Information Security Policy Examples Pdf
What is Information security policy examples pdf?
An Information security policy examples pdf is a document that outlines the rules, procedures, and guidelines for ensuring the security of an organization's information assets in digital format. This document helps in setting the framework for protecting sensitive data and preventing unauthorized access.
What are the types of Information security policy examples pdf?
There are several types of Information security policy examples pdf that an organization can create, including but not limited to:
Information Security Policy for Data Protection
Employee Data Security Policy
Network Security Policy
Password Management Policy
Remote Work Security Policy
How to complete Information security policy examples pdf
Completing an Information security policy examples pdf can be done by following these steps:
01
Identify the information assets that need to be protected
02
Define the roles and responsibilities of individuals regarding information security
03
Establish procedures for responding to security incidents
04
Regularly review and update the policy to adapt to changing threats and technologies
05
Use pdfFiller to create, edit, and share the document online for easy accessibility and collaboration.
pdfFiller empowers users to create, edit, and share documents online. Offering unlimited fillable templates and powerful editing tools, pdfFiller is the only PDF editor users need to get their documents done.
Video Tutorial How to Fill Out Information security policy examples pdf
Thousands of positive reviews can’t be wrong
Read more or give pdfFiller a try to experience the benefits for yourself
Questions & answers
What is an example of information policy?
Some examples include providing accurate information, producing and maintaining information that meets the specific needs of the public, protecting the privacy and confidentiality of personal and sensitive information, and making informed decisions on which information should be disseminated and how to distribute it
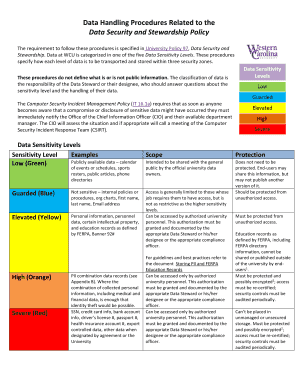
What should be included in an information security policy?
An information security policy should address all data, programs, systems, facilities, other tech infrastructure, users of technology and third parties in a given organization, without exception.
What are the 5 elements of information security policy?
It relies on five major elements: confidentiality, integrity, availability, authenticity, and non-repudiation.
What are the 3 types of security policies?
Security policy types can be divided into three types based on the scope and purpose of the policy: Organizational. These policies are a master blueprint of the entire organization's security program. System-specific. Issue-specific.
What is an example of a information security policy?
It might, for instance, say that remote access is forbidden, that it can only be done over VPN, or that only certain parts of the network should be accessible remotely. Practically every organisation gives its employees user accounts that give them access to sensitive information.
What are information security policies?
An information security policy aims to enact protections and limit the distribution of data to only those with authorized access. Organizations create ISPs to: Establish a general approach to information security. Document security measures and user access control policies.