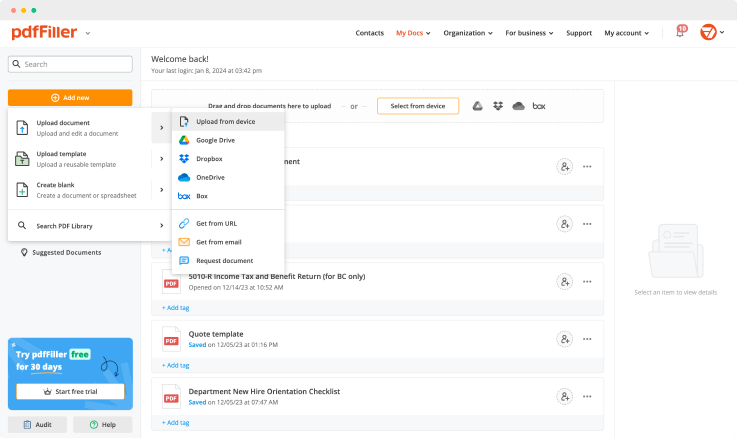
Secure Radio Log Gratis




Join the world’s largest companies









Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution

Unlimited document storage

Widely recognized ease of use

Reusable templates & forms library
The benefits of electronic signatures

Efficiency

Accessibility

Cost savings

Security

Legality

Sustainability
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance

SOC 2 Type II Certified

PCI DSS certification

HIPAA compliance

CCPA compliance
Secure Radio Log Feature
Ensure the safety and integrity of your communications with our Secure Radio Log feature. This tool records all radio transmissions securely, providing you with a reliable way to review and manage your data.
Key Features
Potential Use Cases and Benefits
Our Secure Radio Log feature solves the problem of unreliable or missing communication records. By providing a secure and organized way to log your radio transmissions, you can focus on your core tasks without worrying about lost information. Trust this feature to enhance your communication strategy and keep your operations running smoothly.
Instructions and Help about Secure Radio Log Gratis
Secure Radio Log: simplify online document editing with pdfFiller
The PDF is a popular document format for various reasons. PDFs are accessible on any device, so you can share them between desktops and phones with different screens and settings. You can open it on any computer or phone — it will appear same.
Security is another reason why do we would rather use PDF files to store and share sensitive information and documents. Particular platforms offer opening history to track down people who opened or filled out the document without your notice.
pdfFiller is an online document creating and editing tool that allows to create, modify, sign, and share PDF using one browser tab. This tool integrates with major Arms and allows users to edit and sign documents from other services, like Google Docs and Office 365. Work with the completed document for personal needs or share it with others by any convenient way — you'll get notified when someone opens and fills out the form.
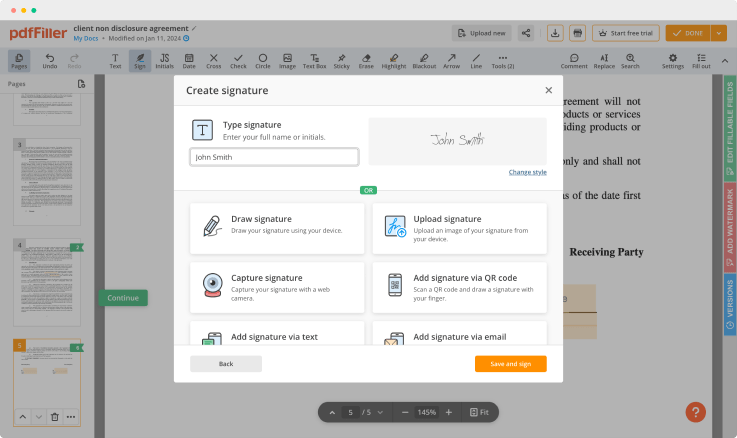
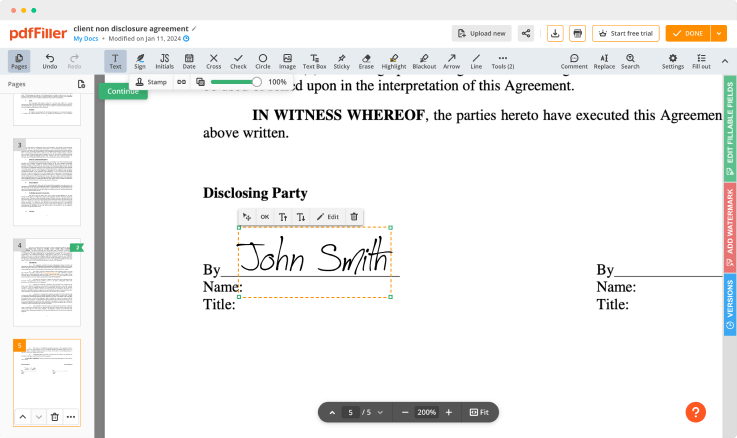
Use powerful editing tools such as typing text, annotating, and highlighting. Add images into your PDF and edit its layout. Change a page order. Add fillable fields and send documents for signing. Collaborate with others to fill out the document. Once a document is completed, download it to your device or save it to cloud.
Get your documents completed in four simple steps:
For pdfFiller’s FAQs
Ready to try pdfFiller's? Secure Radio Log Gratis