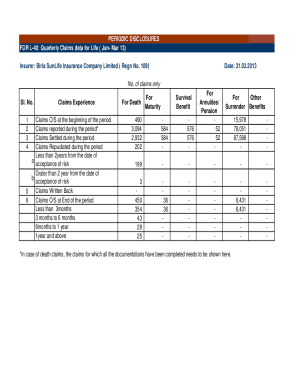
Get the free Analysis of Manual Threat Evaluation and Weapons Assignment ...
Get, Create, Make and Sign analysis of manual threat

How to edit analysis of manual threat online
Uncompromising security for your PDF editing and eSignature needs
How to fill out analysis of manual threat
How to fill out analysis of manual threat
Who needs analysis of manual threat?
Analysis of Manual Threat Form: A Comprehensive Guide
Understanding manual threat forms
A manual threat form serves as a structured document utilized for recording potential risks that could impact an organization's operations, reputation, or security posture. The proactive identification and assessment of threats allow organizations to implement appropriate strategies to mitigate these risks before they manifest.
Manual threat forms, typically part of a larger risk management framework, hold critical value across industries. Their design emphasizes the importance of thorough documentation, enabling organizations to maintain an organized approach in identifying, analyzing, and responding to threats. There are numerous instances in which these forms are essential, including cybersecurity assessments, physical security evaluations, and compliance audits.
Components of a manual threat form
A well-structured manual threat form comprises several essential sections designed to capture all relevant details of a potential threat. Each component plays a vital role in ensuring that the analysis conducted is comprehensive and actionable.
The primary sections include a description of the threat, context and impact assessment, likelihood of occurrence, and mitigation recommendations. Each section requires careful consideration and specificity to ensure clarity and facilitate thorough analysis.
Examples of effective manual threat forms can provide guidance on structuring your own landing page, ensuring all important aspects are covered succinctly.
Best practices for filling out manual threat forms
To maximize the efficacy of manual threat forms, it is essential to adopt best practices during the completion process. This involves a systematic approach that encompasses gathering required information, obtaining input from relevant stakeholders, and accurately assessing potential threats.
Begin by collecting all necessary data related to the threat; this may involve interviews with team members or reviewing past incident reports. Engaging stakeholders is crucial, as diverse perspectives can aid in painting a fuller picture of the potential threat and its implications.
Clarity and precision in filling out these forms cannot be overstated. Avoid ambiguity by using straightforward language and defining technical terms when necessary. The goal is to ensure that any individual reviewing the form can easily understand the presented information.
Editing and reviewing manual threat forms
Once the manual threat form is completed, it is crucial to undergo a collaborative review process. Collaboration fosters a culture of thoroughness in which multiple eyes scrutinize the document for accuracy and comprehensiveness. By involving diverse members of the organization, it encourages mutual understanding of threats and applicable mitigation strategies.
Incorporating feedback is essential. Feedback should be collected systematically, allowing for relevant modifications based on insights received. Ensure that those revising the document understand its context, so their suggestions are constructive and aligned with organizational standards.
Tracking and managing manual threat forms
Effective tracking and management of manual threat forms are key to ensuring that the information remains accessible and actionable. Organizing document submissions can streamline the review processes and ensure timely responses to identified threats.
Utilizing cloud-based solutions allows for easy access, on-the-go edits, and secure sharing among team members. Tools like pdfFiller can facilitate efficient document handling, while version control helps manage iterations of the threat forms, allowing teams to refer back to previous versions as needed.
Analyzing and interpreting threat form data
Collecting and analyzing data from manual threat forms provides actionable insights that can guide organizational strategies and improvements. Various data collection techniques and tools can be employed, ranging from surveys to automated analytical software that tracks trends in threat documentation.
Visualizing threat data through charts, graphs, and dashboards can help distill complex information into understandable formats. Analysis must not only focus on the inherent threat characteristics but also inform decision-making protocols about resource allocation and priority setting.
Integrating manual threat forms into broader risk management frameworks
Integrating manual threat forms within existing risk management frameworks improves overall risk awareness and enables a coordinated response to evolving threats. This integration should align with established threat modeling practices that guide effective risk assessment.
Compatibility with existing tools provides an advantage, as it bridges gaps in current frameworks while ensuring that threat assessments are plugged into larger organizational strategies. Case studies indicate that organizations that have successfully integrated threat forms often show enhanced responsiveness to incidents.
Future trends in threat documentation
The landscape of threat analysis is continually evolving, influenced by technology and changing regulatory requirements. Organizations must stay abreast of these developments, adapting their approaches to documentation and analysis accordingly.
Technological innovations such as artificial intelligence and machine learning are set to revolutionize how manual threat forms are completed and analyzed, offering predictive capabilities that enhance risk mitigation strategies. Regulatory requirements are also expected to change, demanding that organizations proactively update their documentation processes to remain compliant.
Learning from real-world applications
Examining case studies highlighting effective uses of manual threat forms reveals valuable lessons that can be applied across various industries. Success stories showcase how organizations managed to mitigate risks, improve response protocols, and enhance overall safety through diligent documentation and analysis.
Conversely, analyzing notable threat incidents where organizations failed to properly use threat forms serves as cautionary tales. These cases emphasize the critical nature of robust threat documentation practices to safeguard businesses against unforeseen threats.
Interactive tools for enhanced threat analysis
Utilizing interactive tools and platforms can significantly enhance threat analysis, providing organizations with richer data insights and collaborative capabilities. These tools facilitate real-time updates and streamlined cooperation among team members, critical elements in effective risk management.
pdfFiller exemplifies a solution that helps users collaboratively edit and share threat documentation seamlessly across teams. Integrating other complimentary tools provides further analytical depth and efficiency, establishing a comprehensive system for threat management.






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I send analysis of manual threat for eSignature?
Can I create an electronic signature for the analysis of manual threat in Chrome?
How do I fill out analysis of manual threat on an Android device?
What is analysis of manual threat?
Who is required to file analysis of manual threat?
How to fill out analysis of manual threat?
What is the purpose of analysis of manual threat?
What information must be reported on analysis of manual threat?
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.