in their cybersecurity resilience.
FAQs about cloud security policies
Addressing common questions and misconceptions about cloud security policies is crucial for fostering understanding and compliance throughout an organization. Many individuals are unaware of the evolving nature of threats and the necessity for policies that adapt to these changes.
What is the primary purpose of a cloud security policy? It serves as a guideline for protecting data in cloud environments and ensuring compliance with legal and regulatory requirements.
How often should cloud security policies be reviewed? Organizations should aim for quarterly reviews to address emerging threats and technological advancements.
Who should be involved in creating and updating the policy? Collaboration across various teams, including IT, legal, and operations, is essential for comprehensive policy development.
Seeking help from cybersecurity professionals can provide additional support and insights to refine your cloud security strategies effectively.
Final thoughts on utilizing a cloud security policy template
A well-crafted cloud security policy template is crucial for organizations seeking to protect their data while navigating the complexities of cloud computing. It offers a structured approach to defining security measures tailored to various workflows and compliance requirements. By leveraging interactive tools like pdfFiller, you can create, manage, and modify your cloud security policy efficiently, ensuring your organization is well-equipped to face the ever-evolving cybersecurity landscape.